Making a case for the cybersecurity data fabric
When it comes to data, context is everything. Learn how a cybersecurity data fabric can supercharge a security team's ability to see the big picture.
Information, data and context are the weapons that cybersecurity teams use to battle adversaries daily. Yet, using cybersecurity data in the modern enterprise has become increasingly difficult. The data is often scattered among dozens of point technologies, fragmented with use-case-specific interfaces, and siloed between IT, security and application teams with little capability to support cross-team functionality. Without a way to collect, process, normalize and analyze cybersecurity data, insights are often missed, resulting in ineffective detection and response.
Ephemeral cloud-native infrastructure, workloads that spin up and down rapidly, AI-generated code and nondeterministic prompting of applications create an environment where traditional threat and exposure management approaches are doomed to fail. A new centralized data storage and analysis capability that collects and continuously updates all state and event data pertinent to an organization's assets, vulnerabilities, exposures and threats is necessary for success. AI-driven holistic analysis can provide actionable recommendations to lessen enterprise cyber risk, but not without a strong data foundation. Let me introduce you to the cybersecurity data fabric.
What is a cybersecurity data fabric?
A cybersecurity data fabric, in simple terms, is the foundational ingestion, storage and data normalization component of an effective threat and exposure management process. It's an architectural approach to cybersecurity that promises unification and better overall security capabilities. Think of a cybersecurity data fabric as a central nervous system for your cybersecurity technology ecosystem. It's a unified and intelligent data management framework explicitly designed for cyber-related actionable input and output.
A cybersecurity data fabric provides a number of unique features to the security team that takes the time and energy to create such a platform. First and foremost, it is a unified view of all relevant security data enriched and enhanced by infrastructure state and threat intelligence. No more bouncing through a dozen tools to locate and manually correlate the disparate data sets required for a security operations team to do its job. The data is well integrated from multiple other sources and is always up to date if done correctly. It's accessible and democratized, providing security-relevant context to every team in the enterprise, from developers and engineers to security teams and architects. The use cases for the resultant context created by a cybersecurity data fabric are limited only by the team's imagination.
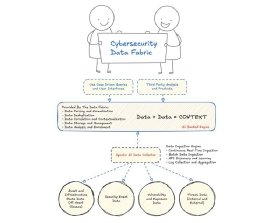
Unlike traditional data lakes or warehouses, which are typically general-purpose, a cybersecurity data fabric provides a much more powerful analysis and enrichment process. The capability connects multiple data pieces to form a contextual view that is highly valuable for common cyber use cases. In this example, data plus data equals context, and context helps us make more informed decisions.
The cybersecurity data fabric can be divided into two distinct process-driven components: collecting pertinent cybersecurity data and surfacing cybersecurity context.
Collecting pertinent data: Agentic AI data collection
The current process for ingesting data into a cybersecurity fabric involves direct connections and integrations with a broad range of cybersecurity, infrastructure, development and application tooling. Polling and batch-based collection of as much pertinent data as possible provides a semi-continuous, near-real-time update of the context used to make effective cybersecurity decisions. This process often requires custom connector development and a reasonably high level of ongoing maintenance, as APIs for access change over time. The ingestion itself, while challenging, pales in comparison to the effort necessary to normalize, standardize and deduplicate data once it has entered the fabric itself. Today's fabrics almost exclusively use this approach to data ingestion, with a significant team dedicated to the engineering improvement and maintenance of the platform.
The future of data ingestion for cybersecurity data fabrics is autonomous and AI-powered agents that can adapt and learn an environment. While this might sound a bit like science fiction, in the future, agents will be deployed whose entire purpose is the detection of new systems and infrastructure. They will learn how to connect, collect and analyze the available data within that target for use within the context created by the fabric. They will possess the intelligence required to proactively discover all relevant data sources in a digital ecosystem, including previously unknown assets. The agent will be able to understand data semantics, adapt to evolving or changing APIs and establish and learn new connections dynamically, resulting in a decrease in maintenance and total overhead of operations.
While we aren't there today, we must remember the direction of the cybersecurity data fabric ingestion capabilities to get the best results possible from our deployments today. Agentic AI-based data ingestion will ultimately improve the security team's effectiveness, as it will ensure the visibility and telemetry that informs cybersecurity decision-making processes is always up to date and highly accurate.
Creating cybersecurity context: AI-backed fabric engine
The cybersecurity data fabric analysis engine is the centralized computing system responsible for analyzing and enriching ingested data, eventually creating the ultimate awareness of cybersecurity context. The analysis engine is instrumental in parsing ingested data, deduplicating and normalizing it, and intelligently connecting it with adjacent data to create security wisdom.
The engine emulates the human activity of consuming disparate data sets from multiple tools by hand and developing a deeper understanding of what's actually happening in the digital ecosystem. Cybersecurity data fabrics available today use a combination of rules, statistical analysis and AI algorithms to deliver the foundational context that the security team requires to operate day-to-day.
Why enterprise security teams need a cybersecurity data fabric
The modern-day, decentralized and ephemeral enterprise infrastructure is highly complex and vulnerable to a multitude of sophisticated threat and attack models. Without a cybersecurity data fabric, staying ahead of attackers is becoming increasingly impossible, using our current siloed, multitool approach. Numerous benefits come from the use of a cybersecurity data fabric, including the following:
- Breaking down silos that limit team effectiveness. Enterprises today have dozens of distinct cybersecurity technologies, each with its own unique set of data. Unifying cybersecurity-related data into a single fabric removes barriers between teams and creates an environment of sharing that increases security program capabilities.
- Improving the speed and effectiveness of incident response and threat-hunting processes. Incident response requires a significant amount of data access to contextualize indicators of compromise and deduce activity that adds risk to the business. Most isolated activities do not indicate an active incident or threat, but analyzing a series of actions or events together can offer important context. Threat hunting and incident response both improve with the adoption of a cybersecurity data fabric approach.
- Switching from a reactive to a proactive stance around risk reduction. The risk reduction process has traditionally been one in which exposures and vulnerabilities were discovered and mitigated based on prioritization strategies. Looking at the risk of a particular exposure without the context of mitigating factors, infrastructure knowledge and active threat data makes prioritization far less accurate and turns risk reduction into a reactive procedure. Moving to a cybersecurity data fabric enables risk reduction to become proactive and eventually preventive, as threat and asset data is analyzed in real time and compared against known threats and actions.
How to get started with a cybersecurity data fabric
If your organization is looking to purchase a cybersecurity data fabric, it must first define the specific security objectives and use cases it hopes to achieve with the platform. This includes documenting security pain points, identifying the types of processes you want to augment with automation and developing a thorough understanding of the threats and risks you need to mitigate. Improved threat detection, faster incident response and enhanced capabilities around reporting and governance can all be achieved with a strong cybersecurity data fabric offering.
With defined goals, begin to evaluate the commercial options available on the market, focusing on vendor prebuilt integrations and what cybersecurity context the technology can surface. The breadth and depth of the data normalization and enrichment capabilities will determine how well the offering matches your analytical requirements.
Once your organization has identified its vendor of choice and the technology it wants to implement, the focus shifts to deployment. One significant advantage of purchasing a data fabric versus building one in-house is the availability of prebuilt connectors and data processing pipelines. Work closely with the vendor to connect various data sources to the platform and configure it to address your organization's use case specifically. Adopt an iterative approach and do not attempt to boil the ocean. Find small outcomes that help your security team execute well, providing quick wins to the project. Solve a singular security challenge and gradually expand the scope of the data fabric implementation to include more data sources and address additional use cases. Use the vendor's training and support as much as possible during this process.
Cybersecurity data fabrics are the path to cyber success
If your organization needs to use deep knowledge of its environment to create valuable security context, a cybersecurity data fabric presents a clear path forward. By defining objectives, evaluating vendor offerings and ensuring alignment with their technology infrastructure, enterprise buyers of cybersecurity data fabrics can quickly increase the pace and effectiveness of their security programs.
Cybersecurity data fabrics enable improved threat detection, faster incident response and a more comprehensive understanding of the organization's security posture. This ultimately empowers security teams to proactively defend against the ever-evolving cyberthreat landscape and embrace an AI-driven future for their security operations.
Tyler Shields is a principal analyst at Enterprise Strategy Group, now part of Omdia. He has more than 25 years of experience in cybersecurity technologies and markets, with emphasis on vulnerability management, risk analysis, threat identification and offensive security technologies.
Enterprise Strategy Group is part of Omdia. Its analysts have business relationships with technology vendors.








