
Sergey Nivens - Fotolia
How to maintain digital privacy in an evolving world
Protecting a user's digital privacy across different technologies requires a plethora of tools. Expert Matthew Pascucci explores the different ways to protect sensitive data.
Digital privacy is a topic that's continually evolving, and, in turn, so are the tools aimed at protecting privacy in a digital age. As businesses, governments and social media outlets continue to vie for control and the tracking of personal data, we need to understand the risks of being in an interconnected world and the tools that can be used to defend us. While living in a digital age, there are numerous ways for someone's privacy to be slowly leaked away without notice, and the aim of this tip is to educate people on the risks and of the tools that can be used to prevent the unwanted disclosure of personal data.
Web browser security
The first area that's important to review is how to protect digital privacy while using a browser. These portals into the web allow businesses and governments to gather an individual's data via numerous methods, some of them without the user's consent. Controlling the user information leaked from a browser is the first place to start when looking to tighten privacy on the internet.
There are many browsers available to access the web, but from a privacy and functionality standpoint, Mozilla Firefox is particularly customizable, and has privacy add-ons that help to limit exposure. There are also dedicated privacy browsers, like WhiteHat Aviator, Brave or Epic, but, sometimes, functionality can become an issue with them. Configuring Firefox with specific plug-ins allows users to reach an adequate layer of security and privacy while not using the Tor browser.
In regards to the privacy add-ons in Firefox, there are numerous options to select from to harden the browser from leaking private data. There are add-ons that monitor the connections of the browser and block tracking cookies, such as Lightbeam, Privacy Badger and Ghostery, which limit the information a business stores on an individual after they leave their site. With this in mind, there's also an add-on called BetterPrivacy, which prevents super cookies and zombie cookies from lingering on a system. Outside of tracking cookies, there are tools like NoScript, which blocks malicious scripts from loading in the browser; Adblock Plus, which limits or removes ads which target users; and SSleuth, which rates the security of the encryption being used in transit.
Without downloading add-ons to Firefox, there are numerous native changes that can be made to the browser itself that allow you to configure privacy-related settings. A few ways to do this include adjusting about:config in the address bar (research this in detail before making changes); selecting DuckDuckGo or, better yet, StartPage as the default search engine; and enabling Do Not Track. There's a privacy section within the options of Firefox where users can configure their privacy to an acceptable level.
Email privacy
Email is another vector of digital privacy that needs regulation, and webmail services, such as Gmail and Yahoo Mail, put privacy at risk. These services are free for a reason, and their privacy policies show that the users are not the customers, but the products. Data advertising is based on the content of a user's email and who has access to the user's data, which is concerning. Hosting email on an alternative provider, like ProtonMail or Runbox, allows for additional encryption, off-site hosting in European countries with strict privacy laws and the elimination of third parties using your data for advertising. There are many other privacy-focused email hosting services that offer email destruction services after a message hits a particular timeframe, and there are options available for anonymity, as well.
If hosting email on one of these providers isn't possible, users should consider using their current mail provider with GNU Privacy Guard installed in the mail client, so as to interact with others in a secure and private manner. This doesn't have to be for every message, but if something sensitive needs to be over standard mail providers, it's recommended to do so in an encrypted manner using similar tutorials.
Messaging services privacy
Communicating with people is what makes the internet so powerful, and protecting the privacy of chat and text messages is important. These forms of communication have become the de facto standard of communicating today, especially in the mobile age. Because of this, these messages need to be protected while in transit and in storage. By default, Apple encrypts all iMessages, but that doesn't particularly make them trustworthy. Using chat apps, like WhatsApp, Telegram, Pidgin with the Off-the-Record plug-in and Signal, allows for open source applications with encryption built into their core, so they can manage the encryption keys. These and other programs offer additional privacy-related features, like passphrase app locking, which adds an additional layer of protection while being utilized on a mobile device.
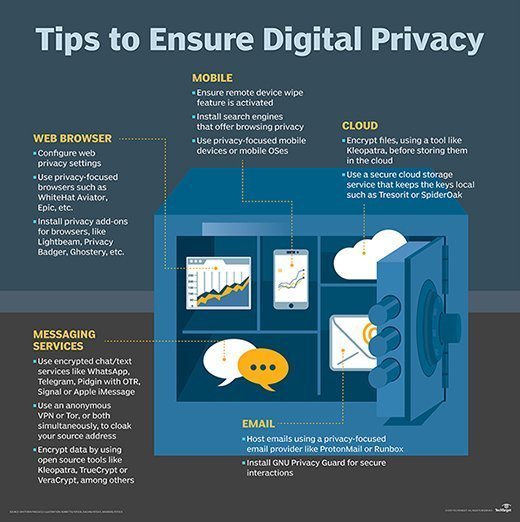
Secure communications don't stop at chatting/texting. Utilizing an anonymous VPN or Tor -- or, even better, using both simultaneously -- will cloak the source address information and allow private access to the internet. Tor and encryption are cornerstones in privacy and digital freedom on the internet, though it's important to note that Tor doesn't offer complete, foolproof anonymity.
Encrypting data at rest is also something that needs to be considered. By default, both Android and Apple encrypt mobile devices out of the box. There are also open source tools, like Kleopatra, TrueCrypt and VeraCrypt, to encrypt partitions, volumes or containers on workstations. With TrueCrypt and other variants, users can install decoy/hidden operating systems at startup to dissuade anyone from attempting to physically access the operating system. There's also a bootable operating system called Tails that runs at startup via USB/CD, and which uses Tor and many of the previously mentioned tools without using the hard disk in the workstation.
Mobile privacy
Mobile devices and the apps that run on them now hold a lot of personal data on one device. Not only that, but the device is also recording phone calls, saving texts, storing pictures, preserving browsing history and, most importantly, tracking the user's every physical move with GPS. These devices are a privacy nightmare, and locking them down can be difficult. Using apps that assist with remote wiping a lost device; installing apps like Signal for texting, DuckDuckGo for browsing and others; and disabling GPS on the phone is a good start. There are also apps like RedPhone that encrypt calls to users that also use the app.
There are also phones that are specifically created to deal with the threats of privacy in the mobile age, such as Blackphone or the Android OS variant called Cooperhead, which take a privacy-first approach when it comes to mobile devices. However, the apps on these devices allow for too much access to data that they do not need to function. Using sites like www.privacygrade.org can help users get an understanding of how these apps run on their mobile device, as well as rank the apps based on privacy.
Cloud privacy
The storage of user data on cloud services is also important. Many online storage features allow third parties to search files stored on their platform. To protect against this, users can either encrypt the files first with a tool like Kleopatra, or use a secure online storage service that keeps the keys locally, like Tresorit or SpiderOak.
There are many reasons to harden digital privacy with technology. December 2016 brought about legislation -- Rule 41 in the U.S. and The Draft Communications Data Bill (or Snooper's Charter) in the U.K. -- that increases the government's access to dissidents' and journalists' reporting from oppressive regimes, as well as the standard citizen, who doesn't want their private information handed out to businesses without their knowledge. Using these tools and following the work of digital privacy advocacy groups, like the Electronic Frontier Foundation and Privacy International, will help safeguard privacy in the digital age.








