- Share this item with your network:
- Download
Information Security

alphaspirit - Fotolia
Verizon DBIR 2017: Basic cybersecurity focus misplaced
Basic cybersecurity measures like limiting password reuse and implementing multifactor authentication could be big benefits, according to the Verizon DBIR 2017.
Editor's note: this is part two of a two-part series covering the Verizon DBIR 2017. You can read part one, regarding the rise of ransomware and pretexting here.
A growing theme across the recent years of the Verizon Data Breach Investigation Report (DBIR) is how the lack of basic cybersecurity plays a part in many of the breaches and security incidents every year, but Verizon suggested vulnerability patching may not be as impactful as once thought.
Dave Hylender, senior risk analyst at Verizon Business, told SearchSecurity the aim of the Verizon DBIR was to focus on the data and to "keep opinion out of it" whenever possible, because it could be difficult to give cybersecurity recommendations to the diverse audience of the DBIR.
However, experts noted that the data alone was enough to highlight basic cybersecurity practices that were failing, such as limiting password reuse and implementing multifactor authentication (MFA).
According to the 2017 Verizon DBIR, 81% of breaches leveraged "stolen passwords and/or weak or guessable passwords," which marks an 18% increase from last year. Hylender said the issue was exacerbated by the fact that almost every website asks you to log in before even minor tasks, so even if the credentials aren't that important to one site, they could "be incorporated into a massive attack" based on password reuse.
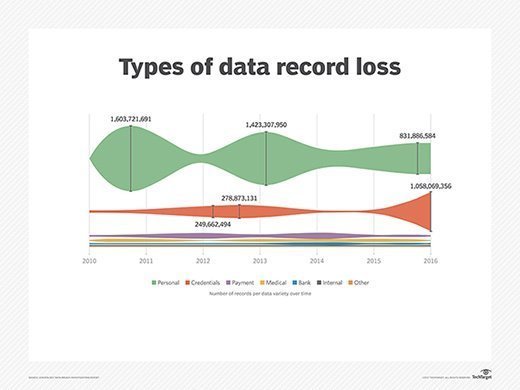
"Data types that are apt to be stored in bulk have some monster numbers associated with them, with personal data and credentials totaling in the billions some years," Verizon wrote in the report. "It should be noted that some of the credentials may be hashed, and some may be salted to strengthen the encryption, but the sheer volume of records speaks ... well volumes."
Does MFA aid in web application attacks?
Verizon also found that web application attacks were the No. 1 attack pattern in confirmed breaches, with almost twice as many instances (571) as the second-ranked pattern, cyberespionage (289). And the use of stolen credentials was the most frequent hacking method used in web application attacks.
Rick Holland, vice president of strategy at San Francisco-based Digital Shadows, said this is especially dangerous because password reuse and "credential theft can be another force multiplier for attackers."
"There are so many attack options, and credential exposure has been industrialized, so it isn't surprising to see it continue to dominate the headlines," Holland told SearchSecurity. "Exposed email address can be targeted for deploying malware. These large data sets can also be used for extortion. Credential stuffing can be used to automatically submit usernames and passwords to log in to user accounts. Credential reuse for corporate accounts can result in account takeovers, pivoting from a consumer account to a domain account."
Experts, however, were divided on whether there was hope for improving basic cybersecurity around credentials, and Verizon even noted the risks of SMS-based MFA.
David Shearer, CEO of (ISC)2, based in Clearwater, Fla., said he would at least like to "think there's hope for reducing credential compromises by leveraging MFA.
"There's still resistance by many users to use MFA because, depending on the solution employed, users complain it's any additional step that they find inconvenient. MFA properly deployed does not have to affect productivity. Leadership needs to support their respective cybersecurity program by setting an example of using strong passwords and MFA," Shearer told SearchSecurity via email. "That said, the bad actors will continue to evolve their tactics, and MFA may not be enough at some point. I think the first step for any organization is to do all you can to ensure you're not an easy target by getting the fundamentals in place and sustained. From there, you can mature your cybersecurity program."
Ilia Kolochenko, CEO of Geneva-based web security company High-Tech Bridge, was less optimistic.
"We cannot change people, and people will always prefer simplicity to security by using same, similar or predictable passwords. We can change a technology but not really a human," Kolochenko told SearchSecurity. "MFA is often incorrectly implemented, and [it] makes account compromise even easier than before. Moreover, MFA is usually perceived as 'another useless puzzle' by the end users."
Holland also said he doesn't "expect password reuse to significantly decrease anytime soon.
"MFA adds friction to the customer experience, and that friction can cause consumers to go elsewhere," Holland said. "Organizations must be aware of and balance the credential-theft risks with customer acquisition costs and retention."

Ubiquitous software and vulnerability patching
Headlines often focus on the latest zero-day vulnerabilities being exploited by attackers, but the Verizon DBIR 2017 showed a slightly different picture.
According to Verizon, one of the most popular ways to spread malware was through a malicious Microsoft Office document because of the ubiquity of the application. "Only a single-digit percentage of breaches in this DBIR involved exploiting a vulnerability," the report claimed. "That is comforting, but it doesn't mean we are condoning a moratorium on vulnerability scanning or patching vulnerabilities."
Kolochenko said this data could be explained by "the extreme complexity of modern information systems."
"Our crown jewels can be stored in several clouds on different continents, while the access to these clouds can be stored on dozens of computers and mobile devices across the world," Kolochenko said. "Modern targeted attacks involve complicated chained attacks, including social engineering, password reusage and other not-very-technical techniques."
Paul Calatayud, CTO at FireMon, based in Overland Park, Kan., said patching still should be basic cybersecurity for any organization.
"It often fails because the responsibility is shared across two organizations. Security teams identity the vulnerabilities. Server and desktops teams then have to patch," Calatayud told SearchSecurity. "If this program is not taking into account how the firewalls and other compensating controls can reduce the risks of these exploits, IT departments are often faced with a huge backlog of patches with no prioritization."
Verizon's data on patching vulnerabilities was also disconcerting when breaking down the proportion of issues fixed and how long it took for each industry. While information technology, manufacturing and healthcare industries ranked fairly well, the public and financial sectors patched few vulnerabilities -- 30.6% and 25%, respectively.
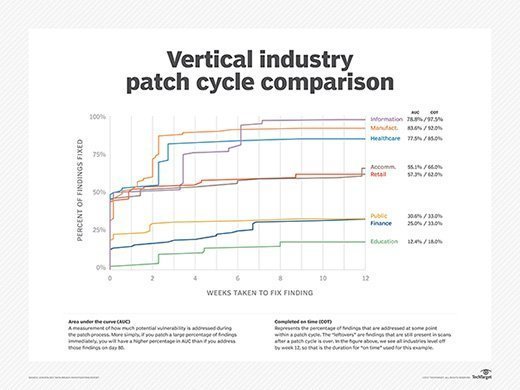
Holland said this failing of basic cybersecurity could be because "the public sector is often under-resourced and understaffed."
"As a result of those challenges, it isn't surprising to see the low patching metrics," he said. "Many financial organizations grow through mergers and acquisitions, and this results in disparate and complex infrastructures. This can significantly complicate the ability to assess and remediate the environment in a timely manner."
Shearer was surprised with the findings on patching but noted that not all vulnerabilities are found in software.
"It is definitely contrary to what the trend has been, especially the renaissance we've been seeing with Exploit kits as a top delivery vehicle for ransomware and data and credential-stealing malware," Shearer said. "I will say that most, if not all, successful breaches are through some form of vulnerability -- i.e., people, process or technology. These findings may bode well for stronger adoption of patching and vulnerability scanning, but cybersecurity pros still -- maybe more than ever -- need to ensure they account for the human vulnerability factor."
Next Steps
Learn how identity management systems can strengthen cybersecurity readiness.
Find out how to synchronize MFA devices for public cloud.
Get info on the best MFA products available.
Related Resources
Dig Deeper on Security operations and management
-
![]()
Verizon DBIR: System intrusion is top healthcare breach cause
By: Jill Hughes
-
![]()
EMEA CISOs must address human factors behind cyber incidents
By: Alex Scroxton
-
![]()
Verizon DBIR: Vulnerability exploitation in breaches up 180%
By: Alexander Culafi
-
![]()
8 data protection challenges and how to prevent them
By: Kathleen Richards




















