Evaluating SOC automation benefits and limitations
Security operations center automation can help address the security skills gap by scaling critical analyst responsibilities. But an overreliance on AI introduces other risks.
All eyes are on the cybersecurity industry to innovate better, more resilient solutions to constantly evolving cyberthreats. Long before the pandemic ushered in a new era of cybersecurity and workforce dynamics, security operations centers were used to evaluate how emerging technologies best enhance security postures.
AI has significant potential to reshape how organizations safeguard, resource for and contain expanding IT and IoT security landscapes and associated business assets. AI is an umbrella category for statistical techniques used to review massive amounts of data and language, to detect patterns and to predict outcomes. In cybersecurity, this takes several distinct forms. Before rushing to deployment, security leaders must evaluate the benefits and risks of AI in the SOC and consider the implications unique to their organization.
The primary benefit of SOC automation is the ability to scale the scope and speed of threat analysis and response. Scale is not just important for traditional drivers, like cost, but also to keep up with attackers' tactics and potential reach. The ability to scan millions of incidents and events, tag those events, and recognize and retain patterns across all of them is virtually impossible to achieve manually. "AI technologies can literally perform the equivalent of years of manual security every minute," said Raef Meeuwisse, Certified Information Systems Auditor, Certified Information Security Manager and author of several books on cybersecurity.
AI's scalability translates to other visibility and security strategy benefits. Visibility across the ever-widening security landscape -- devices, apps, IoT and clouds -- is a logistical and financial challenge in and of itself. AI is used for landscape analysis to scan millions of events -- including connections, transactions, identities and applications -- to correlate threats and to assess how one threat or cluster could impact another.
Visibility across the topology also enables the strategic benefit of moving from a defensive cybersecurity posture to an offensive one. Traditionally, SOCs spend the majority of time and resources responding and reacting to threats, but AI's incident analysis and detection applications use a range of techniques to accelerate time to response, including the following:
- mine data on security incidents;
- assign risk scores;
- cluster for commonalities;
- differentiate and prioritize different classes of threats;
- triage notifications to human analysts;
- recommend response or remediation steps; and
- automate containment activities.
These techniques help analysts shift toward being more proactive by automating prevention actions, as well as spotlighting areas for deeper forensic analysis that helps humans understand more about attacks to inform stronger, smarter offensive cybersecurity techniques.
Offense is crucial for mitigating emergent threats and new security challenges, such as remote work. It is also critical to fighting new technological or social engineering tactics, such as targeting an executive's mobile device via smart malware. However, current machine and deep learning systems are limited by the data and features they are taught. Conversely, attackers can fool AI systems with the unexpected. New forms of artificial neural networks and techniques like transfer learning promise to enable less myopic AI, but any emerging technology has blind spots, unintended consequences and costs that come with misuse.
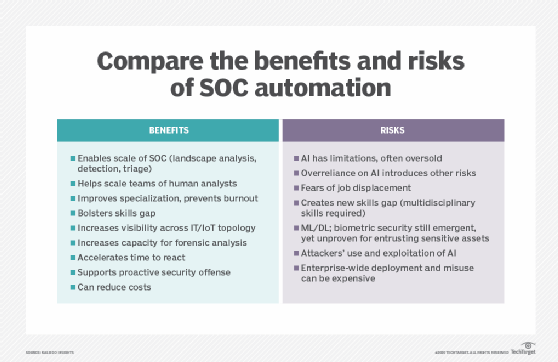
Using AI to manage and scale the massive volume of security alerts can also have positive impacts on employees. SOC analysts are often overwhelmed and understaffed, given they are responsible for mitigating ever-evolving security incidents. Even the most experienced human analysts cannot manage this influx, and those analysts should be spending their time on specialized tasks anyway. Cybersecurity already faces a problematic shortage of talent, and the stress and tedium of manual security alert management have led to burnout and staff attrition for some 40% of organizations surveyed in a 2018 study.
Simultaneously, SOCs must assuage workers' fears that AI adoption is the first step to job displacement. Unlike in other functions where decision-making or risk mitigation may be binary -- yes or no, accept or deny -- SOC analysts' ability to decipher, contextualize, specialize and problem-solve will be needed more than ever.
AI is not equipped for complex problem-solving, understanding nuances or recognizing cultural awareness, so human analysts must focus on the higher-order tasks and mission-critical risks. Automated techniques are better at managing massive volumes of threat alerts to understand exactly what the problem is, but human analysts remain essential to understanding the why. In addition to determining details such as the attacker's motives, these analysts can also decide how best to optimize AI cybersecurity techniques and data.
Successful AI demands multidisciplinary skills and extensive domain expertise, which many organizations lack. Enterprise SOCs must incorporate new roles around the security table. In addition to security analysts who can identify potential breaches, data scientists will be valuable for analyzing the data. Machine learning engineers help translate questions and parameters into algorithms and models.
Across all these areas, there are cost implications that come with SOC automation, both in expenditure and savings. With the right governance, coverage and configuration, applications can help SOCs reduce several critical security metrics, such as time to detect, triage, time to investigate, time to respond and total dwell time -- the time from when an organization identifies a breach to when an adversary gains access. Organizations that contained a breach in less than 30 days saved over $1 million as compared to those that took more than 30 days to resolve, according to a 2018 Ponemon Institute study. There is also potential indirect cost savings embedded in the improved employee satisfaction and company brand reputation that come with security-mindedness.
The next-generation SOC will incorporate automation and orchestration across people, tools and platforms, but powerful tools like AI require greater responsibility. Ultimately, the greatest value of SOC automation comes from combining the virtues of both humans and machines.





