Getty Images/iStockphoto
AWS CDK security issue could lead to account takeovers
Aqua Security researchers discovered AWS Cloud Development Kit is susceptible to an attack vector the vendor refers to as 'shadows resources,' which can put accounts at risk.
Aqua Security researchers discovered an issue related to AWS Cloud Development Kit that could allow attackers to take over some customer accounts.
In a blog post Thursday, Aqua researchers detailed risks stemming from AWS CDK, a popular open source framework for configuring cloud resources with widely known programming languages such as Python and JavaScript that developers use to build their applications. However, researchers discovered that using a previously reported attack technique, they could obtain administrator access to AWS accounts by taking advantage of the CDK bootstrap process.
During Black Hat USA 2024 in August, Aqua presented research relating to six critical AWS vulnerabilities as well as a new attack vector called "shadow resources." The vendor's Nautilus research team found that S3 buckets are automatically deployed to support specific AWS services, including CloudFormation and Service Catalog, when users first launch them.
The researchers discovered an attack technique called "bucket monopoly," where threat actors could potentially guess the name of an S3 bucket using a customer's AWS account ID and create an attacker-controlled bucket before AWS automatically creates the legitimate one. The threat actors would then upload files such as a malicious CloudFormation template to the bucket, which users would identify as a trusted resource, and essentially create a backdoor into the targeted organization.
The critical vulnerabilities affect six AWS services: CloudFormation, Service Catalog, Glue, EMR, SageMaker and CodeStar. AWS addressed five of the vulnerabilities -- CodeStar was deprecated earlier this year -- and closed off the shadow resource attack vector.
However, Aqua at the time warned that shadow resources and bucket monopoly attacks also affected open source projects that similarly create automatic S3 buckets. While Aqua researchers did not name specific projects, they warned the consequences could be severe.
"These buckets often use a constant prefix and the user's account ID to create unique bucket names, sometimes also including the region where the service or logic will be deployed," the researchers wrote in an August blog post. "This is very dangerous, as we have seen. An attacker with your organization's account ID or other unique identifiers can create the bucket before the victim does."
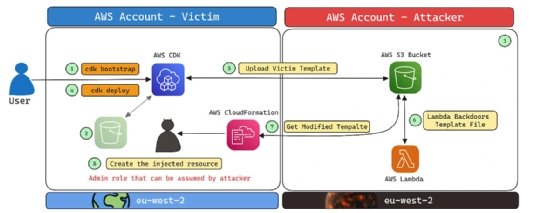
Aqua followed that warning with Thursday's research, which detailed how S3 buckets are automatically created with CDK usage. Specifically, users must bootstrap their AWS environments to prepare for CDK stack deployments; the CDK bootstrap process deploys a CloudFormation template, which in turn automatically creates an S3 bucket with IAM roles and policies.
The Nautilus team found that such buckets follow a naming pattern -- cdk-{qualifier}-assets-{account-ID}-{Region} -- with a predictable qualifier.
"Since many users run the cdk bootstrap command without customizing the qualifier, the S3 bucket naming pattern of the staging bucket becomes predictable. This is because the default value for the bucket name qualifier is set to 'hnb659fds,' making it easier to anticipate the bucket's name," the researchers wrote. "As a result, predicting someone else's CDK staging bucket name only requires knowing their AWS Account-ID and the Region where the CDK was deployed."
The research team said thousands of S3 buckets with the default qualifier are discoverable with a simple GitHub search. More importantly, attackers can execute similar bucket monopoly attacks and obtain admin access to targeted AWS accounts.
"If there is a scenario where the victim's CDK both writes and reads data, such as a CloudFormation template, to and from an attacker-controlled staging S3 bucket, the security implications would be severe," the researchers wrote. "This could allow the attacker to manipulate the data and execute malicious actions within the victim's AWS account."
For example, if a CloudFormation template was mistakenly written to the attacker's CDK S3 bucket, it would be later deployed with admin privileges for the victim's account, which would allow the attacker to create privileged resources.
Additionally, the Nautilus team found that threat actors can even take advantage of deleted CDK S3 buckets by creating a new attacker-controlled bucket with the same name as the previous legitimate instance.
"Since all the necessary roles and resources for CDK were already set up during the previous bootstrap process in the victim's account, CDK will trust the attacker-controlled bucket and proceed to read and write CloudFormation templates to it," the researchers said. "This allows the attacker to manipulate the deployment process and inject malicious resources into the victim's account."
Fortunately, Aqua said only around 1% of CDK users are vulnerable to the threat. "Out of 38,560 accounts analysed, we identified 782 (2%) that had CDK installed. Among those, 81 accounts (10%) were found to be vulnerable to this attack vector," the researchers said. "Additionally, we discovered 100+ vulnerable staging buckets, with some accounts having multiple buckets across different regions, indicating that CDK had been bootstrapped in multiple regions."
Aqua reported the CDK security issue to AWS on June 27, which the cloud giant acknowledged on the same day. AWS released a fix July 12 with CDK version v2.149.0, and the company updated its documentation for customizing bootstrapping resources in August.
However, Aqua warned that the fix only applies to new CDK bootstraps, which means any bootstraps prior to July 12 remain vulnerable to such attacks even if organizations updated their CDKs. The researcher team urged customers to upgrade to the new version and to rerun the CDK bootstrap command. Alternatively, organizations can set an IAM policy to close off the attack vector.
TechTarget Editorial asked Aqua why it described the matter as a "security issue" instead of a vulnerability, considering the previous shadow resources issues with AWS services were categorized as vulnerabilities. Aqua provided the following statement from Yakir Kadkoda, lead security at Aqua's Nautilus team:
"AWS has categorized this security issue as a terminology decision. They believe that the need for users to delete S3 buckets serving CDK poses a security issue, but not a vulnerability (as a security researcher I also don't understand the difference). However, it can indeed be considered a vulnerability, especially given the severity of the patches they released and the notification to users requiring action, etc. To maintain a good relationship with AWS, we acknowledge it as a security issue in our blog as they requested. It would be best to reach out to AWS's security email for further clarification on this matter."
AWS sent the following statement to TechTarget Editorial:
"AWS investigated and resolved all reported concerns. On July 12, 2024, AWS released an update to the AWS Cloud Development Kit (AWS CDK) CLI that implemented additional security controls to mitigate the potential for data disclosure for customers performing CDK deployments. Customers using the latest version will need to perform a one-time action to upgrade their bootstrap resources. AWS has reached out to potentially affected customers directly to notify them of the need to upgrade, and has added additional checks to the CLI to remind users to upgrade. We appreciate Aqua Security for reporting this issue and collaborating with AWS."
Rob Wright is a longtime reporter and senior news director for TechTarget Editorial's security team. He drives breaking infosec news and trends coverage. Have a tip? Email him.