
Getty Images
Cryptomining perfctl malware swarms Linux machines
Aqua Security researchers believe that perfctl malware has infected thousands of Linux machines in the last three to four years and that countless more could be next.
A cryptomining malware dubbed perfctl has infected thousands of Linux machines in the last few years. Researchers at cloud security vendor Aqua Security say it has the potential to impact many more.
Aqua Security released new research Thursday detailing perfctl, a Linux malware originating at least as far back as 2021 that has, the report claimed, "actively sought more than 20,000 types of misconfigurations." Researchers at Aqua's Nautilus team "strongly believe" the attackers behind perfctl have targeted millions of systems and that countless more Linux servers could be at risk.
Aqua researchers first discovered the malware in one of their honeypots. Upon further research, the Nautilus team discovered posts on social media platforms and developer communities across the globe referencing perfectl dating back several years. Despite this, and despite the malware's sophisticated attributes, few researchers had published research about it.
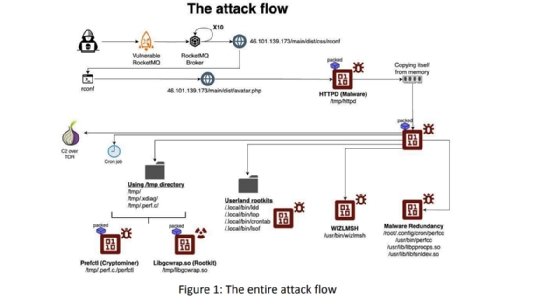
The malware works by exploiting a vulnerability or misconfiguration in a targeted system before downloading a payload from an attacker-controlled HTTP server. The payload then "copies itself from memory to a new location in the '/tmp' directory, runs the new binary from there, terminates the original process, and then deletes the initial binary to cover its tracks."
From the /tmp directory, the payload changes its name. Aqua researchers said that in their experience, the payload's name would be changed to the name of the process that originally executed it.
"In our case the malware was executed by 'sh', thus the name of the malware was changed from httpd to sh," the report read. "At this point, it functions as both a dropper and a local command-and-control (C2) process. The malware contains an exploit to CVE-2021-4043, which it is trying to run in order to gain root privilege on the server. The malware continues to copy itself from memory to half a dozen other locations, with names that appear as conventional system files. It also drops a rootkit and a few popular Linux utilities that were modified to serve as user land rootkits (i.e. ldd, lsof)."
Although the malware would primarily be used to gain access and maintain persistence, it also includes a cryptominer and has seen use in proxyjacking. The perfctl name references the cryptomining and resource hijacking aspects, but said name also has a more practical use case for attackers.
"The name 'perfctl' comes from the cryptominer process that drains the system's resources, causing significant issues for many Linux developers. By combining 'perf' (a Linux performance monitoring tool) with 'ctl' (commonly used to indicate control in command-line tools), the malware authors crafted a name that appears legitimate," the report said. "This makes it easier for users or administrators to overlook during initial investigations, as it blends in with typical system processes."
Infosec professionals generally consider cryptomining malware to be a noisy and easily detectable threat because of performance impacts on infected systems. However, the Nautilus team observed that perfctl "immediately stops all 'noisy' activities" when a new user logs on to a server and only resumes activity when the server is idle again.
The researchers said the malware is also highly evasive.
"All the binaries are packed, stripped, and encrypted, indicating significant efforts to bypass defense mechanisms and hinder reverse engineering attempts. The malware also uses advanced evasion techniques, such as suspending its activity when it detects a new user in the 'btmp' or 'utmp' files, and terminating any competing malware to maintain control over the infected system."
Aqua's research includes further technical details as well as IOCs, detection advice, and mitigation tips such as patching vulnerabilities and disabling unused services on Linux systems. One important mitigation the researchers recommended was for users to set noexec on /tmp, /dev/shm and other writable directories, which prevents perfctl binaries from executing directly from those locations.
Aqua Nautilus chief researcher Assaf Morag told TechTarget Editorial that although his team hasn't identified the threat actor behind perfctl, he suspects the malware is being used by a single threat entity for its own financially motivated intentions rather than being sold on the dark web or being distributed as a service.
However, he said perfctl has elements that would typically be seen in malware from state-sponsored actors. "They're definitely not state sponsored actors," Morag said. "But they're using some advanced techniques which make them look more like state sponsored threat actors and more sophisticated than the average financial threat actor."
Morag said his biggest takeaway from the research is the importance of visibility in protecting one's own environment.
"The way the attacker is operating, and based on what we've seen, you really need to have a kind of visibility. The bottom line for us is that we have great visibility based on the tools that we're using. And I think that if you have this kind of problem, you should really look into these kinds of tools, these kinds of sensors and scanners that will allow to gain visibility for Linux runtime. That's the bottom line," he said. "Because obviously it's not magic. If you can see all the elements of your environment, you can connect all the dots and understand what you're seeing."
Alexander Culafi is a senior information security news writer and podcast host for TechTarget Editorial.







