Search Security
Search SecurityWhat is Identity and Access Management? Guide to IAM
Businesses leaders and IT departments are under increased regulatory and organizational pressure to protect access to corporate resources. As a result, they can no longer rely on manual and error-prone processes to assign and track user privileges. That is where identity and access management or IAM comes in.
In this comprehensive guide, learn about:
- The basic components of IAM
- benefits and risks
- Technologies and tools
- Implementing IAM in the enterprise
- Vendors and products
- IAM and compliance
- And more
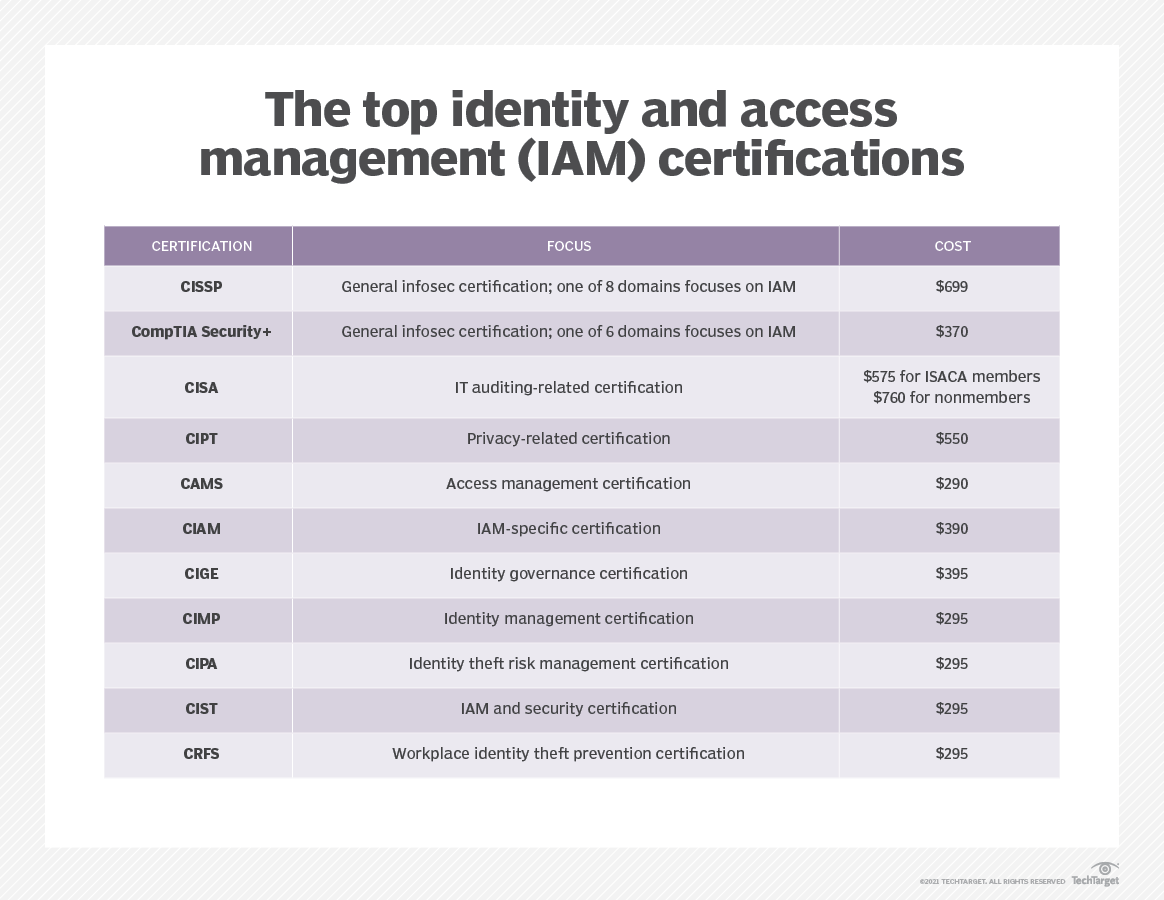
Keep your skills sharp. Here are the top IAM certifications: