jro-grafik - Fotolia
Counter mobile device security threats with unified tools
Attacks on enterprise mobile endpoints are more lethal than ever. To help infosec pros fight back, enterprise mobile management has unified to fortify defenses.
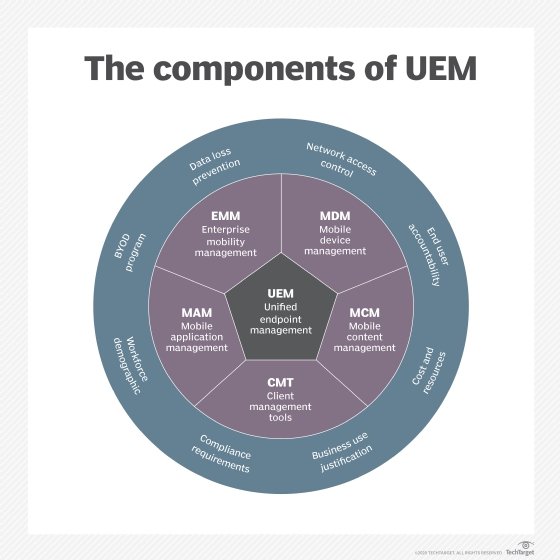
Mobile device management, or MDM, technologies from the past decade or so that intended to tackle mobile device security threats are great for basic password enforcement, data segmentation and remote wiping capabilities. But given the enterprise dependence on the app and content side of the mobile equation, we have to look beyond what we've been doing to more enterprise-worthy and scalable mobile oversight technologies. The next generation of what MDM was trying to accomplish is dubbed enterprise mobility management. EMM and its heir apparent, unified endpoint management (UEM), is where your focus needs to be, at a minimum, if mobile is to be properly corralled and its associated risks are to be minimized.
Where mobile defenses are needed now
Mobile today is really about the soft side of computing. Rather than devices, it's now about things such as the following:
- mobile apps;
- business content;
- team-member collaboration; and
- overall user experience.
Faced with a growing slew of mobile device security threats, IT and security professionals facilitate balancing these areas while, at the same time, maximizing security and usability. That's where EMM comes into play, taking familiar approaches to managing traditional networks, computers and software; delivering better visibility into mobile resources; and managing and enforcing a more granular set of policies. This shows users which apps they're allowed to use, and should be using, in their jobs.
EMM can also help ensure secure document access, sharing and synchronization. With the goal of further enhancing productivity, EMM can also facilitate cloud connectivity and business workflows that, to this point, have been unavailable on mobile platforms.
EMM evolves
What we now know as EMM is solving some common challenges that businesses have experienced with MDM or with another common approach: having no mobile controls at all. EMM is evolving into UEM to further expand mobile security oversight. With a growing set of mobile device security threats and an increasing dependence on mobile for various business functions, UEM is in a good position to address issues across all endpoints. UEM further fleshes out the various means of dealing with mobile device security threats through areas such as the following:
- integration with existing network security controls;
- identity and access management;
- software patching;
- configuration management and system hardening; and
- incident response.
These are all areas that most enterprises struggle with today. Advanced endpoint management tools can further support security standards and policies in these areas that are coming under more and more scrutiny.
Time to move on UEM
Technical solutions such as EMM and UEM can get you where you need to be in the battle against mobile device security threats if properly, and promptly, addressed. Use these tools to your advantage. Otherwise, you risk mobile becoming the big security issue in your business. Do it now while it's less complex. As far as you've come with security, you don't want to make assumptions about what you can handle and attempt to transfer old-school security tactics to this area of IT that needs an updated approach.