
Getty Images/iStockphoto
Black Basta ransomware leak sheds light on targets, tactics
VulnCheck found the ransomware gang targeted CVEs in popular enterprise products from Microsoft, Citrix, Cisco, Fortinet, Palo Alto Networks, Confluence Atlassian and more.
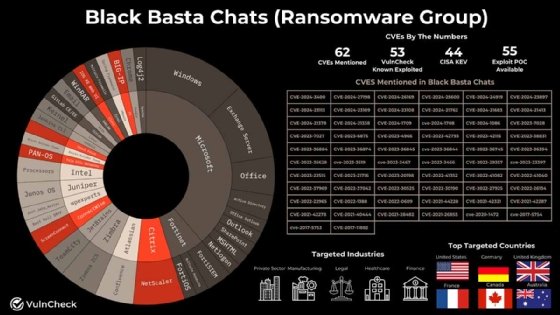
Leaked chat logs from the Black Basta ransomware gang reference 62 CVEs, including more than 50 known exploited vulnerabilities, according to research published Monday by security vendor VulnCheck.
VulnCheck's research follows a leak of chat logs belonging to Black Basta, a Russian-speaking ransomware-as-a-service (RaaS) gang that emerged in 2022 and has targeted critical sectors such as healthcare. VulnCheck, a threat and vulnerability intelligence vendor, analyzed the Black Basta chats and identified 62 unique CVEs that were discussed amongst members of the RaaS operation.
Of the 62 mentioned in the research, 44 are present in CISA's Known Exploited Vulnerabilities catalog, and 53 are in VulnCheck's own KEV.
"Black Basta shows a clear preference for targets with known weaknesses, focusing on vulnerabilities that already have available exploits," VulnCheck security researcher Patrick Garrity wrote in the blog post.
Garrity also said the gang appears to favor "widely adopted enterprise technologies," including those offered by Microsoft, Cisco, Citrix, Fortinet, Palo Alto Networks, Check Point Software Technologies and Atlassian. He noted that mentions of specific CVEs do not necessarily mean Black Basta used them in attacks.
Some notable vulnerabilities discussed in the chat logs include the 2020 Windows escalation of privilege flaw known as "Zerologon," CVE-2020-1472; a Windows Search remote code execution zero-day vulnerability, CVE-2023-36884; two FortiSIEM vulnerabilities with 10 CVSS scores, CVE-2024-23109 and CVE-2024-23108; several Microsoft Exchange vulnerabilities including ProxyNotShell bugs CVE-2022-41040 and CVE-2022-41082; and the Meltdown and Spectre Intel flaws CVE-2017-5754 and CVE-2017-5753 (respectively).
Garrity said Black Basta would discuss new vulnerabilities within a few days of security advisories becoming available. In addition to using known exploits, the gang would discuss purchasing exploits from emerging groups "with hesitancy." Moreover, Garrity said, "there is evidence suggesting that Black Basta has the resources to develop new exploits."
"The analysis of Black Basta's chat logs reveals a methodical yet opportunistic approach that focuses on well-known vulnerabilities and high-value targets," Garrity wrote. "While the group leverages established exploit frameworks and readily available tools, their discussions also suggest potential for new exploit development and tactical shifts. For defenders, the key takeaway is to prioritize the remediation of vulnerabilities using an evidence-based approach."
In an email, Garrity told Informa TechTarget that Black Basta's tactics, techniques and procedures were in line with other ransomware groups. "The research shows that these actors are opportunistic and move fast, targeting initial access, Microsoft technologies and email services," he said.
Alexander Culafi is a senior information security news writer and podcast host for Informa TechTarget.




