
Sikov - stock.adobe.com
Why 2023 is the year of passwordless authentication
Passwords may soon be relegated to the past thanks to IAM vendors' efforts to create passwordless login options. Here's why 2023 should be the year of passwordless authentication.
The explosion of available services has overwhelmed users with accounts and passwords to remember, which has led to them creating simple passwords and reusing passwords across multiple accounts.
Unfortunately, short and easy-to-remember passwords are insecure. Using brute-force methods, a hacker can determine an eight-character password in under an hour. Malicious hackers also create dictionaries with hundreds of millions of existing usernames and passwords stolen during data breaches.
Threat actors may also masquerade as a trustworthy source to force users to inadvertently reveal their usernames and passwords. Known as phishing, these social engineering attacks target email, malware, typosquatting -- for example, a malicious website using the URL gogle.com instead of google.com -- and SMS texts.
To protect against brute-force and dictionary attacks, passwords need to use uppercase and lowercase letters, numbers and symbols, and be at least 14 characters long. Following these guidelines makes passwords harder to remember, leading to password reuse. This, in turn, leads to credential stuffing attacks, where malicious hackers take advantage of password reuse and a known username to attempt to log in to multiple services.
Multifactor authentication continues to improve
Passwords are a form of knowledge-based authentication. For a user to prove they are who they claim to be, they need a secret -- the password -- that has been previously stored by the service.
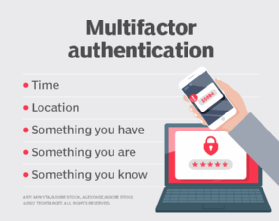
Multifactor authentication (MFA) is a technique designed to strengthen the authentication process by adding possession-based authentication to knowledge-based authentication. A service can only authenticate a user when they prove they have knowledge of the shared secret in addition to something they have or are.
The ubiquity of smartphones makes the phone the ideal physical item for possession-based authentication. To prove a user is in physical possession of the device, the service sends a message -- a challenge -- to the phone, which the user must then interact with.
While MFA serves as an improvement over traditional password-based authentication, many MFA techniques have their own security issues:
- Verification messages sent via email are easily intercepted by third parties.
- SMS-based MFA is susceptible to SIM swapping, whereby an attacker convinces the phone company to register the attacker's physical device with the victim's phone number.
- Push notifications can be defeated with prompt bombing, whereby the attacker attempts multiple logins, hoping that the victim mistakenly acknowledges a request.
MFA also increases friction by requiring the user to go through a multistep process: entering the password, waiting for a challenge and then entering the challenge.
Passwordless authentication comes to the rescue
Eliminating shared secrets removes the intrinsic weakness of password-based authentication and MFA. A secure form of possession-based authentication is the best alternative. Passwordless authentication based on FIDO standards is considered the archetype.
FIDO passwordless authentication is based on public-key cryptography. This asymmetric cryptography uses pairs of keys; any system can encrypt a message using the public key, and the message can only be decrypted with the private key. This system also works in the reverse direction: Any message encrypted by the private key can only be decrypted by the public key. As long as the private key remains private, the public key can be shared without compromising security.
With FIDO passwordless authentication, when a user registers with a service, the user generates a public/private key pair. The public key is shared with the service, and the private key is kept in a hardware-based vault on the device.
During the authentication process, the service sends a challenge to the user. The user encrypts the challenge with the private key and sends the encrypted challenge back to the service. If the service successfully uses the public key to decrypt the challenge, the user has proved who they are.
What prevents an attacker from using a stolen device to authenticate to the service? The user's hardware vault and private keys are protected by either a PIN or biometrics, such as a fingerprint or facial recognition. Biometrics or PINs never get shared or transmitted across the network. This ensures only the legitimate user can access the private keys and is in possession of the device.
Thus, FIDO passwordless authentication is more secure than password-based or multifactor authentication. FIDO passwordless authentication also removes friction from the process: Users only need to look at the phone's camera, swipe their finger or enter a PIN.
Passwordless authentication in the real world
While FIDO protocols have been standardized since 2019, a passel of startups -- including 1Kosmos, Acceptto, Axiad, Beyond Identity, Hypr, Nok Nok Labs, Secret Double Octopus, Stytch, Transmit Security and Trusona -- are innovating products to add passwordless authentication to apps.
Identity and access management (IAM) providers haven't been idle, either. Auth0, CyberArk, ForgeRock, IBM, JumpCloud, Microsoft, Okta, OpenText, Oracle, Ping Identity, SailPoint, Saviynt and WSO2 have added passwordless authentication to their workforce and customer IAM products.
Thanks to the above, organizations can now transition to passwordless authentication. A survey from Enterprise Strategy Group (ESG), a division of TechTarget, revealed the following:
- 31% of respondents said passwordless authentication is their top identity-related activity;
- 34% of respondents said passwordless authentication was among their top three identity-related activities; and
- 54% of total respondents have started to transition to passwordless authentication.
Of organizations transitioning to passwordless strategies, more than half experienced a significant positive impact to risk reduction and improved UX. Almost two-thirds reported increased efficiency for IT and security teams.
With these benefits and the ability for organizations to move to a passwordless approach for their IAM systems and applications, 2023 can and should be the year of passwordless authentication.






