
beebright - Fotolia
6 types of insider threats and how to prevent them
From disgruntled employees to compromised users to third-party vendors, here are six types of insider threats and best practices to mitigate the issues.
Insider threats pose a significant enterprise security risk -- one that's only growing. According to Ponemon's 2022 "Cost of Insider Threats Global Report," 60% of companies experience more than 21 insider incidents annually, up from 53% in 2018.
The good news is there are steps to take -- as well as signs to look for -- to detect and protect against common insider threats without breaking the bank.
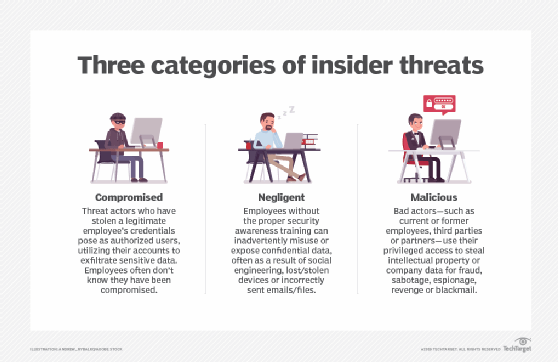
The three broad categories of insider threats are the following:
- Compromised insiders. For example, an employee gets infected with ransomware after clicking a malicious link in a phishing email.
- Negligent insiders. For example, an employee misplaces a laptop or thumb drive or sends an email to the incorrect recipient.
- Malicious insiders. For example, an employee commits fraud or takes sensitive data when quitting the company.
Negligent insiders accounted for 56% of incidents over a 12-month period, according to the Ponemon report, while malicious insiders accounted for 26% of incidents and 18% of incidents related to compromised insiders.
These broad categories can be further broken down into the following six more specific insider threats:
- careless workers
- compromised credentials
- disgruntled employees
- departing employees
- inside agents
- third-party threats
Let's look at each threat, and explore best practices to mitigate them.
1. Careless workers
Problem
Careless workers, sometimes referred to as security evaders, disobey the rules and disregard company security measures either knowingly or unwittingly. These vulnerabilities pose an insider threat in many ways, including the following:
- shadow IT use;
- insecure file sharing;
- leaking company data via email and IM;
- insecure use of wireless networks;
- posting information to discussion boards and blogs;
- improper patching; and
- ignoring security policies.
Examples
In January 2020, misconfigured Azure security rules left five Microsoft servers visible to anyone on the internet, exposing 250 million customer records. In June 2019, the private data of employees at NHS 24, Scotland's telehealth and telecare organization, was erroneously sent in a companywide email, rather than just to senior executives.
Solution
Making employees care about security can be a challenge. Companies should conduct cybersecurity awareness training and build a security culture.
Companies should also implement security controls to manage the threat vectors commonly exploited by careless workers. These include the following:
- Monitor for shadow IT.
- Implement secure file sharing best practices and permissions.
- Use client- or server-based content filtering.
- Maintain patching best practices.
- Require secure network connectivity via VPNs or through a zero-trust framework.
- Use Wi-Fi Protected Access 3.
- Disable Bluetooth if not needed.
2. Compromised credentials
Problem
Compromised employees are one of the most common types of insider threats. Attackers who have stolen legitimate users' logins are one of the leading causes of data breaches. Credentials are often compromised via the following means:
- phishing and social engineering scams
- brute-force attacks
- credential leaks
- keyloggers
- man-in-the-middle attacks
- dictionary attacks
- credential stuffing
- password spraying attacks
Compromised credentials can lead to malware infection, data breaches, ransomware attacks and more.
Examples
In July 2020, a group of malicious actors breached Twitter's network during a vishing attack on employees, enabling the group to send tweets from high-profile accounts. In March 2020, data on 5.2 million Marriott guests was accessed via the credentials of two compromised employees.
Solution
Use proper email security controls, email security gateways and email filtering. Require strong passwords/passphrases, and ensure those requirements are described in a corporate password policy. Also, teach employees about the warning signs of phishing scams. Require multifactor or two-factor authentication, employ privileged access management and the principle of least privilege (POLP), and conduct regular access reviews to verify users' access rights.
3. Disgruntled employees
Problem
Disgruntled employees are insiders who may be current or former workers. These individuals have malicious intent and carry out attacks on their employer for revenge, sabotage, personal and financial gain, or fun. Current employees with privileged access and former employees who retain access after leaving the company or being fired may steal intellectual property, proprietary data, trade secrets, source code and more.
Examples
In July 2020, two General Electric employees stole intellectual property from the company to open a competing organization. In February 2017, autonomous driving technology company Waymo, a subsidiary of Google's parent company, sued Uber, alleging three ex-Google employees stole trade secrets before leaving the company to join Uber.
Solution
On the managerial front, promote transparency, communication and collaboration by conducting employee interviews, check-ins and surveys. On the IT front, hold cybersecurity trainings, and monitor user behavior for abnormal activity and behavioral changes.
4. Departing employees
Problem
Employees who quit their jobs are one of an organization's biggest insider concerns, largely because they can take important company information to competitors. These employees can be malicious -- for example, by stealing company-owned information, such as email addresses and contact lists -- or negligent -- for example, by taking projects they worked on when leaving, believing they own their work.
Example
An employee at security software company Code42 downloaded the entire contents of her laptop prior to her last day at the company. When asked why by her manager, the employee said she was only trying to copy her contact list.
Solution
Ensure employees who leave are aware they cannot take corporate property. Monitor for employees downloading larger amounts of data than normal. Perform offboarding processes to terminate employees' access rights after they leave.
5. Inside agents
Problem
Inside agents, also referred to as moles, collusive threats or collaborators, are malicious insider threat actors who use their access credentials to steal information for or carry out attacks on behalf of external threat actors. These insider threats may be involved in bribery or blackmail. Fraud is also common among inside agents, for example, through embezzlement or insider trading.
Examples
In December 2021, an employee at technology company Ubiquiti misused his privileged access rights to steal confidential data and extort his employer. In November 2019, a Trend Micro employee stole names, email addresses and phone numbers from a company database and sold the information to a malicious third party.
Solution
Employ POLP to limit what applications, networks and data employees have access to. Also, use monitoring, zero-trust network access and behavioral analytics to detect anomalous activity.
6. Third-party threats
Problem
Third parties that have access to enterprise systems -- think contractors, part-timers, suppliers, service providers and customers -- present a major risk to sensitive data. Also known as supply chain attacks or value chain attacks, third-party attacks make sensitive information and a company's reputation vulnerable.
Example
In the 2013 Target breach, customer information and corporate data was stolen from the company's point-of-sale system after an HVAC contractor's credentials were obtained by hackers.
Solution
Ensure third parties are trustworthy. Look at their background, and get references before engaging. Also, have a sound third-party risk management program in place. In addition, monitoring tools are instrumental in detecting third-party threats. Restrict third-party access through POLP. Regularly review third-party accounts to ensure system permissions are terminated after work is completed.
How to detect insider threats
Because these attacks originate within the organization -- or, at least, use the credentials of someone within the organization who has legitimate access -- insider threat detection can be extremely difficult.
Organizations must rely on a mix of people and technology to detect insider attacks. On the people side, monitor employees and insiders from a human aspect. Often, just talking with employees is an indicator of a bad or off attitude.
On the technology side, monitoring tools and user behavior analytics (UBA) can detect for the following abnormal employee behaviors:
- accessing information and applications not relevant to their job role;
- installing unauthorized applications or using unauthorized devices;
- logging in to accounts and applications outside normal working hours;
- logging in to accounts and applications outside regular locations;
- downloading large amounts of data;
- creating accounts; and
- violating company policies.
How to prevent and defend against insider threats
As mentioned, security awareness training and a cybersecurity culture are key to preventing and defending against malicious, compromised and negligent insider threats. Cybersecurity hygiene best practices, including UBA, regular user access reviews, a sound identity and access management program and monitoring, are also necessary controls to prevent insider threats of all kinds.
Additional insider threat prevention best practices include the following:
- Use data loss prevention software.
- Use SIEM and security orchestration, automation and response.
- Use endpoint detection and response.
- Classify data, and secure based on risk levels.
- Encrypt data at rest, in motion and in use.
- Conduct OS and application logging.
- Disable Remote Desktop Protocol whenever possible.
- Review firewall rules to limit what is allowed into and out of the network.








