
Getty Images/iStockphoto
Dragos: Ransomware attacks against industrial orgs up 87%
Ransomware attacks continue to be a major pain point for industrial organizations, as the sector has historically struggled with vulnerability management.
Ransomware attacks against industrial organizations are up 87% year over year, according to Dragos' "Year in Review" report for 2025.
The report, published Tuesday, is Dragos' eighth annual publication where it presents operational technology (OT) and industrial control system (ICS) security findings from the previous year. Dragos obtained the report's data through a combination of research, incident response engagements, threat hunting and telemetry discovered through the vendor's security platform.
The industrial security space faces a set of particular challenges, as many of the organizations that require OT and ICS systems are in critical infrastructure sectors, such as water and power, or are important parts of the supply chain like manufacturing. Because of the high-stakes status of such organizations -- and because many, particularly smaller, industrial organizations struggle to stay on top of vulnerability management -- OT/ICS has become an increasingly popular target for threat actors. As such, Dragos' latest report focuses in large part on topics like vulnerability management and ransomware.
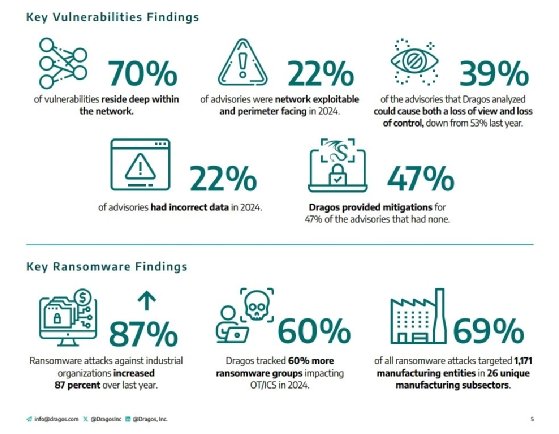
In addition to an 87% increase in attacks last year, Dragos saw a 60% jump in ransomware groups targeting OT and ICS, from 50 groups in 2023 to 80 in 2024.
Dragos observed an increase in threat actors using remote tools and services like VPN appliances to gain initial access to victim networks, "taking advantage of the lack of basic network security defense principles," the report read. For example, the vendor noticed significant differences in outcomes between ransomware victims that enforced strict network segmentation versus those that did not.
"Of the ransomware incidents Dragos responded to in 2024, victim organizations that enforced strict network segmentation between IT and OT systems and conducted offline backup testing significantly shortened the recovery times and avoided paying the ransom," the report read. "Conversely, organizations that did not employ network segmentation and had poorly secured remote access pathways led to more lengthy recovery times, more involved incident response efforts, more severe production downtime, and increased remediation costs."
Vulnerability management challenges
On the vulnerability side, 22% of the 606 OT/ICS-relevant security advisories Dragos analyzed were network exploitable and perimeter facing, meaning they did not require local access for threat actors to exploit. The report noted that 70% of advisories were present deep within an organization's network -- close to control processes, as well as Level 3.5 or below on the Purdue ICS security model. Meanwhile, 39% of advisories could cause both a loss of view and a loss of control, though this is down from 53% in 2023.
Dragos also covered issues surrounding the advisories themselves. For example, 22% had incorrect information, 11% had errors, 7% were more severe than the advisory reported, and 3% were less severe. On the positive side, this is a marked decrease from the 29% of incorrect advisories seen in 2023. Dragos said errors make it difficult for organizations to determine how to prioritize patching or mitigating certain vulnerabilities over others.
Some advisories also alerted organizations to problems without offering mitigations or fixes. Dragos found that 26% of advisories offered no patch, while 18% offered no patch and no mitigation. Just 2% offered both, while 57% provided a patch but no mitigation. Although for many organizations this might not be an issue, critical infrastructure and industrial sectors in particular benefit from mitigations when patches cannot be applied quickly due to technological or logistical hurdles.
Dragos said in the report that it provided alternate mitigation advice to 47% of advisories that were missing both patches and mitigations.
During a press briefing last week, Dragos CEO and co-founder Robert M. Lee explained that traditional IT vulnerabilities are more clearly defined by things like CVSS scores to indicate the severity and exploitability, but OT is more complicated. "In IT, if something's highly exploitable, it's probably worth paying attention to. But in the world of OT, just because it's exploitable doesn't mean you can do anything with it," he said.
Because of this, Lee said, Dragos adopted a system of "now, next, never" to determine how a vulnerability should be handled, rather than a 10-point severity scoring system.
"Should you deal with the vulnerability now? Should you deal with it at the next opportunity, which may mean you're just even monitoring for the exploitation -- not doing anything about it and more just looking for it? Or do you deal with it never, meaning you should not waste any resources and it is not causing any real risk?" he said. "We look at it in an operational context of, is this vulnerability being actively exploited, or would the exploitation of [this] vulnerability actually pose a real operational risk and be easy enough to do? Then that's a 'now' vulnerability."
Concluding the report, Dragos recommended that organizations update or create an incident response plan, conduct attack surface analyses, increase visibility and monitoring capabilities, secure remote access through strict IT/OT network segmentation, and conduct risk-based vulnerability management.
Alexander Culafi is a senior information security news writer and podcast host for Informa TechTarget.







