
santiago silver - Fotolia
How to perform an ICS risk assessment in an industrial facility
An important step to secure an industrial facility is performing an ICS risk assessment. Expert Ernie Hayden outlines the process and why each step matters.
Managers of major industrial facilities with large footprints -- such as refineries or municipal utilities -- have a challenging enough job just operating and maintaining facilities on a daily basis. When someone from the C-suite reaches out and asks for an ICS risk assessment, it adds to those challenges. What should the manager do? How should they handle such a large task?
Understanding the overall risk assessment process can be useful for security engineers, inspectors, insurance underwriters and general quality assurance/audit staff. It can also be helpful for operations and maintenance personnel who can offer some new perspective on the facility's risk posture.
The key aspect of this methodology is that simply identifying problems and their associated risks is a starting point. It is important to mitigate the identified risks so as not to waste time and resources.
Audit vs. assessment
Some organizations may feel that they don't need another audit. However, an industrial control systems (ICS) risk assessment can be much more useful to a facility manager or executive than an audit.
An audit tends to be compliance-oriented and has more of a pass-fail outcome. An assessment enables admins to use their experience and practical knowledge -- in conjunction with recognized standards and guidelines -- to look for ways to help the customer achieve a higher level of performance and not simply achieve minimum compliance. Gradients of risk can be identified using an assessment.
Additionally, assessments give the customer a sense of their current security reality and risk level. Risk assessments also tend to be more performance-based than a simple pass-fail checklist.
Three primary phases
A high-level view of the ICS risk assessment process is shown below. There are three primary phases: planning and preparation, conducting the assessment, and writing the report.
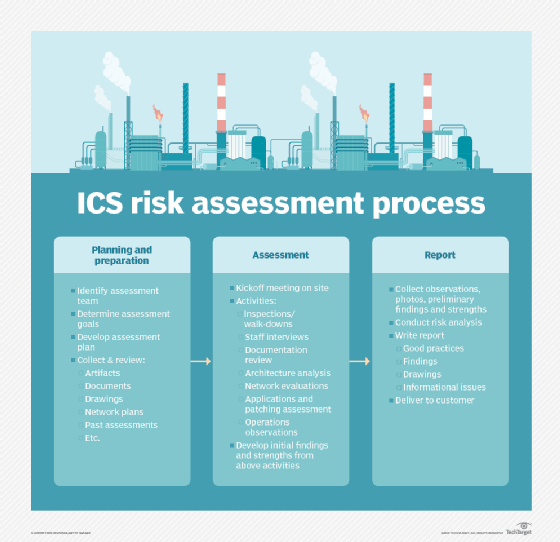
Phase 1: Preparation
Ben Franklin once wrote, "By failing to prepare, you are preparing to fail." This is true for risk assessments. Once you arrive on site and evaluate the task at hand, you can be immediately overwhelmed.
When preparing for an assessment, admins must first understand the desired outcomes and purposes of the assessment. For example, if the site visit is to understand a narrow issue, such as cyber-risk for programmable logic controllers, then it may not be necessary to spend time on the physical security characteristics of the plant. Alternatively, if the assessment is intended to give the customer an overall view of the site's risk posture, perhaps an all-risks perspective is appropriate.
Once you know and understand the desired outcomes and purposes of the ICS risk assessment, make sure your team members are knowledgeable and up to the task. Team sizes can range from one or two members to 10 or more members. Again, the size of your team can depend on the size of the facility, the required team knowledge and the purpose of the review.
Your goals can also be prescriptive or broad. Examples include:
- Documentation reviews
- Architecture and network dissection and assessment
- Staff interviews
- Specific component assessments
- Configuration reviews, such as firewall rule analysis
- Observation of work performed by field operators
- Physical security walk downs
- Port and vulnerability scans and penetration testing
Once the team and site management have established the assessment's goals, they can begin preparation, which can include requesting documentation, such as network diagrams, process flows, select policies and procedures, etc., from the site's staff.
Finally, about two weeks before arriving on site, the assessment team should hold a call or a face-to-face meeting with site management to review the goals, objectives, team members and site visit logistics. This is a great time to identify specific documentation requests to help with assessment preparation and to satisfy the assessment goals.
Phase 2: Conducting the assessment
Performing the on-site ICS risk assessment begins in earnest when the team arrives on site and the first entrance meeting is held with plant management. The entrance meeting is a formal start to the assessment and will normally include key topics such as:
- the introduction of the key participants for both the assessment team and the site;
- the reason for the assessment, goals, objectives and planned/proposed activities each day while on site;
- plans for interviews, note-taking, system/network scanning -- if planned -- visual inspections, system walk downs, photographs, etc.;
- site logistics for the remaining time on site. Don't forget lunch!
Each day, the assessors should spend time on their assigned areas of review. That said, you should ensure the assessors are also aware of their surroundings and can share concerns and best practices with the team and to the plant manager. For instance, if your focus is on control room activities, you should still raise awareness if you notice any physical security deficiencies on the site perimeter when transiting to the control room.
The assessors will need to conduct interviews as part of the assessment process. Interviews are intended to obtain information from site personnel regarding site operations, security and methodologies. Becoming an effective interviewer takes practice -- don't expect to be a premier interviewer immediately. A new interviewer should have excellent resources available to help.
Team members should document facts and perspectives that the team leader can use to build a comprehensive report. One technique is to write an observation at the end of each day including the key events observed, strengths, deficiencies and suggestions for improvement. Writing this mini-report at the end of a long day may seem onerous, but it is a great way to capture fresh thoughts rather than putting it off until a few days later when the details are a bit fuzzy.
On the final day on site, it is customary to hold an exit meeting to review the identified strengths, concerns and other informational points. This meeting's primary focus is to offer a summary review of the actions taken and the sites/facilities visited during the assessment. Then, the team can review any strengths or areas that need improvement. The meeting should be a dialogue, as some topics may be matters of opinion rather than just pass-fail compliance topics.
Following this review, the team leader should go through the next steps for report development and delivery with the site manager.
Phase 3: Writing the report
Writing the ICS risk assessment report is more than a trivial exercise; it is a very important way to document the team's perspective of the site's risk profile and should include both positive and negative elements.
When reviewing all of the team's observations, notes, pictures and daily meeting conversations, you must assign relative risk levels to each finding. Don't forget that the intention of the risk assignment is to not only identify the seriousness of the concern, but also to assist the site manager to take care of higher risk issues.
Finally, the report should recommend actions to correct the findings. The intention here is to help the site manager to solve the problem.
This is a high-level review of the risk assessment process. Each risk assessment is unique and has its nuances. Overall, though, the process is basically the same. Risk assessment activities can be documented to identify different techniques, approaches and tools teams can use to accomplish a successful review.







