
sdecoret - stock.adobe.com
10 RDP security best practices to prevent cyberattacks
Securing remote connections is critical, especially in a pandemic. Enact these RDP security best practices at your organization to prevent ransomware, brute-force attacks and more.
The COVID-19 pandemic has forced many organizations to rush to upgrade their networks. Some shouldered the challenge of giving employees access to office workstations and applications from their homes for the first time, while others had to handle a big increase in the number of remote connections.
The majority of organizations using Windows machines rely on Remote Desktop Protocol (RDP). This proprietary protocol developed by Microsoft is built into Windows OSes and enables remote connections to other computers. RDP opens a "listening" socket that accepts authenticated inbound connection attempts over port 3389, providing network access to a Windows machine for a remote user over an encrypted channel. Network administrators use RDP to carry out tasks and diagnose issues on remote servers, while many employees use it to log in to their organization's network to access email and files.
However, RDP is plagued with security issues. Protecting connections that use RDP is of the utmost importance for organizations today.
RDP's history of security issues
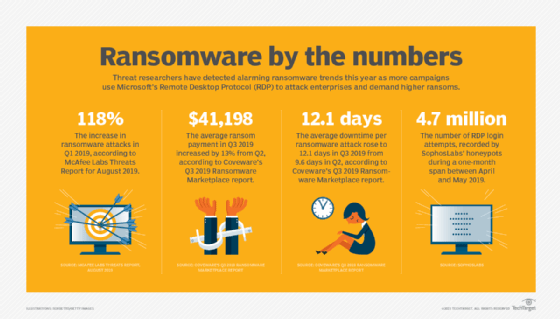
Unless properly secured before it is used, RDP can become a gateway for hackers to establish a foothold in the network, escalate privileges, install ransomware, or access and steal sensitive information. Unfortunately, for security teams, when attackers use a legitimate network service, it is easier for them to maintain a low profile and remain undiscovered.
Microsoft has repeatedly updated RDP -- also known on legacy platforms as Terminal Services -- but it still has weaknesses. Because it is so widely used, RDP is, and will remain, a popular attack vector for hackers. Web crawlers, such as Shodan, make it easy for attackers to quickly identify misconfigured RDP ports and vulnerable public-facing machines.
Brute-force attacks against RDP, where an attacker tries to gain system access through automated authentication attempts and man-in-the-middle (MitM) attacks, are widespread. Additionally, a lot of malware, such as Ryuk, Sodinokibi and GandCrab, incorporate RDP modules. Both the RobinHood ransomware attack against the city of Baltimore and the SamSam attack against the city of Atlanta were RDP-originated attacks, while the BlueKeep RDP vulnerability enables cybercriminals to remotely take over connected PCs that are not properly patched.
Implementing RDP security best practices
Because of these ongoing risks, organizations must understand how RDP works and adopt RDP security best practices to protect their networks and maintain data security. For example, all RDP instances should require multiple levels of access and authentication controls. Using a VPN to access an RDP instance, while requiring a second factor for authentication, should also be in place.
Below is a list of cost-effective RDP security best practices that IT leaders should consider implementing at their organizations:
- Enable automatic Microsoft updates to ensure the latest versions of both client and server software are installed. Prioritize patching RDP vulnerabilities that have known public exploits as well.
- Make strong passwords and two-factor authentication mandatory when using RDP.
- Implement account lockout policies to defend against brute-force attacks.
- Change the default port used by RDP from 3389 to another.
- Restrict access to the Remote Desktop port to an individual or group of trusted IP addresses and allowlist connections to specific trusted hosts. This means the server will not accept connection attempts from any IP address outside of the scope of the allowlist and stops it having to process malicious connection attempts.
- Only allow connections from computers running Remote Desktop with Network Level Authentication (NLA) over TLS. Note, NLA is not on by default in older versions of Windows. This will help protect against MitM attacks that intercept credentials.
- Enact the principle of least privilege by ensuring only employees who need remote access have RDP access and by granting the minimum level of permissions required to do their work.
- Use a VPN to enable remote users to securely access the corporate network without exposing their computer to the internet.
- Monitor RDP utilization, and flag first-time-seen and anomalous behavior, particularly failed login attempts.
- Use an RDP gateway server, which recent versions of Windows Server provide. This provides one external interface to many internal RDP endpoints, which greatly simplifies the management of tasks such as logs, TLS certificates, authentication and authorization.
Even with a strong password policy and multifactor authentication in place, RDP should never be open to the internet as it makes networks vulnerable to denial-of-service attacks and user account lockout. Once the above RDP security best practices are in place, be sure to scan the network to look for any RDP instances still directly exposed to the internet and fix them.
Even if RDP is not needed, perform regular checks to ensure RDP ports remain secured. It is critical to be aware that, while RDP is built into Microsoft OSes, it can also be installed on Apple, Linux and Android OSes.








