How to calculate cybersecurity ROI for CEOs and boards
Calculating and communicating cybersecurity ROI can help persuade top management to invest. Here's how to use meaningful, concrete metrics that resonate with business leaders.
Everyone knows we need cybersecurity. But whether they admit it or not, businesses don't always want to pay for it. Too often, the C-suite sees security as a cost center, making it difficult for CISOs to secure funding for new tools and initiatives.
While cybersecurity doesn't directly drive revenue, it does maximize business continuity, protect the organization's reputation and ensure regulatory compliance. By calculating cybersecurity ROI, CISOs can translate this value into a business context that resonates with CEOs and boards.
Understanding cybersecurity ROI
Financial experts typically define ROI as the income directly resulting from an investment, less the cost of the investment and expressed as a percentage.
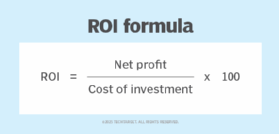
For example, consider a $1,000 investment that resulted in $100 of income. The ROI would be 10%, or a 10-cent return for every dollar invested.
But security controls don't directly lead to revenue. Rather, they protect revenue by reducing cyber-risk. That's why cybersecurity ROI has a looser definition than traditional ROI: It refers to direct and indirect financial benefits of a cybersecurity investment, including loss avoidance, risk reduction, time saved and money saved.
What is ROSI?
Some cybersecurity leaders prefer the term return on security investment (ROSI), which provides a more precise metric to evaluate cybersecurity investments.
There are multiple ways to calculate ROSI. The traditional ROSI formula incorporates a figure known as annual loss expectancy (ALE), the anticipated yearly financial costs of a given security risk. ALE is calculated by multiplying the annual rate of occurrence (ARO) by the single loss expectancy (SLE).

For example, if an organization has experienced a given type of security incident twice a year, the ARO would be 2. If the organization expects to lose $5,000 in direct and indirect costs each time such an incident occurs, the ALE would be $10,000.
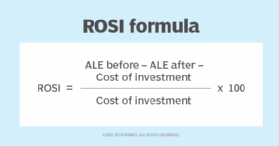
Calculate ROSI as a percentage by subtracting the cost of the security investment from the difference in ALE -- before and after the investment -- divided by the cost of the investment and multiplied by 100.
Say an organization invested $2,000 in a security measure to address the above security incident, which occurred twice per year and cost the organization $5,000 each time. Imagine that after the investment, the incident occurred only once per year, resulting in a new ALE of $5,000. Using the above formula, calculate the ROSI as follows:
ROSI % = ((10,000 – 5,000 – 2,000) / 2,000) × 100 = 150%
Based on this calculation, for every dollar invested, the organization avoided $1.50 in losses.
An alternative ROSI formula includes a mitigation ratio (MR), which refers to the percentage of risk the security investment could mitigate.
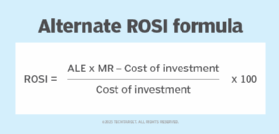
This equation is useful for evaluating products or controls, for example. Say an organization's ALE for 100 phishing attacks per year, at $5,000 an attack, is $500,000. A CISO is evaluating an $80,000 anti-phishing tool that claims it prevents 99% of phishing attacks. Calculate the ROSI as a percentage by subtracting the cost of the investment from the ALE multiplied by the MR, divided by the cost of the investment and multiplied by 100:
ROSI % = (((500,000 × .99) – 80,000) / 80,000) × 100 = 519%
Based on this calculation, for every dollar invested, the organization could avoid $5.19 in losses.
Cybersecurity ROI challenges
Whether a CISO uses the term cybersecurity ROI or ROSI, calculating the value of a cybersecurity investment presents clear challenges:
- Loss avoidance relies on estimates. It's impossible to prove that a given loss would have occurred or will occur in the future without a cybersecurity measure in place. At best, a CISO can make a compelling case that it would have likely occurred or will likely occur, based on historical internal data, industry benchmarks and cyber-risk quantification metrics.
- Business leaders often view cybersecurity as a cost center. Because the goal of cybersecurity is to mitigate risk rather than drive revenue, some CEOs and board members still view it as a cost center. The CISO's challenge is to convincingly demonstrate that security controls either increase efficiency -- thus saving time and money -- or protect the business's ability to generate revenue.
How to calculate cybersecurity ROI
Finding compelling metrics for cybersecurity ROI calculations can be difficult. Consider using a reputable cyber-risk quantification framework, such as the FAIR model, which helps CISOs translate cyber-risk scenarios into financial terms, taking into account event likelihood and both direct and indirect losses.
Plenty of data also exists in the typical security environment that a CISO can use to make convincing and compelling cybersecurity ROI or ROSI calculations. For example, it is a straightforward process to examine log files to see if the number of security events has declined since the implementation of a given tool, service or strategic initiative.
Trouble ticketing software offers valuable insight as well. It captures how long it takes to address problems and tracks the effectiveness and productivity of security personnel who solve those issues. If an investment helps staff solve issues more quickly, it's possible to translate time saved into dollars saved.
Examples of cybersecurity ROI calculations
Let's say a security analyst makes $100,000 annually. If a given tool or service saves an hour of that employee's time, then the business saves $48. Similarly, if a security analyst managed 100 tickets a month and can now handle 200 tickets a month, that represents a 100% increase in efficiency -- the equivalent of one full head count.
Productivity is also measurable through systems integration -- i.e., the merging of networking information with security information. This yields quicker root cause analysis, which can be calculated as the percentage change in events detected over time, which can then be factored in terms of head count reduction.
If an organization with a security IT staff of six deployed security software that boosted efficiency by 25%, the company could reduce that staff by 1.5 and still get the same productivity. Assuming a fully loaded labor cost of $125,000 per employee, the company could save about $180,000 by eliminating those positions. If the security software costs $90,000, the time to recoup the investment cost would be just six months.
Executives also readily understand how important it is to avert any disruption to the business, so consider calculating increased uptime as it relates to money generated by the business. A $100 million enterprise, for example, brings in about $275,000 a day, or $11,000 an hour. By using direct measurements like this, CISOs can directly calculate the value of reducing downtime from security-related IT outages.
How some cost-avoidance metrics hurt CISO credibility
While CISOs might be tempted to use cost-avoidance metrics derived from high-profile security incidents or industry averages to calculate cybersecurity ROI or ROSI, doing so risks hurting credibility with business leaders.
For example, an oft-cited statistic is IBM's average cost of a data breach, which reached $4.88 billion in 2024. While this figure could inform compelling and productive discussions with business executives about cyber-risk scenarios and the organization's risk appetite, it is too broad to use in a realistic ROI calculation.
Similarly, avoid relying on the following cost-avoidance metrics.
High-profile security incidents
A CISO might say, "Because I installed tool X, we didn't suffer a ransomware attack, which saved us from paying a $10 million ransom like our competitor recently did." CEOs and boards are likely to dismiss this reasoning as flimsy and imprecise -- it's impossible to prove a negative -- and the hypothetical cost dodged as vague and variable, at best. The only executives likely to buy this argument are the ones who have already personally experienced such massive losses themselves. For better or worse, those executives are probably not the ones now in charge.
Reputational damage
Reputational costs are nebulous. Estimating the damage from a publicized security incident might be a worthwhile exercise for cyber-risk scenario analysis or cyber-risk appetite discussions, but it is not necessarily a credible way to calculate cybersecurity ROI in a different instance or at another organization.
Consider the 2020 SolarWinds breach. The company suffered a loss in market capitalization of more than $1 billion in a matter of days. But there is no way to use this figure to directly calculate the value of averting another security vulnerability at another company. In other words, not every organization that experiences a breach will lose $1 billion in market capitalization. Each organization has its own unique reputational stakes, with potential costs varying from incident to incident.
Regulatory fines
Like reputational damage and other indirect costs, hypothetical regulatory fines are similarly difficult to estimate. For example, average PCI DSS noncompliance fines range from $5,000 to $100,000. But in the instance of the 2008 Heartland breach, the payment processor paid nearly $110 million in fees to Visa, MasterCard, Discover and American Express, plus additional legal fees.
CISOs would be hard-pressed to meaningfully quantify compliance risk by comparing their businesses with other companies that have paid penalties for regulatory mistakes, as each situation and exposure is different.
How to communicate cybersecurity ROI to executive leadership
Executive managers care about security, even if only tangentially, in that they care about the business risks security threats create. Their focus is on how security tools might mitigate those risk levels.
When communicating cybersecurity ROI to executives, CISOs should consider the following:
- Use clear, concise language -- not security speak. Avoid using technical jargon or sharing tactical and operational details when communicating the value of cybersecurity to business executives. In other words, no discussions about the mechanics of RSA encryption or lectures on how quantum superpositioning obviates hashing functions.
- Speak in business terms, aligning with investments and business needs. Highlight how specific investments in people, processes and technology mitigate critical business risk factors and ensure maximum profitability.
- Use visual aids. Provide visuals such as graphs, charts and infographics to illustrate ROI data.
- Build a narrative. Use storytelling to build a coherent cybersecurity ROI narrative, focusing on how security spending optimizes the business's ability to generate revenue.
- Complement cybersecurity budget requests with cyber-risk discussions. In addition to cybersecurity ROI calculations, present the CEO and board with cyber-risk scenarios and cyber-risk appetite analysis, further contextualizing security spending in business terms.
- Don't talk about eliminating risk. Never talk about eliminating risk, which is an impossible expectation to meet. Rather, highlight risk-based security investments that have a direct effect on the bottom line. The more that security managers can focus on business prerogatives and risk management, the more they will win the understanding and support from the business leaders who depend on them.
Jerald Murphy is senior vice president of research and consulting with Nemertes Research. With more than three decades of technology experience, Murphy has worked on a range of technology topics, including neural networking research, integrated circuit design, computer programming and global data center design. He was also the CEO of a managed services company.
Alissa Irei is senior site editor for Informa TechTarget.





