
DoS vs. DDoS: How they differ and the damage they cause
DoS and DDoS attacks may not be new, but that doesn't mean they are any less disruptive to organizations. Companies should understand what they are and how they work.
At 50 years old, denial-of-service and distributed DoS attacks are well known -- yet they continue to wreak havoc on organizations of all industries and sizes. Malicious actors use these tried-and-true attacks because they remain successful.
Let's look at each attack and how they differ.
What is a DoS attack?
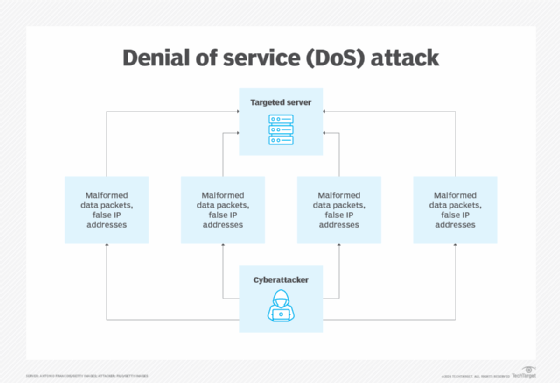
A DoS attack typically targets one machine or server. The attacker floods the target with multiple requests for shared resources, and the machine comes to a grinding halt. The server's processing and compute powers are overwhelmed, and it simply cannot keep up with demands.
As a result, end users might be unable to send email, visit a website or process basic transactions online. While a DoS attack is not meant to take over the server -- and most victims recover from such an attack -- the consequential downtime can generate steep financial losses. Indirect costs, such as lost customers and associated brand or reputational damage, are also incurred. Most DoS attacks aim to disrupt operations and prevent an organization from conducting normal business, unlike the financial or data-stealing motives of other attacks, such as extortionware or ransomware.
Malicious actors launch DoS attacks by targeting a specific computer and then bombarding it with false IP addresses and malformed data packets. A successful attack can paralyze a device in a matter of minutes or as long as a few days, depending on how quickly and pervasively the addresses and packets are delivered.
Types of DoS attacks
DoS types generally fit into the following categories:
- Browser redirection. In this attack, the end user is sent to a different website than the intended one.
- Closing connections. Once the end user closes out of a website, they cannot access it again because the connection is no longer active.
- Data destruction. The cyberattacker deletes shared resources in the server.
- Resource exhaustion. The end user's access to the server slows to a crawl. This is the most common DoS attack.
What is a DDoS attack?
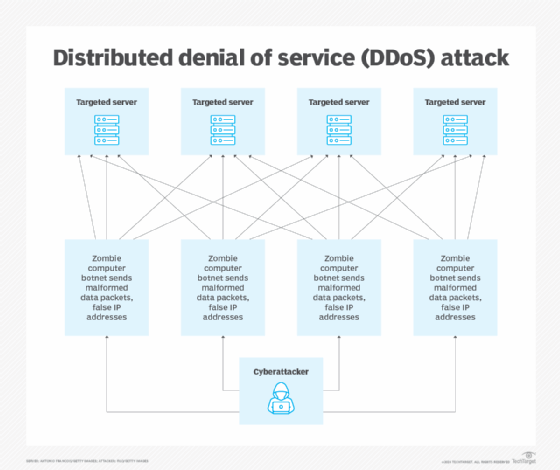
A DDoS attack is similar to a DoS attack but with the goal of shutting down more than one machine or service. A DDoS attack uses multiple malicious hosts to infect multiple machines at the same time. A single DDoS attack can hit multiple victims in different parts of the world simultaneously. Attackers have used this technique to bring down critical infrastructure components, such as water supplies and power grids.
DDoS attacks rely on infected host servers or machines, known as botnets or zombies. The zombies, in turn, are controlled by a remote computer through which the attack is launched. Given the magnitude and scale of a DDoS attack, it is difficult to track down the perpetrators. DDoS attacks are fueled not only by the huge interconnectivity of both physical and virtual devices, but by the evolution of IoT as well.
DDoS attacks exploit the same vulnerabilities targeted by DoS attackers, but due to the number of machines and servers involved, the scale of the damage can be much greater.
Some noteworthy DDoS events include the February 2020 attack on AWS, which exploited a Lightweight Directory Access Protocol vulnerability; the December 2020 attack on Google launched by Chinese ISPs; and the September 2016 Mirai botnet attack on Krebs on Security, Dyn and other sites.
Types of DDoS attacks
DDoS attacks fall into three main categories:
- Volume-based attacks are the most common, in which attackers flood targets with requests.
- Protocol attacks target Layer 3 (network) and Layer 4 (transport) of the Open Systems Interconnection (OSI) model.
- Application layer attacks, which target Layer 7 (application) of the OSI model, are deemed the most difficult to mitigate and detect.
Common attack methods include the following:
- User Datagram Protocol (UDP) flood. In this attack, ports on the server are flooded with malformed data packets, which overwhelm the system as it attempts to assemble the malformed packets. UDP flood attacks can use DNS, Network Time Protocol, VoIP and peer-to-peer networks, among others.
- Internet Control Message Protocol (ICMP) flood. Also known as a ping flood attack, malicious actors overwhelm the victim with ICMP echo requests. Using numerous devices, the attackers flood servers with spoofed ping packets. This affects both inbound and outbound bandwidth as the server attempts to reply to each ping. ICMP flood attacks can target one specific internal endpoint, such as a router or computer.
- HTTP flood. Malicious actors send numerous HTTP requests to a web server to slow it down or overwhelm it. Attackers can use HTTP GET or HTTP POST. GET involves flooding the server with numerous requests for images or files, while POST continually requests URLs from a server until it crashes.
- TCP SYN flood. Malicious attackers send SYN requests to a server but never send the ACK back. As a result, the traditional handshake between the end user's computer and the server cannot be completed. Malicious actors can use either a reflection or distributed attack. Reflection involves sending the SYN request to a server with a spoofed IP address, which then gets every SYN-ACK response. A distributed attack uses a botnet to send out additional SYN requests.
- Fraggle attack. This attack uses UDP echo requests to inundate a broadcast or multicast address on a server.
- Smurf attack. This is similar to a fraggle attack, except a smurf attack uses ICMP echo requests.
- Slowloris. This attack targets a web server. It creates a cascading effect on all websites on the same server by initiating HTTP requests and keeping each active.
- Buffer overflow. The attacker targets the memory regions of the server to consume all available memory storage. This means the amount of data held far exceeds the processing power of the server. Malicious actors can use either stack- or heap-based buffer overflow attacks. Stack-based buffer overflows target memory available at time of the attack, while heap-based attacks target all memory for a program.
- Fragmentation attack. Malicious actors send fragmented IP packets that exceed maximum size parameters when reassembled. Attackers might send malformed packets that crash the server or overload resources when it attempts to reassemble the fragmented packets. Examples include TCP, bonk and tiny fragment attacks:
- TCP or teardrop attacks are when IP packets are not intended to reassemble. This can crash the server.
- Bonk attacks use large fragments designed to exceed allocated buffers.
- Tiny fragment attacks use fragments that are smaller than the header and interrupt the ability to reassemble the packet correctly.
- Ping of death. Attackers send oversized data packets to the server -- usually greater than 65,535 bytes -- in smaller, fragmented packets. The server becomes overwhelmed when it tries to reassemble the packets and they exceed the maximum allowed size. Malicious actors use this to attack hypervisors, cloud instances and cloud networks.
- Amplification attack. Also known as a reflection attack, an amplification attack involves malicious actors spoofing IP addresses to send requests to a reflector server, which generates a large response that then overwhelms a server. Amplification attacks can target TCP, UDP, ICMP, Simple Service Discovery Protocol/Universal Plug and Play and DNS, which is the most popular version of the attack.
How to prevent DoS and DDoS attacks
DoS and DDoS attacks hit without warning. It is, therefore, critical organizations not only know how to identify such an attack, but also reduce exposure and know how to mitigate the effects of DoS and DDoS attacks. A few options include the following:
- Continuously monitor networks for signs of an attack.
- Use a web application firewall to monitor and filter web traffic.
- Spread networks into smaller subnets using network segmentation.
- Use rate limiting to control the number of incoming requests and prevent overloading a system.
- Use a content delivery network, which uses distributed servers and makes it more difficult to bring down an organization's network.
- Follow patching best practices.
- Maintain proper cyber hygiene.
Ravi Das is a cybersecurity consultant and business specialist who specializes in penetration testing and vulnerability management content.






