Cloud vulnerability management: A complete guide
Your security strategy might not grapple directly with cloud vulnerability management. Is it time to consider the possible benefits and challenges of this emerging product class?
"Don't buy software that you can't manage" is a decades-old adage among IT professionals. That guideline is still in practice today, particularly when it comes to the caution around cloud vulnerability management software.
While there are multiple variations of meaning for cloud vulnerability management, the generally accepted definition is that it is the practice of continuously identifying, managing and remediating vulnerabilities in IT environments. It is a process that eventually becomes a seamless part of an enterprise's overall cloud security program.
While many large corporations have begun the process of designing and implementing a cloud vulnerability plan, many more have not. Such efforts stall for a variety of reasons, including the inertia typically found in Fortune 500 companies. This inertia is often brought on by questions about who in the company makes technology decisions that affect divisions across the larger organization -- each of which likely has its own needs. There's also uncertainty about which budget gets tapped to pay for products used in multiple parts of the business.
Another factor in the slow adoption is a lack of knowledge about the strategic role and importance that cloud vulnerability management plays in the overall scheme of managing cloud security.
"Larger companies need a well-defined strategy in place for vulnerability management, but a lot of them do this stuff by the seat of their pants. It's an afterthought," said Jack Gold, president of J.Gold Associates, a consultancy in Northborough, Mass., that focuses on security and cloud environments. "But you can't pick on IT guys too much. Many of them don't get the resources they need in order to make it a priority," he said.
Money is often what bogs down a decision to move ahead with cloud vulnerability management.
"Several executives in the C-suite get into squabbles with each other about who is going to pay for it and what the ROI is on that investment," said Frank Dzubeck, president of Communications Network Architects in Washington, D.C. "But, since most ROI investments have to do with user productivity, how do you measure productivity with products that just prevent events that could negatively impact productivity?"
Common vulnerabilities in cloud environments
Cloud vulnerabilities that CISOs and other IT professionals can expect to encounter include the following:
- Misconfigurations. These are errors in security settings of cloud applications and systems, including VMs, containers and serverless environments.
- Lack of visibility. Enterprises commonly mix and match cloud technologies from various vendors, creating an interconnected and evolving IT environment. In such a diverse technology landscape, it can be difficult to recognize and mitigate cloud vulnerabilities.
- Poor access management. Digital identities far outnumber human identities in cloud environments, which makes them attractive targets for hackers. Identity-related vulnerabilities serve as initial attack vectors for cybercriminals seeking to gain entry to an IT environment.
- Insider threats. Insider threats are vulnerabilities associated with individuals with existing access to and knowledge of an IT environment, including current and former employees and business partners.
- Insecure APIs. Hackers can exploit API vulnerabilities such as inadequate access controls, weak authentication protocols and accidental data exposure.
- Lack of cloud encryption. Lack of cloud encryption is a prominent vulnerability in cloud storage, allowing unauthorized individuals to access critical data if they can infiltrate the cloud environment. When data is fully encrypted, it is transformed into a format that cannot be read without an encryption key.
Because every organization using cloud services faces these vulnerabilities, it is important that they work in cooperation with their vendors to take steps to reduce cloud risks.
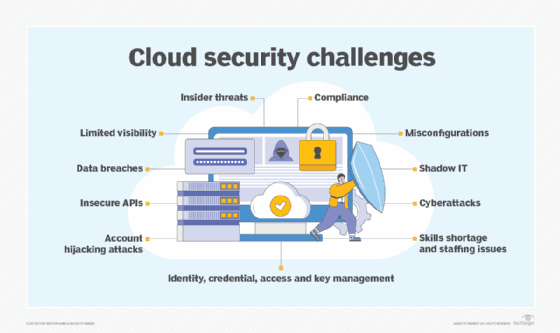
Challenges with cloud vulnerability management
It is often left to CISOs to make purchasing and implementation decisions related to cloud vulnerability management, but that is not always the case. Sometimes, it's executives in divisions far from the C-suite with authority, and there is little chance all of them agree on a universal standard for cloud vulnerability management tools.
Because of this, the managing of cloud-based vulnerabilities becomes a complex problem.
"The need to secure a hybrid and multi-cloud landscape for many enterprises is overwhelming for CISOs," said Steven Dickens, vice president and practice leader with The Futurum Group. "When you couple this with a fragmented security tools provider market, the challenges multiply. What is needed is the emergence of security platforms that address multiple threat apertures from a handful of trusted vendors," Dickens said.
Until these platforms emerge, Dickens advises organizations to remain vigilant, partner with trusted vendors and look to regulatory frameworks as mechanisms to ensure best practices. Regulations such as the Digital Operational Resilience Act in Europe for financial services and PCI DSS for credit card data are examples of standards that helped clarify complicated business practices.
Best practices for cloud vulnerability management
To stand a chance against determined adversaries, PurpleSec, a cybersecurity company based in Washington, D.C., offers three guidelines for organizations trying to manage cloud vulnerabilities:
- Conduct asset discovery and inventory. The most important step in vulnerability management is doing a comprehensive inventory of all authorized and unauthorized devices on the network, including the software installed on assets owned by the organization and those owned by third-party vendors. Once the IT team knows which assets pose the biggest risk, it can fine-tune vulnerability scanning.
- Classify assets and assign tasks. After assets are inventoried, IT must classify and rank those assets based on their true risk to the company. Risk classification helps determine the frequency of vulnerability scanning and the priority of remediation tasks. Also, it's important to assign ownership of assets so that it is understood who is responsible for an asset's associated risks; this also makes it clear that the assigned owners become liable should that asset become compromised.
- Run frequent automated vulnerability scanning. IT should conduct automated vulnerability scanning against all systems on the network at least every month or quarter. New vulnerabilities can be found daily, however, and hackers sometimes weaponize them within hours. So, if you scan monthly, your organization can theoretically be exposed to risk for up to 29 days a month.
Future of cloud vulnerability management
AI and machine learning technologies have been showing up in a variety of security offerings the past year or two, including cloud vulnerability management products. For the most part, AI deployments in vulnerability software help speed -- and otherwise make more efficient -- processes associated with remediation and scanning for vulnerabilities.
Cisco's Vulnerability Management platform, for instance, is designed around advanced algorithms along with internal and external threat intelligence. The platform can detect vulnerability changes and forecast weaponization of malware.
Cisco has also doubled down on its commitment to incorporate advanced technologies with an April 2024 announcement of Hypershield. This product, which is built from the ground up using AI, aims to protect applications and devices across public and private data centers. It is autonomous and predictive, and Cisco said the product will eventually be adapted to manage itself.
Cisco is working with Nvidia to build AI-native security offerings. The partnership involves use of Nvidia's AI-based Morpheus cybersecurity framework, which features network anomaly detection.
Also, Tenable said it is bringing new generative AI capabilities to its One Exposure Management Platform. The features enable users to ask relevant questions of its AI Assistant to get more specific guidance on security risks and threat intelligence.
Ed Scannell is a freelance writer based in Needham, Mass. He writes about a broad range of technologies and issues facing corporate IT professionals. He can be reached at ed.scannell@gmail.com.








