
sarayut_sy - stock.adobe.com
What's the answer for 5G security?
Learn about the planning of 3GPP in developing specifications for 5G security in this synopsis of 5G Americas' white paper, 'The Evolution of Security in 5G.'
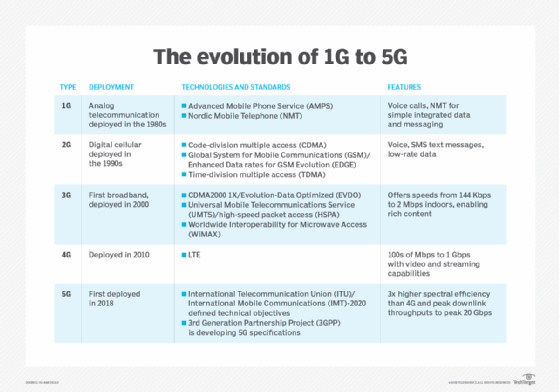
5G, the next generation of mobile wireless technology, brings greater speed, enabling more data capacity; lower latency, enabling more critical communications and responsiveness; and the ability to connect a lot more devices at once for the massive IoT.
But what does it mean for security?
The fact that 5G will support many different access networks (ANs), including 2G, 3G, 4G and Wi-Fi, means that 5G perhaps inherits all the security challenges.
5G is the first mobile architecture designed to support multiple, specific use cases, each with its own unique cybersecurity requirements. For example, 5G will enable massive IoT applications, such as traffic sensors and vehicle-to-infrastructure services, that are the foundation for smart cities. It's critical hackers cannot access data, hijack IoT devices or perform distributed denial-of-service attacks in smart city scenarios.
Security isn't new to the mobile industry. There is a long-standing emphasis on security, creating a strong market differentiator against other wireless technologies -- some of which have inherently more vulnerable network architectures. Mobile's use of licensed spectrum provides a layer of protection against eavesdropping on data, voice and video traffic. Network segmentation is often used in enterprises to mitigate security risks. Now, 5G introduces the concept of network slicing, which provides mobile operators with segmentation capabilities that were not possible with previous generations.
5G security standards
The 3rd Generation Partnership Project (3GPP), the global standards body that works on specifications for mobile technology, approaches security by uniting seven telecommunications standard development organizations. Its working groups have created standardized security features and mechanisms for 3G, 4G and now 5G technologies. The SA3 Working Group is responsible for security and privacy architectures and protocols in 3GPP systems. The latest 5G security specification published by SA3 defines the security architecture, features, mechanisms and security procedures performed in the 5G core and 5G New Radio (NR).
Increased home control. Home control is used for device location authentication when a device is roaming. It enables a home network to verify if a device is in the serving network (SN) when the home network receives a request from a visited network. Home control was added to address vulnerabilities found in 3G and 4G networks where networks could be spoofed: sending false signaling messages to the home network to request the International Mobile Subscriber Identity (IMSI) and device location -- data that could be used to intercept voice calls and text messages.
Unified authentication framework. In 5G networks, authentication is access-agnostic; the same authentication methods are used for 3GPP and non-3GPP ANs -- for example, 5G radio access and Wi-Fi access. Native support of Extensible Authentication Protocol (EAP) enables new plugin authentication methods to be added in the future without impacting the SNs.
Security anchor function. 5G introduces the anchor key concept with the security anchor function (SEAF). It enables device reauthentication when it moves between different ANs or SNs without having to run the full authentication method -- for example, authentication and key agreement (AKA). This reduces the signaling load on the home network Home Subscriber Server during various mobility services. The SEAF and the access and mobility management function (AMF) can be separated or colocated. The SEAF and AMF are colocated in 3GPP Release 15.
Subscriber identifier privacy. In 5G, each subscriber is allocated a globally unique subscription permanent identifier (SUPI). SUPI formats include the IMSI and network access identifier. In 3G and 4G networks, the IMSI is disclosed when a device is going through an attach procedure before the device is even able to authenticate with the new network -- a vulnerability in 3G and 4G networks. The SUPI is never disclosed over the air in the clear when a mobile device is establishing a 5G connection. Instead of disclosing the SUPI, a subscription concealed identifier (SUCI) is used until the device and network are authenticated. After authentication, the home network discloses the SUPI to the SN. This procedure prevents IMSI catchers -- also known as false base stations or stingrays -- from retrieving a subscriber's identity. This is accomplished by forcing a device either to attach to a rogue base station or perform an attachment process to the operator's base station while sniffing the unencrypted traffic over the air.
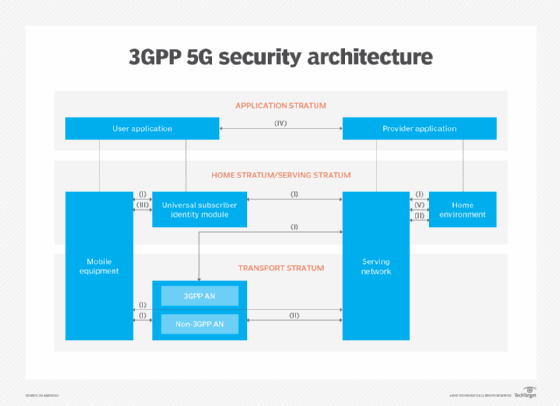
3GPP 5G security architecture
The 3GPP 5G security architecture includes many network architectural elements and concepts, including the following:
- Network access security (I) is the set of security features that enables user equipment (UE) -- any devices used directly by an end user to communicate, such as a cellphone, laptop computer or tablet -- to authenticate and access services, including 3GPP access and non-3GPP access, and particularly to protect against attacks on radio interfaces. It also includes security context delivery from the SN to UE for access security.
- Network domain security (II) is the set of security features that enables network nodes to securely exchange signaling data and user plane data.
- User domain security (III) is the set of security features that secures the user access to mobile equipment (ME).
- Application domain security (IV) is the set of security features that enables applications in the user domain and in the provider domain to exchange messages securely.
- Service-based architecture (SBA) domain security (V) is the set of security features that places heavy emphasis on services as the primary architecture component used to implement and perform business and nonbusiness functionality. SBA domain security features include network element registration, discovery and authorization security aspects, and protection for service-based interfaces.
- Visibility and configurability of security (VI) is the set of features that enables the user to know if a security feature is in operation.
End-to-end core network interconnection security requirements
To ensure secure network connections, systems must do the following:
- support application layer mechanisms for addition, deletion and modification of message elements by intermediate nodes;
- provide end-to-end confidentiality and integrity between source and destination networks for specific message elements identified in the present document;
- have minimal impact and additions to 3GPP-defined network elements;
- use standard security protocols;
- cover interfaces used for roaming purposes;
- account for considerations on performance and overhead;
- prevent replay attacks;
- cover algorithm negotiation and prevention of bidding down attacks; and
- account for operational aspects of key management.
To protect messages sent over the N32 interface, which provides interoperator network connectivity that might traverse the Internetwork Packet Exchange, 5G system architecture implements security edge protection proxy (SEPP) at the perimeter of a public land mobile network (PLMN). SEPP receives all service layer messages from the network function and protects them before sending them outside the network on the N32 interface. Additionally, it receives all messages on the N32 interface and, after verifying security, forwards them to the appropriate network function.
Authentication framework
Primary AKA procedures enable mutual authentication between UE and the network. They also provide keying material that can be used between UE and the SN in ensuing security procedures. The keying material generated by the primary AKA procedure results in an anchor key, the KSEAF, which is provided by the authentication server function of the home network to the SEAF of the SN.
Keys for more than one security context can be derived from the KSEAF without the need of a new authentication run. For example, an authentication run over a 3GPP AN can also provide keys to establish security between UE and a non-3GPP interworking function (N3IWF) used in untrusted, non-3GPP access. Keys must be secure, unpredictable, random and offer true entropy for complete encryption.
UE and the SN should support EAP-AKA and 5G-AKA authentication methods. Home network operators select the authentication method. The universal subscriber identity module (USIM) should reside on a universal integrated circuit card (UICC), which may be removable or nonremovable.
For non-3GPP ANs, USIM applies if the terminal supports 3GPP access capabilities; the credentials used with EAP-AKA and 5G-AKA for non-3GPP ANs should reside on the UICC. EAP-AKA and 5G-AKA are the only authentication methods supported in UE and the SN.
Granularity of KSEAF binding to SN
Primary AKA procedures bind a KSEAF to the SN. This prevents one SN from claiming to be a different SN, thus providing implicit authentication to UE. This authentication must be provided to UE regardless of the AN technology; it applies to 3GPP and non-3GPP ANs.
The KSEAF binding includes a parameter called serving network name in the chain of key derivations that leads from the long-term subscriber key to the KSEAF.
Mitigation of bidding down attacks
An attacker could attempt a bidding down attack by making UE and network entities believe that the other side does not support a security feature, even when both sides do support it. SEPPs help ensure that such bidding down attacks can be prevented.
UE's 5G security requirements
In order to ensure 5G security, UE must support settings and mechanisms, including the following:
- man-to-machine interface settings where users can disable use of one or more of the ME's radio technologies for radio access network (RAN) access, regardless of PLMNs;
- man-to-machine interface settings enabling users to reenable use of one or more of the ME's radio technologies for RAN access, regardless of PLMNs;
- ability for the home operator to reallow selection of one or more of the ME's radio technologies for RAN access, regardless of PLMNs;
- for a prioritized service -- for example, emergency services or mission-critical services -- UE supporting a mechanism to automatically override user- and network-disallowed radio access technologies when there are no PLMNs on the allowed radio technologies identified that UE can access; and
- upon power cycle or when the USIM is disabled, UE configuration of enabled or disabled radio technologies configured by the user remaining as it was before the USIM was disabled.
5G identifiers
As mentioned, each 5G subscriber is allocated one globally unique 5G SUPI for use within the 3GPP system, and the SUCI preserves the privacy of the SUPI. 5G systems support subscription identification independently of UE identification. Each piece of UE accessing the 5G system is assigned a permanent equipment identifier and may be given a 5G globally unique temporary identifier, or 5G-GUTI, to ensure confidentiality.
The subscriber identification mechanism shown in the figure may be invoked by the SN when UE cannot be identified by its 5G-GUTI. Using subscription temporary identifiers is an important element of 5G security.

5G security mechanisms
Subscriber privacy. Subscriber privacy is important to mobile network architecture security aspects. For example, UE must support 5G-GUTI and the null scheme; the SUPI should not be transferred in cleartext over 5G RANs, except routing information, such as mobile country codes and mobile network codes; ME must support at least one non-null scheme; and the home network public key must be stored on the tamper-resistant secure hardware component.
Home network operators are responsible for provisioning and updating the home network public key in the tamper-resistant hardware. Subscriber privacy enablement is controlled by the home network of the subscriber.
Secure steering of roaming. Native support for secure steering of roaming was added in 3GPP Release 15. This enables a home network operator to steer its roaming customers to its preferred visited PLMNs to enhance roaming customers' experience and reduce roaming charges.
UE-assisted network-based detection of false base stations. UE in radio resource control connected mode sends measurement reports to the network based on configurations provided by the network. These reports have security values useful for detection of false base stations or SUPI/5G-GUTI catchers.
Why all the additional security for 5G?
Today's networks experience a wide variety of threats from different sources and attack routes. The quantity and quality of these attacks increase each year as more points of vulnerability are available in networks, UE and devices. With massive IoT, the threat surface becomes quite broad, especially when it comes to IoT services, applications, nodes and platforms, networking and transport, or IoT devices themselves.
Sophisticated attackers understand mobility and edge threats, and network cores, secure gateway internet LAN firewalls, and roaming and air interfaces present plenty of opportunities for attack. Each vulnerability point potentially presents several different types of threats -- such as message blocking, denial of service, man-in-the-middle techniques and more -- that can attack authentication, integrity, network availability and privacy. For example, an attack involving a wireless subscriber's privacy has numerous points in which a customer's device SUPI number could be exposed or captured, as illustrated below.
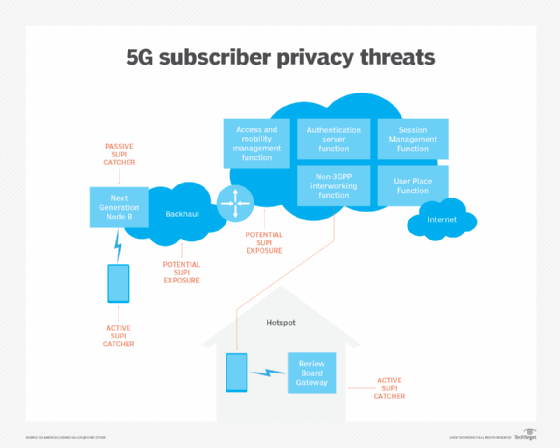
With so many points of exposure and vulnerability threats, security can put significant strain on network operator resources. Fortunately, wireless operators don't need to reinvent the wheel. 5G security protocols and specifications build upon and are compatible with key frameworks developed in 4G LTE. In addition, 5G NR can plug in to a 4G core and coexist with 4G radios as part of an existing network, even as edge computing creates additional nodes at a network's edge.
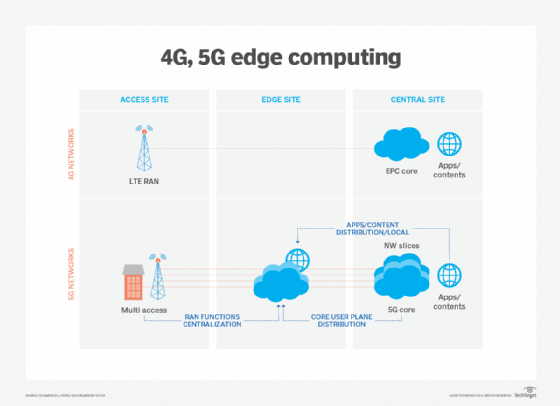
5G offers new security capabilities for networks that use network slicing via software-defined networking, primarily in enterprise situations. In network slicing, virtual networks are created, allocating compute, spectrum and other data management capabilities to provide just the resources necessary. 5G offers resource isolation, which lets a slice remain available when others may become overloaded, and security isolation, which ensures a slice is quarantined -- much like bulkheads in a submarine will prevent it from sinking.
The realization is, in an interconnected society, the risk of attack is high. Engineering and security professionals are working to keep 5G networks, devices and communications secure.
For more information, download "The Evolution of Security in 5G" from the 5G Americas website.






