
juanjo tugores - Fotolia
How to conduct a security risk review on a large building
Assessors cannot dive into a security risk review of a large building; they have to prepare and strategize ahead of time. Learn how to get ready for this type of security assessment.
Imagine you are a risk analyst or CISO and have been assigned the task of conducting a cyber and physical security risk assessment of a 30-plus-story building in the middle of a major city. Before you begin, it's important to familiarize yourself with foundations for planning and performing such a review with some ideas on where to start, where to focus and why.
A new way to look at building services
A fundamental approach to a security risk review of a large building is to consider the primary services supporting the building. Such services include:
- electricity
- industrial controls
- IT/communications
- waste/waste treatment/sewer
- water
You can develop a hierarchy of importance of these infrastructure systems that can help guide your facility review sequence.
The five factors listed above are of foundational importance to the operation and resilience of the facility and provision of a safe, comfortable environment for customers, residents, visitors, contractors, vendors and employees. The degradation of any of these services can lead to some negative effects on the commercial facility and its occupants.
Using the interdependencies analysis outlined in the white paper "Identifying, Understanding and Analyzing Critical Infrastructure Interdependencies" by Steven Rinaldi, James Peerenboom and Terrence Kelly, you can develop a building analysis approach for the security risk review.
Based on the analysis hierarchy, the first area to focus on for both physical security assessments and cybersecurity scrutiny is the electric systems, including components and controls. The electric systems power the water systems/infrastructure, waste water systems, IT/communications and industrial controls. Therefore, the first critical systems to evaluate are electric supply and distribution because of their fundamental support of all other structures and control schemes.
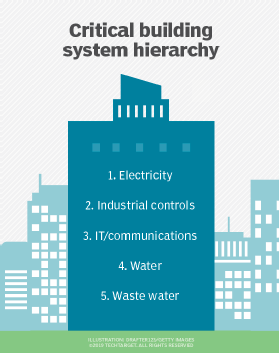
Also, even if you have emergency electric power/backup, loss of primary power will immediately cause degraded performance of most, if not all, building systems. With some analysis of the different systems and their resilience to system failure, the hierarchy of the building systems is as shown in this figure.
While this approach may not be perfectly tiered, it can provide a good start on your building walk-down and activity prioritization. As Rinaldi observed, loss of electricity can lead to first, second, third and nth order effects on other systems.
Gathering data before the security risk review
Walking into a building for a security risk review without some preparation can be daunting. You need to work with the building owner or maintenance staff to collect some basic drawings and system data. Asking for the following information and reviewing it before you arrive on-site will help you prioritize your system and floor reviews:
- Copies of building floor plans from roof to basement
- One-line diagrams
- electric power (normal and emergency);
- building management system (BMS) controls network;
- IT and telecom communications;
- potable water systems;
- fire protection and water systems; and
- waste water.
- Network hardware
- brand and model of BMS controllers and
- brand and model of routers and network switches in the building.
- Procedures for taking manual control of building subsystems, such as heating, cooling, lighting, elevators, etc., to maintain operations
- Procedures and legends for color-coding cables and pipes in the building
- Written security plan for the building (physical and cyber)
- Written security procedures
- access control -- keycard assignment and retrieval;
- brand and model number for keycard systems
- access control -- username, password assignments;
- cyber incident response;
- physical incident response;
- personal security policies and procedures;
- prehire procedures, especially regarding screening;
- termination procedures/checklists;
- key control/key management procedures;
- What brand are the building keys?
- remote access to building systems/components;
- roof access procedures;
- active shooter procedures;
- fire/emergency response procedures; and
- Wi-Fi system -- access control, management and architecture.
- access control -- keycard assignment and retrieval;
- Copies of past written security/risk assessments
- Closed-circuit TV (CCTV)
- Policies, procedures, network diagrams for CCTV;
- Vendor name(s) and contact information; and
- Processes for recordings and handling same for evidence.
- List of all vendors with remote access to building controls
This is just a sample list of topics and ideas for the data request. With more time, the assessor can develop more questions and requests; however, you will find that starting with this top 10 is a good starting point.
Developing a plan of attack
You are still not ready to commence your site inspection and security risk review. Instead, you need to understand the building before you begin -- almost to a floor-by-floor familiarity -- to help guide your activities during your finite amount of time.
For large buildings, you need a collection of building elevation drawings showing key systems and controls on each floor. By reviewing each floor on each elevation drawing and floor-by-floor tactics, you can identify key components, systems and controls to each level.
With that, you can develop a floor-by-floor plan of attack. An example of such a plan is shown below:
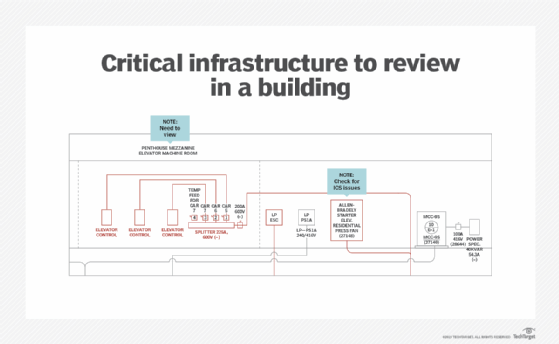
The plan should include a list of key floors because not all floors contain critical systems and not all floors are of operational importance for the building operation and security. The plan should also include a review of each key floor, collecting the different elevation drawing elements onto a single page for that floor. The example above is for a specific floor and its associated mezzanine. You can add notes to identify key systems, rooms and devices that need to be inspected and analyzed.
With this in hand, you are ready to do the on-site inspection.
Editor's note: This is part one of a two-part series. You can read part two here.







