
Getty Images/iStockphoto
Coalition: Ransomware severity up 68% in first half of 2024
The cyber insurance carrier examined claims trends for the first half of 2024, which showed policyholders experienced disruptive and increasingly costly ransomware attacks.
Coalition's cyber insurance claims frequency decreased slightly during the first half of 2024, but ransomware severity jumped 68%.
Cyber insurer Coalition published its "2024 Cyber Claims Report: Mid-year Update" on Thursday that examined policyholder claims submitted between January 1 and June 30, 2024. While Coalition found that overall claims frequency decreased from 1.61% to 1.55% in the first half of this year, claims severity increased 14% as ransomware remained a prevalent threat. The report stated that overall ransomware severity increased by 68% in the first half of 2024 as businesses experienced an average loss of $353,000 per incident.
"After a volatile 2023, in which ransomware severity spiked to nearly $402,000 in the first half of the year before falling to $239,000 in the back half, threat actors reinvigorated the cybercrime with one the highest returns on investment," Coalition wrote in the report.
Coalition found that businesses with $100 million or more in revenue experienced a 140% surge in overall claims severity, which the insurer referred to as "a historic high for this cohort." Policyholders suffered an average loss of $307,000, according to the report.
On the other hand, overall claims frequency was the lowest Coalition tracked since the second half of 2022. Many vendors and cybersecurity organizations reported a decrease in ransomware activity throughout 2022 before activity rebounded and reached record highs in 2023.
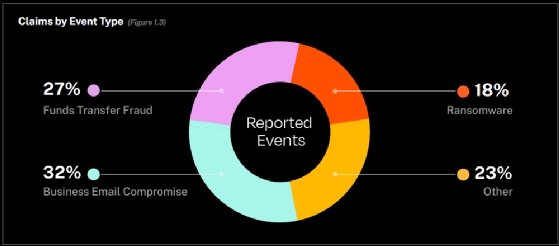
Although ransomware accounted for 18% of event types for claims, behind business email compromise at 32% and funds transfer fraud at 27%, it heavily drove overall claims severity. Coalition noted that ransomware activity showed a consistent pattern, as attackers were more active during winter holidays and less so during summer months.
The report broke down ransomware incidents by sector and found that attack frequency decreased for some industries. "Notably, ransomware frequency among businesses in the financial services industry decreased for all revenue bands. Healthcare businesses with $100M+ in revenue experienced a 32% dip in ransomware frequency over the past six months, but are still up 134% from 1H 2023 rates," the report read.
Ransomware numbers were also driven by massive attacks against United Healthcare's Change Healthcare, a technology vendor that provides billing and reimbursement services for pharmacies and hospitals, and CDK Global, a software vendor that serves more than 150,000 auto dealerships. Coalition said the attacks highlight how significantly downstream customers are affected by supply chain risks. The report found that nearly 75% of auto dealers with more than $100 million in revenue were affected by the attack against CDK Global.
Ransom payments and negotiations
Coalition's report also examined trends in ransom demands and payments. The decision on whether to pay a ransom can be a contentious topic among cybersecurity vendors, government officials and infosec professionals as some have advocated banning such payments. Coalition found that 40% of policyholders paid a ransom demand during the first half of 2024. Coalition said it successfully negotiated initial ransom demand amounts down by an average of 57%.
Coalition found that the average ransom demand increased by just 1% during the first half of the year, though two ransomware gangs stood out. "The ransom demands associated with two ransomware variants, Play and BlackSuit, were noticeably higher with average demands of $4.3 million and $2.5 million, respectively," the report read.
Rob Jones, global head of claims at Coalition, told TechTarget Editorial that the decision to pay is situational, subjective and emotional. "There are many considerations any insured needs as to why and whether to pay. You're trusting a criminal. Can you trust them? You may have to," he said.
Jones added that Coalition asks many questions during the ransom demand decision process, including whether systems are encrypted, how long the business impact may be, and whether potentially leaked data holds sensitive data or trade secrets. Depending on those factors, customers may decide that paying the ransom is the best option.
"You understand why that cost may seem fair and not just because an insurance company is paying it. Proceeds from the policy will do that, but that's part of the policy that covers other things like claims, litigation and regulatory activity," he said.
Jones said Play and BlackSuit were the most active ransomware groups Coalition tracked in the first half of 2024. BlackSuit claimed responsibility for the attack against CDK Global.
For some good news, Jones said LockBit, which was the one of the most prolific ransomware gangs in recent years, was not a major presence in Coalition claims during the first half of 2024. He attributed the drop in LockBit activity to recent law enforcement action, which appears has been successful in quelling the group.
Risky products and practices
Coalition also highlighted risky technologies present in organizations' environments that led to an increase in reported claims. The numbers show ongoing challenges with vulnerability management and organizations' inability to implement basic security protocols like MFA.
The report found that policyholders with certain boundary devices, remote access products and end-of-life-software were 2.5 more times likely to experience a claim during the first half of 2024. That's up from 1.7 times more likely in 2022. Coalition referred to those technologies as "contingencies."
"Exposed login panels were among the most significant contingent vulnerabilities putting businesses at increased risk. Login panels, or login screens, are a way for users to access a website or application," the report read.
The report also warned that policyholders using FortiOS SSL VPNs were 2.8 times more likely to submit a claim, and those using SonicWall firewalls were 1.8 more times to submit a claim. Additionally, policyholders with Cisco Adaptive Security Appliances (ASA) were 5.1 times more likely to experience a claim.
Earlier this year, Coalition issued another report that showed insurance claims skyrocketed for policyholders with ASA devices in 2023, and anticipated the trend would continue into this year. Attackers, including nation-state threat actors, are increasingly targeting and exploiting vulnerabilities in edge devices like Cisco ASA to gain initial access to victim organizations.
"Coalition strongly recommends businesses enforce multi-factor authentication for all VPN users and ensure they're running the latest firmware," the report read.
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.





