Maxim_Kazmin - Fotolia
How does BGP hijacking work and what are the risks?
The lack of security protections in BGP means that route hijacking can be easy, especially for organized crime or state-backed threat actors. Here are ways to deal with it.
No matter what you call it -- prefix hijacking, route hijacking or IP hijacking -- BGP hijacking is when a router improperly advertises itself as having the most efficient route to a victim network.
Border Gateway Protocol route hijacking, both malicious and inadvertent, has long been an inherent risk when using the internet backbone routing protocol. And because the protocol was originally designed without security protections, BGP routers can be subject to some troubling attacks.
During BGP hijacking, the BGP backbone routers advertise themselves as providing the best routes to affected networks and then redirect traffic intended for those networks. While many such incidents are caused by malicious actors, inadvertent BGP hijacking caused by misconfigurations can be hard to differentiate from malicious cases.
When a route has been maliciously hijacked, internet backbone routers direct traffic intended for the affected route to a different network controlled by attackers. Such attacks are used when an attacker wants to gain access to data stored in the targeted network, to harvest authentication tokens or to take over user accounts hosted on the affected network.
One recent BGP hijacking incident targeted a network hosting a cryptocurrency exchange. The Amazon Route 53 incident enabled attackers to steal cryptocurrency from unwitting victims who were trying to log into their exchange accounts. In that attack, hackers stole approximately $150,000 worth of cryptocurrency from MyEtherWallet.com customers.
How BGP hijacking works
BGP is an older internet protocol that was first used in the 1980s and was designed to enable internet backbone routers to advertise the default routes for the major networks served by the backbone providers.
These networks, also known as autonomous systems, or ASes, are operated by organizations that provide access to backbone internet services, like telecommunications companies and cellular service providers. An AS is a group of networks that share the same backbone routes, such as networking or telecommunications companies that provide network access to different organizations.
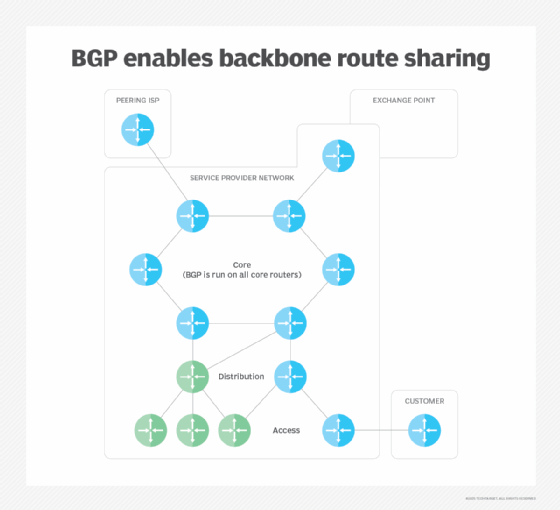
Local routing can be administered from within an enterprise, but when a user needs to access a host outside of the enterprise, the enterprise's internal routing tables direct that network traffic to exterior or backbone routers running BGP. These routers advertise routing tables to the ASes they serve.
BGP hijacking occurs when an AS improperly advertises itself as providing a route to a particular set of network addresses. Inadvertent hijacks caused by accidental misconfigurations may be difficult to differentiate from malicious BGP hijacks, but the effect is the same: Network packets are routed to incorrect destinations.
Defending against BGP hijacking attacks
For organizations that don't maintain their own AS routing infrastructure, defending against BGP hijacking is a matter of choosing service providers that actively defend against such attacks. The only useful tactic for these organizations is to actively monitor externally routed traffic, but this method may not be cost-effective.
Other strategies for defending against BGP hijacking include:
- using IP address prefix filtering to block inbound network traffic from networks known to be controlled by malicious actors; and
- deploying BGP hijacking detection strategies at the AS level, where operators can monitor network latency, performance and failed packet deliveries to identify BGP hijack attempts.
Border Gateway Protocol Security (BGPsec) is an extension of the BGP protocol that is intended to add cryptographic verification for advertised BGP routes. BGPsec, an internet standards track protocol, provides a mechanism for backbone routers to apply digital signatures to their route update advertisements, making it more difficult for unauthorized attackers to improperly advertise routes for ASes. BGPsec can also help reduce the potential for complications when BGP routes are improperly advertised due to misconfigurations.








