
tampatra - stock.adobe.com
3 steps to create a low-friction authentication experience
Passwords are no longer sufficient, but more secure authentication methods frustrate users. Explore how to create a low-friction authentication process for improved UX and trust.
New-account fraud and account takeovers are major liabilities for many organizations. Poor password practices and advanced attack techniques are no longer sufficient in confirming a user's identity.
Simultaneously, consumer behavior is becoming more fluid. Users are logging in to accounts from private browsers and using different devices and connection methods, which prompt higher false positive and challenge rates from fraud detection and authentication tools. These events also increase customer frustration, which leads to abandonment of enrollment, login or purchase.
Gartner predicted that, by 2022, digital businesses with a smooth customer journey during identity corroboration will earn 10% more revenue than comparable businesses with an unnecessarily frictional customer journey. It is time we assume the positive intent of our users and rebalance risk and trust.
Here are three steps security and risk management leaders should take to enable a low-friction authentication experience.
1. Implement bot detection technologies
While bad bots have long been recognized as problematic, recent evidence has shown they are well organized and are largely driven by the goal of monetary gain. Many organizations have responded to bot attacks by forcing CAPTCHAs on sensitive customer interaction points.
However, traditional CAPTCHAs with jumbled numbers and letters and the more user-friendly image-based CAPTCHA can still be beaten by attackers and cloud-based analysis tools. Customers are also more likely to abandon an interaction when a CAPTCHA request appears.
Bot detection systems are a better method of circumventing these attacks. Such systems have matured from standalone products to an integrated part of many enterprise web application firewalls and content delivery networks. These products detect and mitigate bot attacks on sign-up and sign-in pages, as well as on protected or sensitive content. The burden to "prove humanity" is removed from the customer and placed where it belongs: the domain of the technology intended to support the integrity of a web property.
By actively detecting and separating bot traffic from human traffic, organizations can reduce or eliminate the need for active tests of humanity. This fosters greater trust between the customer and business, strengthening loyalty and engagement.
2. Focus on the behavior of legitimate customers
With an estimated 60%-70% of consumers using the same username and password to access more than one account, it is clear that password privacy is long dead. This means users' ability to authenticate their accounts with a password provides little proof of legitimacy. Likewise, due to the high percentage of legitimate customers that fail to enter the correct password -- particularly for sites requiring complex passwords -- password failure alone cannot be considered a strong indicator of risk.
Implementing behavioral biometric technologies in combination with more traditional authentication signals can enable an elevated level of trust. These technologies observe and analyze users' activity within a digital property, such as the way they type, the placement and timing of their mouse movements or their swipe pattern on a mobile device.
For organizations with frequent user interactions, such as banks, gaming sites and e-commerce retailers, behavioral norms can be established for each user. Significant variations from a user's normal patterns can indicate an account takeover or unauthorized use. For organizations with less frequent interactions, this technology can still add value when focused on behavioral analytics rather than user identity corroboration. It does this by creating a baseline of normal behaviors, against which any interaction can be compared.
Approaching each interaction with the question, "Is this a human or a machine?" is the first step in the separation of risk populations. If it is a human, deciding if it appears to be a known or unknown customer base enables further segmentation of known and low-risk customers from unknown and moderate-risk users. From that point, assuming the perceived known customer is, in fact, a legitimate customer creates a foundation of trust. Continuous analysis of the customer's behavior provides ongoing validation of that trust.
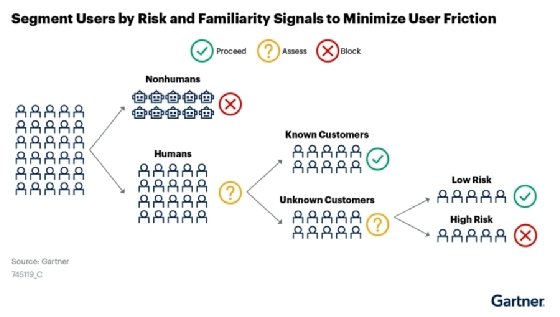
For the majority of human-to-digital business interactions, the human user has positive intent. Shifting the paradigm of digital trust to start from that assumption, along with utilizing behavior analytics to flag indicators of abnormal behavior, will improve customer experience and lower false positive rates.
3. Implement an adaptive approach to authentication
When designing authentication processes and risk tolerances, many organizations take a "moat and castle wall" approach. Once inside the "castle," a malicious actor will have access to everything of value, so developers front-load customer experience with a requirement of absolute trust.
For most organizations, legitimate users logging in to an existing account rarely intend to execute high-risk actions. Rather, the user is more likely to perform a mundane and low-risk activity, such as reviewing account balances or making a payment to a known payee.
The castle wall mentality often results in legitimate customers walking away, as they lack the patience to repeat a multistep authentication process. Being asked knowledge-based verification questions or performing repeated email or mobile authentication requests seem time-consuming at best and excessively difficult at worst.
The choice is no longer between high security and a seamless experience. A system that utilizes context-aware risk classifications can offer an experience where the required level of friction matches the level of risk. For example, a user that is identified as most likely human, logging in to an account from a low-risk device and with some familiar behavioral signals, may be allowed to access their account even from a new IP address. Every avoided customer challenge is another step toward building trust.
Organizations can build assessment gates at points of high risk, such as changing an email address, adding a new deposit account or turning off account notifications. These enable the organization to determine, at strategically placed gates, whether the trust is high enough for the action being requested. If it is not high enough, this is the appropriate time for a customer challenge, be it a mobile push, an active biometric authentication mode or a text message passcode.
The key to a successful authentication and risk management transformation is to reframe the business risks involved. The greatest risk to a business is no longer fraudulent activity; the greatest risk is impracticality and loss of customers.
About the author
Tricia Phillips is a senior research director at Gartner Inc. covering user authentication with an emphasis on continuous and adaptive risk assessment to protect UX and prevent advanced account takeover threats. Phillips and other Gartner analysts will provide the latest research and advice for security and risk management leaders at the Gartner Security & Risk Management Summit 2021, taking place Sept. 20-22 in Orlando, Fla.






