
How SOCs can identify the threat actors behind the threats
Learn how SOC teams can track threat actors by understanding the factors that influence an attack, such as the type of infrastructure used or commonly targeted victims.
Detecting threats is the primary function of a security operations center. Security tools, such as extended detection and response and SIEM, help identify and raise suspicious or malicious activity to SOC analysts, who then determine the validity and severity of the activity and define appropriate response actions. The effectiveness of these tasks determines a key security metric: mean time to detect.
Responding to threats is the secondary function of a SOC. Response is often measured by the mean time taken to repair following an incident, or MTTR. The link between MTTD and MTTR is clear: The quicker you identify a threat, the quicker you can respond to it.
A threat detection and response program should initially focus on detecting threats within monitored systems and networks. Investment in this step offers comprehensive visibility, advanced analytics and an analytics engine capable of scaling high volumes of data and thus improving the MTTD metric.
Mature threat detection and response programs, however, look beyond simply identifying a threat to track indicators specific to the actors behind the threat.
Let's clear up that statement by doing some level setting. Read on to learn about the factors your SOC team should consider when tracking threat actors.
How to understand the threat
The following can be considered threats:
- exploits, for example, Log4Shell, SQL injection and CVEs;
- tactics, such as recon, lateral movement, and command and control; and
- objectives, i.e., ransomware, data exfiltration and business email compromise.
Threats can be used by any actors, and multiple actors rely on the same threats.
SOC teams should trigger detections on the aforementioned threats, as they can potentially affect an organization's operations and there's usually no legitimate use for them. Once trigger detections have been established, threat detection programs can start to look beyond the threats to understand the surrounding characteristics and behavior of the actors wielding these threats.
How to understand the threat actor
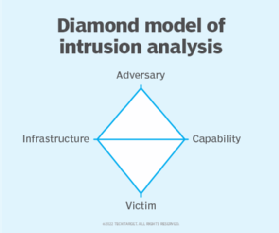
Understanding threat actors is complex but can yield significant returns in threat detection and response. Actor-specific indicators can be tracked and understood using the Diamond Model of Intrusion Analysis. It records four distinct vertices: adversary, capability, infrastructure and victim.
Adversary
The term adversary is used to describe the unique characteristics of an attacker. Examples include crypto wallet addresses or trademarks in scripts and malware. By understanding these indicators, security responders can detect and respond to threats more efficiently. Indicators need to be weighted appropriately because the majority are lower-fidelity investigation triggers, making them unsuitable for automated detection. When applied intelligently, however, they can aid analysis.
Capability
Capability is used to describe the tactics, techniques and procedures (TTPs) favored by the adversary. By understanding favored TTPs, SOCs know where to look next for detection and what attackers' next moves may be, enabling SOCs to use targeted mitigation or containment response actions to disrupt the attack.
The capability vertex also looks at the goals of an adversary. By understanding the intended end goal of the compromise, attackers can be beat -- for example, by focusing on lateral movement for a ransomware actor or scrutinizing database access if data exfiltration is the goal.
Comprehensive response actions ensure compromises are addressed holistically and not just treated as a symptom of compromise.
Infrastructure
Infrastructure describes what is used to deliver TTPs, such as IP addresses, email addresses or domains. By understanding infrastructure, SOCs can monitor connections and capture zero-day exploits or scripts that may have been previously unknown. Monitoring infrastructure has provided early warning to zero-day and emerging exploits when captured packets are periodically reviewed manually by analysts performing threat hunts.
Victim
Victim refers to who or what is being targeted. By knowing the type of organizations or systems attackers target, SOC members can take appropriate precautions to prepare for them.
Tracking the actors behind threats is a difficult endeavor and should only be performed by mature SOCs that wish to enhance their threat detection and response capabilities. When done correctly, SOCs can significantly decrease the key MTTD and MTTR metrics and even prevent compromise from occurring in the first place.
About the author
Josh Davies is product manager at Alert Logic by HelpSystems. A former security analyst and solutions architect, Davies has extensive experience working with midmarket and enterprise organizations. He conducted incident response and threat hunting activities as an analyst before working with organizations to identify appropriate security solutions for challenges across cloud, on-premises and hybrid environments.







