How to conduct a cybersecurity audit based on zero trust
This checklist offers guidance on how to prepare for a zero-trust cybersecurity audit and helps document how well cybersecurity controls are performing based on CISA's ZTMM.
The CISA Zero Trust Maturity Model is a framework for organizations in the public and private sectors designed to strengthen efforts to prevent unauthorized access to technology infrastructure and information resources.
Developed by the U.S. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA), the Zero Trust Maturity Model (ZTMM) is relatively new and is among many other similar maturity models that address cybersecurity.
Organizations will need to conduct cybersecurity audits at some point, especially with the CISA ZTMM and other zero-trust frameworks gaining momentum as organizations adopt zero-trust methods and guidance, and as the government begins to mandate the use of zero trust.
Why zero-trust cybersecurity maturity audits are important
To maintain zero trust, policies and procedures must be proactively managed. Failure to perform periodic reviews of cybersecurity plans and procedures, as well as failing to regularly test those resources, can increase the risk of unauthorized cyber attacks.
Audits of zero-trust compliance are an essential part of an organization's efforts to comply with zero-trust models and related cybersecurity standards. They provide objective assurances that organizations have policies, procedures, trained staff, educated employees and supportive senior leadership. Audits also show that organizations have established formal controls to ensure they comply with guidelines and specifications. Lastly, audits ensure IT infrastructure is performing securely -- and, if not, they ensure anomalies can be quickly identified and corrected.
Zero-trust controls for audit investigations
The ZTMM document follows the seven baseline criteria of zero trust as defined in NIST Special Publication (SP) 800-207 (2020), Zero Trust Architecture, all of which can be considered controls themselves. Each control can be expanded, however, into more detailed controls that address aspects of the baseline criteria.
For example, the third criteria states, "Access to individual enterprise resources is granted on a per-session basis." The following are supplementary controls that can support the baseline control as part of an audit investigation:
- Access to organizational resources is defined by a policy.
- Access to organizational resources is governed by a series of procedures.
- Access to all resources is based on an individual employee's need to know.
- Access to resources is based on an employee's role in the organization.
- Access to resources is granted on a per-session basis, based on the employee's role and need to know.
- Completion of a session terminates further access to resources unless a new session is initiated.
- Access to resources is granted via a multistep process that includes a user ID and multifactor authentication (MFA).
- No more than three unsuccessful access attempts can be made before access is denied and must be reinstated by a security administrator.
- User access passwords must be updated every 60 days.
- User authentication methods must be reviewed every six months and updated as needed.
Best practices for zero-trust audit preparation
The most important elements for audit preparation are overall preparation and documentation. These steps include the following:
- Secure management approval and funding for the audit.
- Establish an audit team to interact with the auditors.
- Assess the auditors' capabilities and experience in terms of auditing cybersecurity issues.
- Understand the zero-trust model.
- Understand relevant cybersecurity standards and best practices.
- Prepare an audit plan.
- Secure hard-copy and electronic evidence, including policies and procedures; cybersecurity plans; screenshots of various cybersecurity functions; records of various activities, such as patching and updating firewall rules; and reports of system tests.
- Provide copies of previous assessments, audits and other analytical reports.
- Provide a work area for auditors.
CISA Zero Trust Maturity Model audit checklist
Within the ZTMM document are details on activities that can be addressed as organizations evolve their zero-trust capabilities through three specific stages -- traditional, advanced and optimal -- using five pillars of zero trust development: identity, device, network/environment, application workload and data.
The following checklist provides a high-level look at suggested audit controls and examples of evidence using the ZTMM as a basis. The three stages and five pillars are built into the table.
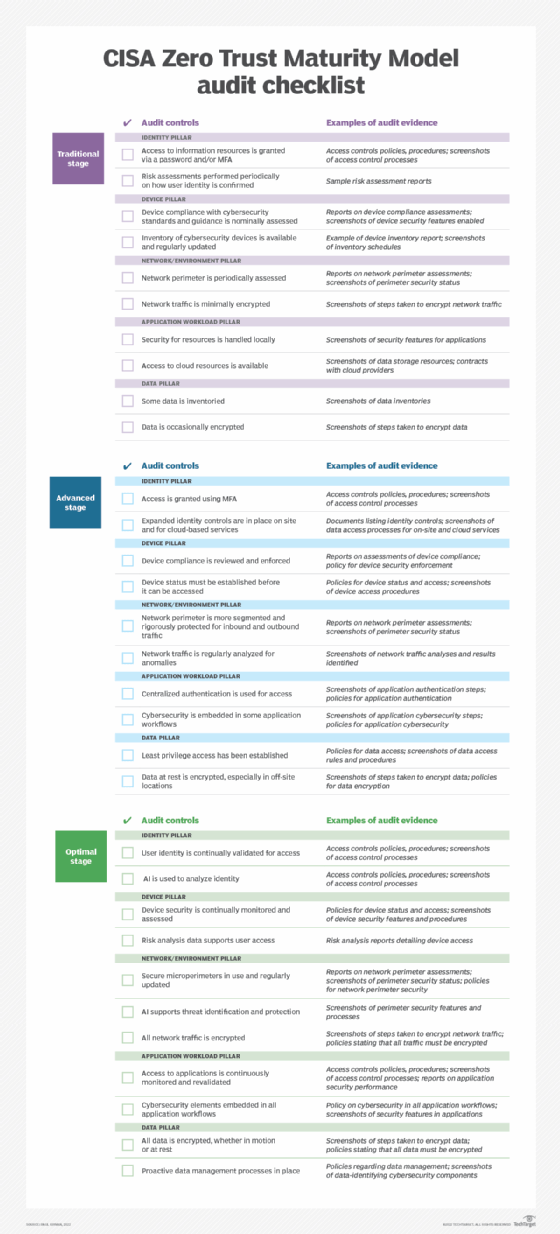
Download a copy of the CISA ZTMM checklist here.






