
alphaspirit - Fotolia
Guide to identifying and preventing OSI model security risks: Layers 4 to 7
Each layer of the Open Systems Interconnection presents unique vulnerabilities that could move to other layers if not properly monitored. Here's how to establish risk mitigation strategies for OSI layer security in Layers 4 through 7.
Cybersecurity personnel must understand the Open Systems Interconnection layers because hackers can easily pivot from layer to layer when exploiting computing system vulnerabilities. In part two of this two-part tip, contributor Daniel Allen continues his examination of OSI model security risks by identifying vulnerabilities for each layer as well as the necessary steps to mitigate each.
Layer 4: The Transport layer
Layer 4 is responsible for the packetization of data. It delivers packets of information error-free without observing any losses or duplication. Most applications running on the internet use services that are provided by the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
OSI layer vulnerabilities:
- Mishandling of undefined, poorly defined or "questionable" conditions.
- Differences in transport protocol implementation allow enumeration of host information. Overloading of transport-layer mechanisms such as port numbers limit the ability to effectively filter and qualify traffic.
- Transmission mechanisms can be subject to spoofing and attacks based on crafted packets and the educated guessing of flow and transmission values, allowing the disruption or seizure of control of communications.
- SYN flood, Smurf attack.
OSI model security and compliance strategies:
A typical strategy for Layer 4 OSI model security involves stopping DDoS attacks through Blackholing, a method employed by the internet service providers to stop any DDoS attack that a customer experiences at the Transport layer. Unfortunately, this approach stops all traffic (malicious and legitimate) from getting into the system.
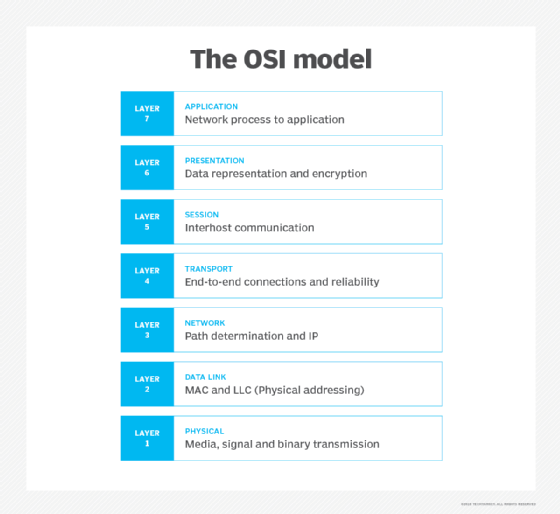
Layer 5: The Session layer
The Session layer is responsible for establishment, coordination and termination of sessions. In case there is any interruption in between the session process, this service reviews the authentication and reconnects the layers together. TCP and UDP use this service when working with applications.
OSI layer vulnerabilities:
- Telnet DDoS-attacker exploits a flaw in a Telnet server software running on the switch, rendering Telnet services unavailable.
- Weak or nonexistent authentication mechanisms. Passing of session credentials such as user ID and password in the clear, allowing intercept and unauthorized use. Session identification may be subject to spoofing and hijack.
- Leakage of information based on failed authentication attempts. Unlimited failed sessions allow brute-force attacks on access credentials.
OSI model security and compliance strategies:
The only way to resolve this vulnerability is to keep hardware up to date. Hardware manufacturers issue version updates or patches, which enable users to mitigate the vulnerability.
Layer 6: The Presentation layer
The Presentation layer is known as the Translator, and is the part of the OS that translates the data from the source format into a common format and then sends it to the receiver, and vice versa. It uses the layer of compression and encryption during the transaction of information between users.
OSI layer vulnerabilities:
- Malformed Secure Sockets Layer requests, inspecting SSL encryption packets is resource-intensive.
- Poor handling of unexpected input can lead to application crashes or surrender of control to execute arbitrary instructions. Unintentional or ill-advised use of externally supplied input in control contexts may allow remote manipulation or information leakage.
- Cryptographic flaws may be exploited to circumvent privacy protections.
- Attackers use SSL to tunnel HTTP attacks to target the server.
OSI model security and compliance strategies:
Remove the SSL from the original infrastructure. Then inspect the application traffic for any signs of malicious activities. Search for any violations of policy at the application delivery platform. Verify that the traffic is re-encrypted and sent back to the original infrastructure.
Layer 7: The Application layer
The Application layer is the layer where communication partners are identified. This is the database-access level where end-user protocols, such as FTP, Telnet, Simple Mail Transfer Protocol and Remote Access Service, perform their respective functionalities. All messages and packet creations begin at this level. Data appears visually for the user and it contains a set of services an application can use.
OSI layer vulnerabilities:
- PDF GET requests, HTTP GET, HTTP POST, = website forms (login, uploading photo/video, submitting feedback).
- Open design issues allow free use of application resources by unintended parties. Inadequate security controls force "all or nothing" approach, resulting in either excessive or insufficient access.
- Overly complex application security controls tend to be bypassed or poorly understood and implemented.
OSI model security and compliance strategies:
To prevent attacks on Layer 7, employ software monitoring applications that detect zero-day attacks, which can also be used to stop and track the source from where the attack initiated. Issues with open design can potentially allow the free use of application resources by malicious parties, because backdoors and application design flaws can allow easy bypass of standard security controls.








