How to perform a data risk assessment, step by step
Organizations need confidence that they are properly identifying and protecting sensitive data. Follow these five steps to create a data risk assessment.
Most enterprises today count sensitive data among their most valuable assets. That includes everything from personal records to intellectual property and other proprietary information.
Every organization needs to safeguard the security and privacy of its sensitive data to avoid data breaches, intellectual property theft and other compromises that may result in fines, lawsuits and -- in the worst case -- business failure.
What is a data risk assessment and why is it important?
A data risk assessment is a review of how an organization protects its sensitive data and what improvements might be necessary.
Organizations should perform data risk assessments periodically, as a form of audit, to help identify information security and privacy control shortcomings and reduce risk. A data risk assessment is also necessary after a data breach, whether intentional or inadvertent, to improve controls and reduce the likelihood of a similar breach occurring in the future.
5 steps to perform a data risk assessment
Use the following five steps to create a thorough data risk assessment.
1. Inventory sensitive data
Check endpoints, cloud services, storage media and other locations to find and record all instances of sensitive data. A data inventory should include any characteristics that might influence risk requirements. For example, the geographic location of stored data affects which laws and regulations apply.
This article is part of
What is data security? The ultimate guide
Identify who is in charge of each instance of sensitive data so you can interact with them as necessary.
2. Assign data classifications to each data instance
Every organization should already have defined data classifications, such as "protected health information" and "personally identifiable information," for all sensitive data. These definitions should indicate which security and privacy controls are mandatory and recommended for each sensitive data type.
Even if data already has a classification, recheck it periodically. The nature of data can change over time, and new classifications may emerge that apply to the data in question.
3. Prioritize which sensitive data to assess
An organization may have so much sensitive data that it is not feasible to review all of it during each assessment. If necessary, prioritize the most sensitive data, the data with the most stringent requirements or the data that has gone the longest without assessment.
4. Check all relevant security and privacy controls
Audit the controls protecting sensitive data where it is used, stored and transmitted. Common audit steps include the following:
- Verify the principle of least privilege. Confirm that only the necessary human and nonhuman users, services, administrators and third parties -- e.g., business partners, contractors and vendors -- have access to sensitive data and that they have only the access they require, such as read-only, read-write, etc.
- Ensure all policies restricting access to data are actively enforced. For example, an organization might limit access to certain sensitive data based on the following factors:
- the location of the user
- the location of the data
- the time of day
- the day of the week
- the user's device type
- Ensure all other necessary security and privacy controls are in use. Common tools to mitigate risk include the following:
- data loss prevention software
- firewalls
- encryption
- multifactor authentication
- user and entity behavior analytics
- Identify data retention violations. Determine if any data is present that should be destroyed to comply with data retention policies.
5. Document all security and privacy control shortcomings
While identifying security and privacy deficiencies is within the scope of a data risk assessment, fixing them is not. It's reasonable, however, for an assessment to include the following:
- a relative priority level for each deficiency
- a recommended course of action for addressing each deficiency
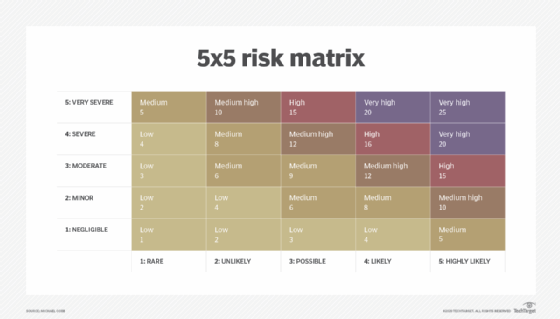
These recommendations ideally inform a roadmap toward better data security. A risk matrix can help organize and prioritize issues according to the severity of their potential consequences and the likelihood they will occur.
How to use data risk assessment results
Enterprise leaders should formulate a strategy to mitigate the security and privacy shortcomings uncovered in the data risk assessment, taking into consideration remediation recommendations and prioritizing high-risk issues.
Ultimately, the output of a data risk assessment should be a major input to an organization's risk management and mitigation program, enabling more informed decision-making that helps improve data protection.








