
Getty Images
12 DevSecOps tools to secure each step of the SDLC
DevSecOps tools integrate security throughout development. These 12 options enhance workflows from coding to deployment without slowing teams down.
DevSecOps has transformed software development, taking security from a bolted-on afterthought to an integral part of the process. Security decisions and implementation now happen in real time alongside development.
DevSecOps success hinges on choosing the right security tools and embedding them at every stage of the software development lifecycle (SDLC) -- from initial code commits to deployment and runtime monitoring. These tools must be both powerful enough to catch vulnerabilities and intuitive enough for developers to embrace. The wrong tools create bottlenecks and resistance, while the right ones enhance existing workflows. In today's rapid development environment, this choice can make or break DevSecOps implementation.
Let's look at 12 popular developer-focused tools, all offering free or open source tiers, that demonstrate how modern DevSecOps can enhance rather than impede the development process.
The following DevSecOps tools were chosen based on firsthand experience and consulting with clients. It is ordered by the phases of the SDLC.
IriusRisk
Threat modeling is increasingly critical in modern software development. IriusRisk is an automated threat modeling platform that helps teams identify and mitigate security risks early in the SDLC based on system architecture diagrams and questionnaires. The platform stands out for its ability to scale threat modeling across large organizations while maintaining consistency and reducing the manual effort traditionally required for security assessment.
Additional IriusRisk features include the following:
- Built-in security standards. Incorporates major security standards, such as OWASP, NIST and Mitre, helping ensure compliance with industry best practices.
- Integration capabilities. Integrates with popular development tools, such as Jira, GitHub and Jenkins.
- Reusable components library. Maintains a comprehensive library of threat patterns and countermeasures that can be quickly applied to new projects.
- Risk visualization. Provides clear visual representations of security risks and their potential impact on the system.
- Collaborative features. Enables security and development teams to work together effectively on threat assessment and mitigation strategies.
IriusRisk offers a free Community edition and paid Enterprise edition. The Community edition, available as SaaS, includes the creation of up to three threat models, as well as access to its AI assistant. The Enterprise edition, available as SaaS or on-premises, includes unlimited users and a purchasable amount of threat models. Contact IriusRisk for pricing.
Semgrep
For comprehensive static application security testing, organizations can use Semgrep, which combines powerful code analysis with dependency and secrets scanning capabilities. A standout feature is its intuitive approach to custom rule creation. Developers can copy and paste code patterns they want to find and add placeholders for variables, and Semgrep semantically matches similar patterns across the codebase. This feature makes it useful for enforcing company-specific coding standards and finding business logic flaws.
Devs can also use Semgrep to analyze individual API specifications and scan hundreds of repositories simultaneously at the enterprise level.
Additional Semgrep features include the following:
- Reduced false positives. Context-aware scanning understands code structure rather than just pattern matching, leading to more accurate and actionable results.
- Custom standards enforcement. Create and maintain organization-specific coding standards and security rules through intuitive pattern matching.
- Continuous integration/continuous delivery integration. Provides existing CI/CD workflows with support for major CI platforms and API access for custom integrations.
The free version of Semgrep provides access to open source rules, custom rule creation and CI integration, making it suitable for individual developers and small teams.
Semgrep offers paid enterprise options: Semgrep Code at $40 per contributor per month, Semgrep Supply Chain at $40 per contributor per month and Semgrep Secrets at $20 per contributor per month, as well as customized pricing. The first 10 contributors for Semgrep Code and Semgrep Supply Chain are free. Paid features, which might not be available in all, include advanced secrets scanning to detect hardcoded credentials and tokens, software composition analysis to identify vulnerable dependencies, role-based access control and priority support. The dependency scanner identifies outdated or vulnerable packages and provides actionable upgrade paths. The paid options also include supply chain security features, compliance reporting and API access for custom integrations.
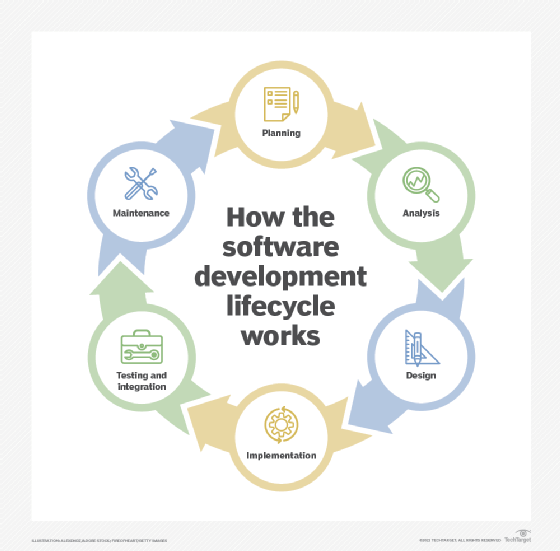
Snyk
As organizations grapple with the exponential growth of open source dependencies and containerized applications, Snyk has emerged as a leading developer-first security platform that seamlessly integrates vulnerability management into existing development workflows.
What sets Snyk apart is its focus on actionable intelligence. Rather than overwhelming developers with endless vulnerability lists, it prioritizes risks based on exploitability and provides clear upgrade paths and automated fixes. The platform's strength lies in its comprehensive coverage across the software supply chain, scanning everything from package dependencies and container images to infrastructure as code (IaC) configurations.
Key Snyk features include the following:
- Developer-native workflows. Integrates directly into integrated developer environments, Git repositories and CI/CD pipelines without disrupting developer workflows.
- Intelligent prioritization. Uses exploit maturity data to focus on vulnerabilities that actually matter, reducing alert fatigue.
- Automated fix generation. Automatically creates pull requests with dependency upgrades or patches for one-click vulnerability resolution.
- Comprehensive scanning. Covers open source dependencies, container images, IaC templates and code repositories in a unified platform.
- Security education. Provides inline learning with vulnerability explanations and secure coding guidance.
- License compliance. Monitors open source license usage and flags potential compliance issues.
Snyk offers a free tier for individual developers and small teams that includes vulnerability scanning for open source dependencies, basic container scanning and limited IaC analysis, making it accessible for individual developers and small teams. The paid tiers -- Snyk Team at $25 per month per developer and Snyk Enterprise at a custom price -- add enterprise features such as advanced container security, comprehensive IaC coverage, proprietary code analysis and team collaboration tools.
ZAP and StackHawk
Zed Attack Proxy, or ZAP, is one of the world's most widely used open source web application security scanners. Created by OWASP and now supported by Checkmarx, it acts as a man-in-the-middle proxy to intercept and inspect messages between client and web application. Key features include automated vulnerability scanning, passive scanning while browsing, web crawling and a REST API.
ZAP is known for its extensive community support, active development and integration capabilities with CI/CD pipelines. It's used by organizations of all sizes, from small teams to major enterprises.
StackHawk is built on ZAP's core engine, modernizing and streamlining security testing for DevSecOps workflows. It enhances ZAP's capabilities with the following:
- Native CI/CD integration, especially with GitHub Actions.
- Modern API security testing features.
- Simplified configuration and setup.
- Team collaboration features.
- Enhanced reporting and dashboard functionality.
- Better handling of modern authentication methods.
While ZAP remains the go-to free option for web security testing, StackHawk has gained traction among organizations looking for a more polished, enterprise-ready product with dedicated support. StackHawk's focus on developer-first security testing and API scanning has made it particularly popular among teams adopting DevSecOps best practices.
Both tools maintain strong reputations in the security community, with ZAP being especially popular for its reliability and extensive feature set.
StackHawk offers paid tiers. Pro, at $49 per code contributor per month, has a 20-contributor minimum. Enterprise, at $59 per code contributor per month, has a 25-contributor minimum. Organizations with teams of more than 50 code contributors can contact StackHawk for a custom quote.
42Crunch
As APIs become the backbone of modern applications, specialized API security testing has evolved from nice-to-have to mission-critical. 42Crunch addresses this challenge by providing comprehensive API security testing that focuses specifically on vulnerabilities that traditional application security tools often miss.
The platform's strength lies in its deep understanding of API specifications and business logic -- a true shift-left approach that enables it to identify complex flaws like broken object-level authorization and API-specific injection attacks that generic scanners typically overlook.
Key features of 42Crunch include the following:
- OpenAPI-native security. Uses OpenAPI specifications to perform deep security analysis and identify specification-to-implementation gaps.
- API discovery and inventory. Automatically discovers and catalogs APIs across environments, providing visibility into shadow APIs and undocumented endpoints.
- Business logic testing. Analyzes complex API workflows and business logic flaws that require an understanding of the application context.
- Runtime API protection. Provides real-time API traffic analysis and blocking capabilities during production.
- Developer-friendly integration. Works with CI/CD pipelines and provides clear, actionable remediation guidance.
42Crunch offers both SaaS and on-premises deployment options, with a free tier that includes basic API security auditing and limited testing capabilities for a single user. The tool has three paid tiers: Single User at $15 per month per single user, Teams at $375 per month for up to 25 users and Enterprise at a custom price.
GitGuardian
GitGuardian helps organizations prevent costly data breaches by automatically detecting and securing sensitive information, including API keys, credentials and other secrets, across their entire SDLC. Its powerful scanning engine integrates with existing workflows and tools, monitoring repositories, commits and pull requests in real time without disrupting developer productivity.

GitGuardian enables teams to maintain strong security practices while keeping development velocity high by providing immediate alerts and detailed remediation guidance when secrets are exposed. It also helps prevent developers from accidentally committing critical secrets to public repositories.
GitGuardian offers a free Starter tier for up to 25 developers and Teams tier at $220 per developer per year for up to 200 developers. Organizations with more than 200 developers can contact GitGuardian for a custom quote.
Trivy
Security scanning across the entire software supply chain is critical in today's cloud-native landscape. Trivy, an open source security scanner maintained by software vendor Aqua Security, provides comprehensive vulnerability detection and security analysis for containers, applications and infrastructure code across major Linux distributions.
Additional Trivy features include the following:
- Kubernetes security. Identifies misconfigurations and risky settings in Kubernetes workloads to ensure compliance with security best practices.
- Multilayer detection. Scans for vulnerabilities in OS packages, application dependencies, exposed secrets and license violations.
- IaC coverage. Examines security configurations in IaC files, including Terraform and Kubernetes manifests.
- DevSecOps integration. Offers fast scanning with low false positives, designed for easier integration into CI/CD pipelines.
The key differentiator for Trivy is its combination of broad feature coverage -- containers, IaC and dependencies -- with simplicity and speed, making it appealing for teams that want a single, straightforward tool for multiple security scanning needs.
Falco
In cloud-native environments where containers and microservices create complex, dynamic attack surfaces, traditional perimeter-based security approaches fall short. Falco, a Cloud Native Computing Foundation (CNCF) graduated project, provides real-time runtime security monitoring that detects anomalous behavior and potential threats as they occur. By operating at the kernel level, Falco provides deep visibility into system calls and container activities that would be invisible to traditional monitoring tools.
Key features of Falco include the following:
- Real-time threat detection. Monitors system calls and network activity in real time to detect security incidents as they happen.
- Cloud-native awareness. Natively understands Kubernetes environments and container lifecycles for context-aware security monitoring.
- Behavioral analysis. Uses rule-based detection to identify deviations from normal behavior patterns.
- Extensive rule library. Comes with comprehensive built-in rules while supporting custom rule creation.
- Flexible output integration. Sends alerts to Slack, PagerDuty, SIEM platforms and custom webhooks.
- Low performance impact. Designed for production environments with minimal overhead.
Falco is open source, with strong community support and extensive documentation.
KICS
As IaC adoption accelerates, security misconfigurations in cloud infrastructure templates have become a leading cause of data breaches and compliance failures. KICS (Keeping Infrastructure as Code Secure), developed by Checkmarx, provides comprehensive static analysis for infrastructure templates before they reach production environments. The platform catches infrastructure security issues during the development phase, when fixes are cheapest and easiest to implement.

Key features of KICS include the following:
- Multiplatform coverage. Scans Terraform, CloudFormation, Ansible, Kubernetes manifests, Docker files and more across diverse infrastructure toolchains.
- Comprehensive query library. Includes 2,000-plus built-in security and compliance queries covering Center for Internet Security benchmarks, GDPR, HIPAA and cloud provider best practices.
- Custom rule creation. Enables teams to write organization-specific security policies using a simple query language.
- CI/CD integration. Seamlessly integrates into development pipelines with support for major CI platforms.
- Detailed remediation guidance. Provides clear explanations of security issues with specific remediation steps.
- Multiple output formats. Supports JSON, SARIF and other formats for integration with security dashboards and SIEM platforms.
KICS is open source, with active community development and regular updates.
CycloneDX
CycloneDX is a lightweight software bill of materials (SBOM) specification that tracks and documents components in software applications, enabling better security and compliance management. It stands out for its broad industry adoption and backing by OWASP, making it an ideal SBOM specification for organizations that need to understand and manage their software dependencies and supply chain risks.
CycloneDX integrates well with the other tools featured here and works with XML, JSON and protocol buffer data formats. Organizations can create SaaSBOMs, hardware BOMs and vulnerability disclosure reports using CycloneDX.
OPA
As modern applications become increasingly distributed across microservices, containers and multi-cloud environments, enforcing consistent security and compliance policies becomes exponentially complex. Open Policy Agent (OPA), a CNCF graduated project, provides a unified policy engine that enables policy as code, which helps organizations define, version and enforce security policies using the same development practices applied to application code.
Key features of OPA include the following:
- Universal policy engine. Provides a single framework for policy enforcement across Kubernetes, microservices, CI/CD pipelines and cloud APIs.
- Policy as code. Enables security policies to be written in policy language Rego, which helps version, test and deploy policies using standard DevOps practices.
- Real-time decision-making. Performs authorization and compliance decisions in milliseconds without affecting application performance.
- Rich integration ecosystem. Integrates natively with Kubernetes, Istio, Terraform, Jenkins and hundreds of other tools through a REST API.
- Flexible deployment models. Runs as a lightweight sidecar, standalone service or embedded library.
OPA is open source, with strong enterprise adoption and commercial support available from various vendors.
Colin Domoney is a software security consultant who evangelizes DevSecOps and helps developers secure their software. He has previously worked for Veracode and 42Crunch and authored a book on API security. He is currently a CTO and co-founder, and an independent security consultant.






