Cybersecurity career path: A strategic guide for professionals
There's no single path for everyone, but knowing what employers look for and following these best practices can help you move up the cybersecurity career ladder.
Whether you're just starting to explore a potential cybersecurity career, or you have years of experience in the field and want to keep advancing, understanding the cybersecurity career roadmap is critical. A career roadmap defines the job titles and promotion paths that professionals in a particular industry typically pursue.
But the cybersecurity career trajectory can also be challenging because career levels and roles in this domain can vary significantly. So can the compensation levels, skill requirements and growth opportunities associated with different types of cybersecurity positions.
This guide breaks down what professionals need to know when navigating a cybersecurity career. It explains the main career levels and associated roles, identifies common career pathways and offers tips on the most important skills for climbing the cybersecurity job ladder.
An overview of cybersecurity career levels and roles
Broadly speaking, cybersecurity career paths can be broken into four categories, each distinguished by different job titles, experience, educational requirements and salary ranges.
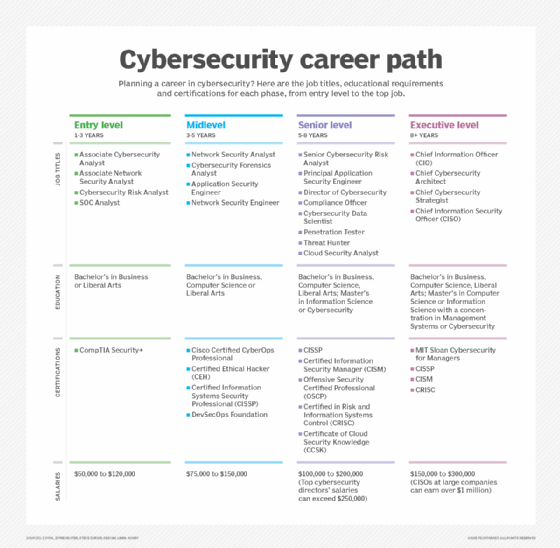
1. Entry level
If you're new to cybersecurity, you'll typically start in an entry-level position. Exact job titles vary, but they often include the words analyst or specialist -- for example, cybersecurity analyst, IT security analyst or forensics analyst. They might also include the term SOC, which is short for "security operations center," the part of an organization responsible for detecting and mitigating cybersecurity threats. The SOC is usually staffed mostly with entry-level personnel.
Responsibilities for entry-level cybersecurity roles typically involve "serving in the trenches," receiving notifications from monitoring tools and responding to threats or risks. The work often involves following playbooks, but demonstrating the ability to manage unforeseen threats and go off script when necessary can help an employee stand out.
Unsurprisingly, salary ranges for entry-level and early-career cybersecurity jobs are low compared with those for more senior positions. ZipRecruiter estimates that cybersecurity analysts earn just under $100,000 on average.
The upside of the lower pay for entry-level positions is that these jobs can be easier to land without formal education. Only about 61% of cybersecurity analysts hold bachelor's degrees, according to the Zippia career website. If you have some general IT experience or training, it's feasible to find a job in cybersecurity even without a formal degree.
2. Midlevel
Midlevel positions are often distinguished from early career roles by job titles that include the terms architect or engineer, such as information security architect or cybersecurity engineer. (However, engineer is also in some entry-level job titles.)
Midlevel cybersecurity jobs focus more on designing and implementing security systems and protocols, and less on the day-to-day operational duties performed by entry-level staff. Nonetheless, people in midlevel positions might be expected to help respond to more complex incidents.
Pay for these positions is often well above $100,000. For instance, information security architects average around $150,000, according to ZipRecruiter.
Educational requirements are also steeper for midrange roles. Virtually all cybersecurity architects hold bachelor's or master's degrees, for instance, according to Lightcast, a provider of labor market analytics. Holders of these jobs also usually have at least five years of experience, and often much more.
3. Senior level
Those who climb higher up the cybersecurity career ladder can land senior-level roles. These often have the word senior in the title -- e.g., senior cybersecurity architect. They might also be director or vice president positions.
Senior-level security jobs usually involve responsibility for overseeing teams of cybersecurity practitioners. They determine how many staff to assign to various security roles. They might also play a lead role in evaluating cybersecurity tools and in establishing security tactics and strategy for the organization.
Salaries for senior cybersecurity roles can exceed $200,000. Senior cybersecurity architect jobs, for example, pay about $250,000 on average, according to the Glassdoor career site. A director of information security makes slightly more, with average compensation of around $270,000.
Most senior-level cybersecurity professionals have college degrees and well over a decade of experience in lower-level roles.
4. Executive level
The highest cybersecurity career level involves executive positions. Chief information security officer (CISO) is the top security role at most organizations. Some companies might also employ a chief security officer (CSO) -- sometimes instead of a CISO -- whose responsibilities are typically broader and encompass risks of all types, not just those related to IT security.
These roles usually report to a chief information officer (CIO), who oversees the IT organization as a whole. However, at some companies, CISOs and CSOs operate as peers, rather than subordinates, of the CIO.
The pay for executive-level cybersecurity roles ranges between $150,000 and $300,000, depending on company size and location. But at large companies, CISOs can earn seven figures.
It is not unheard of for ambitious strivers to become a CISO with as little as a decade of experience. But for many people, this is a role attained only after several decades in cybersecurity. It requires mastery not just of the technical side but also understanding how to work with corporate boards, engage other executives and manage security budgets.
Cybersecurity career areas and pathway examples
Cybersecurity is a dynamic field, and there is no single path that every professional follows as they progress from entry-level to midlevel roles, or from midlevel to more senior or executive-level positions. Everyone's experience will vary.
That said, effective upleveling strategies are available for people hoping to climb the security job ladder. Here are some key examples.
1. Getting out of the SOC
If you're in an entry-level role, such as cybersecurity analyst working in a SOC, and you want to move up to a midlevel role, your best bet is to earn some certifications. Focus on those -- such as Certified Information Systems Security Professional or Information Systems Security Architecture Professional -- that demonstrate the ability to design cybersecurity architectures and strategies. An understanding of cybersecurity design and strategy, more than knowing how to operate tools or respond to threats, is what midlevel and senior-level roles prioritize.
2. Fast-tracking a senior cybersecurity career
The most straightforward way to move into senior cybersecurity positions is to spend many years in lower-level roles, gaining the experience necessary to become competitive for senior-level jobs when they open up.
If you want to fast-track the climb to senior level, one strategy is to seek cybersecurity jobs at startups. Newer, less established companies might be less picky about years of experience and formal credentials than larger companies when hiring senior security staff, especially when applicants demonstrate the ability to think dynamically about cybersecurity strategy.
The drawback is that startup jobs tend to pay less, and much of the compensation might come in the form of equity that you might never be able to cash out if the company ends up failing. But if you can succeed in a senior security role at a startup for several years, you can use that experience to apply to similar jobs at more established companies if you grow tired of swimming the startup seas.
3. Making the jump to CISO
Because most companies have just one or two executive-level cybersecurity positions, only a small fraction of cybersecurity professionals ever land one of these roles. But there's nothing wrong with never becoming a CISO or CSO; it can be a stressful job that, in some cases, only pays marginally better than other cybersecurity jobs.
That said, if you do want to pursue a CISO or similar role, the best approach is to acquire a range of certifications. You should also plan to earn a bachelor's degree or, even better, a master's or doctorate in information security or a closely related field.
Building relationships with executives -- ideally by interacting with them regularly in your senior-level cybersecurity role -- is also key if you want to become a CISO. This isn't only because those connections will help you find and pursue job opportunities, but also because knowing how to talk and act like an executive is (for better or worse) part and parcel of what it means to be a CISO. Those skills are best acquired through osmosis more than any kind of training or education.
Career tips for advancing as a cybersecurity professional
Beyond the scenarios just laid out, the following practices can help advance a cybersecurity career, no matter which role you currently hold:
- Follow the trends -- but always have a foundation. Cybersecurity trends change frequently as technologies evolve. For instance, AI security risks have become a hot topic in the past few years. It's important to keep your cybersecurity skill set up to date with trends like these. However, it's also important to establish a fundamental understanding of the core concepts at play in cybersecurity, including how systems and networks work, as well as the differences between vulnerabilities, risks and threats. The fundamentals apply, no matter which platform or technology you happen to be working with.
- Understand basic IT. In addition to mastering foundational cybersecurity concepts, having a solid grasp of general IT skills is also key for many cybersecurity careers. You'll want to know how software engineering works, what IT administrators do, how organizations manage data and so on. Obtaining generic IT certifications to demonstrate these skills to prospective employers is also valuable.
- Focus on platform-agnostic certifications. While many software vendors and cloud service providers offer certifications linked to their platforms, it's usually best to pursue certifications that aren't tied to a specific vendor ecosystem. A future employer might see a certification as less important if it doesn't focus on a technology that the employer uses.
- Consider adjacent roles. Moving up the cybersecurity career ladder isn’t the only way to advance your career. Some people move from cybersecurity roles into jobs that are close to -- but distinct from -- cybersecurity, such as in the risk management, compliance or network engineering domains. Being open to a cybersecurity-adjacent role can increase the number of job opportunities that come your way. It's also a good option if you don't love cybersecurity work because of the stress or fast pace but want to continue using the security skills and experience you have.
- Don't neglect soft skills. The ability to demonstrate technical expertise through job experience and certifications is crucial for a successful cybersecurity career. But so are soft skills, like those that focus on engaging with other people in the organization. When pursuing new job opportunities, be sure to emphasize your experience working as part of a team, directing teams or spearheading initiatives in an organization. All of these reflect mastery of soft skills.
- Build a public profile. Maintaining a publicly visible profile as a cybersecurity professional can help advance your career, especially at more senior levels. We're not talking just about having a LinkedIn account. Presenting at security conferences, writing articles, participating in bug bounty programs and contributing to open source projects that develop cybersecurity tools are all ways to establish yourself publicly as someone who is deeply experienced and passionate about cybersecurity.
Chris Tozzi is a freelance writer, research adviser, and professor of IT and society. He has previously worked as a journalist and Linux systems administrator.








