We talk a lot about access and authentication, but what about revoking user access?
Google hopes to make it easier with their proposed Continuous Access Evaluation Protocol.
As authentication continues to improve, another problem to examine is around ending user sessions, especially with automation. This is a continuation our conversation around the importance conditional access and zero trust.
Ending user sessions
Right now, a user is usually authenticated just when they log in; and, as long as they stay active, the session doesn’t end. What do you do if a session needs to be ended for some reason, like the device enters a risky security state, or the user’s authorization needs to be revoked (which is a nice way saying they were dismissed)?
At Oktane 2019, it became clear to me that simply deprovisioning employees and partners from systems remains complicated, so what’s the experience around ending user sessions right now?
When I looked into how admins could end user sessions, I dug into the developer documentation for several popular SaaS applications and IdPs. All sorts products and platforms, ranging from Salesforce, to Citrix, to Windows PowerShell, and others allow admins the ability to end a user session. With Okta, you can end user sessions through proprietary APIs or within Okta itself, but for generic SAML-enabled applications, current standards have some limitations.
So, yes, you can end user sessions, but it isn’t always clear how immediately it ends the session and no one seems to offer the ability to automate the process. One example of how complicated it can be: an admin disabled a fired employee’s AD, but the employee was able to continue to use their company email for hours afterward.
Automating user session management
This is where Google hopes their proposed Continuous Access Evaluation Protocol could help. The idea with CAEP is how, as everyone moves more into the cloud and onto mobile devices, user sessions authentication should involve dynamic data (e.g., location, device hygiene, etc.). Authentication shouldn’t be a static decision made when the user wants to login. So, this could make it easier to end a user session if malware is detected on a device, as mentioned earlier.
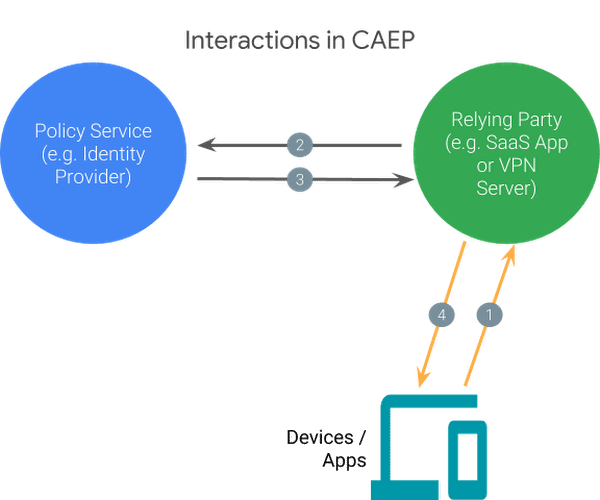
CAEP would provide vendors with a publish-and-subscribe approach to user sessions, which relay data about live sessions to the app and IdP, as opposed to the current style of “fire and forget,” according to Google. If it works as Google believes the process would work, it'd go like this:
“An endpoint security service monitoring the device obtains information about the suspicious activity. It publishes a message that invalidates all sessions from that device. All service providers subscribed to those sessions then invalidate their internal sessions from that device, and the user needs to re-authenticate from that device in order to proceed.”
The Continuous Access Evaluation Protocol allows for multiple services to subscribe, making it possible to end all of a user’s active sessions.
Watch this space—the identity space is very active
I’ve only become familiar with the industry over the past year, and in that time, I’ve seen an impressive amount of advancement in identity standards, such as WebAuthn. So, I was surprised automatically ending user sessions isn’t really a thing, let alone easy. Continuous Access Management Protocol might not be the option with that ability, but it’s one that stuck out to me.
Authentication continues to improve, so ending user sessions is something I figured would have been in a better place than it currently is. However, it can take a while to implement changes, so I expect to be waiting a little while longer. As focus turns toward contextual access and other methods handling access and authentication, it would be useful for automatically ending user sessions to come along with that.






