The pros and cons of biometric authentication
Biometric authentication can be a solid supplement to passwords when securing data and systems. But understanding potential drawbacks, and planning to minimize them, is essential.
Authentication relies on three different methods: something you know (e.g., a password); something you have (e.g., a token); and something you are (e.g., a fingerprint). Most strong authentication mechanisms employ two of these three methods. Problems arise when a forgotten password must be reset or when lost tokens need to be replaced. Once a simple extra step, authentication has become a cumbersome process taxing the cognitive load of most users. Passwords, even with helpful phrases to assist a person's recall, are difficult to keep straight. Given these drawbacks, biometric authentication begins to sound like a practical solution.
Unlike passwords, biometrics don't get misplaced. Authentication can be accomplished through methods that include fingerprints, retina scans, facial recognition, DNA matching, behavioral biometrics, vein recognition and iris scanning. These passwordless methods of identification can improve the user experience and reduce costs in other areas. But there are pros and cons to biometric authentication.
Pros of biometric authentication
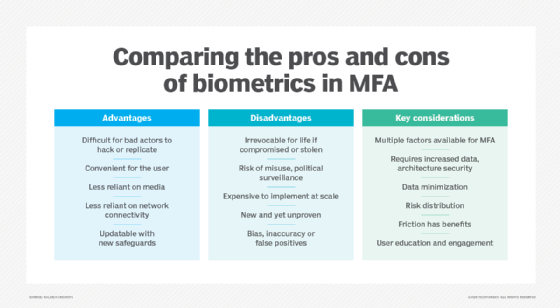
Because of their unique nature, biometrics provides several benefits, including the following:
- Convenience. Users won't misplace or forget a body part. This makes for a better user experience for them. Plus, fewer forgotten passwords mean fewer hassles for an IT support team.
- Unique security attribute(s). The uniqueness of a fingerprint or retina provides nonrepudiation; a user can't claim the data they accessed wasn't touched by them.
- Reduced risk of human error. When the fingers and brain are not in sync, it's easy for humans to make errors with transcription and character transposition.
- Scalability. The ability to grow the authorizations of a user based on a single token holds the promise of a few keystrokes to dynamically allow or disallow access.
- Fraud detection and accountability. The nonrepudiation feature of biometric authentication makes a case for biometric use in fraud detection and accountability, since the user can't deny their role in sending the data.
- Administrative cost savings. An organization using biometrics will spend less on help desk calls for password resets.
Cons of biometric authentication
The most troubling aspect of biometric authentication is their irreplaceable nature. Stolen digital retina data or fingerprint data can't be regrown with slightly different characteristics. There are ways to minimize the likelihood of such losses, but -- once lost -- full replacement is a challenge. Given that fact, it's important to be aware of the following problems connected with biometric authentications:
- Credential theft. Not only will the user be spoofed, but other accounts that rely on the same biometric data are at risk. While passwords can be unique to sites and reset when necessary, these option aren't possible with biometrics. Also, modern AI algorithms can be used to generate fingerprints that are capable of deceiving fingerprint scanners.
- Accidents and aging. Bodily injury can result in a biometric being lost or changed. For example, a significant burn can change a fingerprint's spaces and ridges. And as people grow older their physical characteristics don't remain the same, which can result in errors.
- Environmental factors. A common problem with facial recognition occurs when changes in lighting result in an authentication failure. Iris scanning might not work when the user has long eyelashes, wears colored contact lenses or a reflection catches the subject's cornea. Dryness can affect a fingerprint. And emotions can disturb biometric behavior.
- Implementation costs. The hardware and software required for biometric authentication can be costly. To ensure their effectiveness, these systems need to be regularly updated and maintained.
- Hardware deterioration. Biometric interfaces can degrade over time. Combined with slight bodily changes, this can increase the number of false positives or negatives.
- DoS attacks. A simple DoS attack can be performed by someone who knows a system's naming convention and enters incorrect biometric information, which results in a user being locked out. While this type of DoS attack is possible with other authentication mechanisms, there is no way to make a quick fix to a biometric system the way there is with a password-based system. Typically, a back-up mechanism of username-password combination is deployed.
- Record deletion. When biometric authentication is no longer needed, such as when an employee leaves a company, assurances must be made that the digital instances of biometric data will be destroyed. This preserves the user's right to be forgotten.
Best practices to protect biometric data
In the absence of perfection, best practices can help to protect biometric information. Suggestions include the following:
- Never store biometric information on a server. A server housing a group of biometric tokens is a likely target for attackers, who could harvest information from many users at a single site. Stored biometric information should be kept on a local device that the user authenticates with each login attempt.
- Stored biometric data must be encrypted using a strong algorithm and robust key management. In the event the storage device is stolen, attackers shouldn't be able to find the user's biometric information.
- Active patch management is critical for all firmware deployed to manage and store biometric information.
- The physical device that stores the biometric information must also be sealed and resistant to physical tampering.
- Use multifactor authentication with biometric authentication to create a more rigorous authentication process.
- Use reputable vendors.
- Get assurances -- in writing -- that biometric information will be destroyed when the mechanism is no longer needed.
Because of its ease of use, biometric authentication will likely continue to grow. This might force vendors to build security into the products. While these more-secure products might cost more, the cost of security failures in the case of biometric information is unacceptable.
Char Sample is a cybersecurity research fellow at ICF International.






