
metamorworks - stock.adobe.com
NCC Group: Ransomware down in June, July YoY
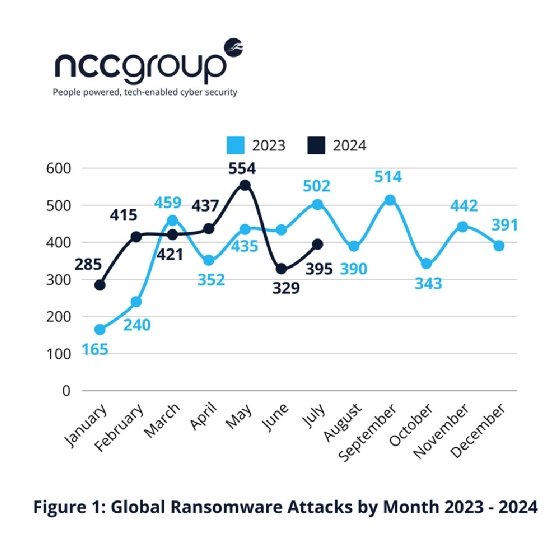
While ransomware activity in July increased from the previous month, NCC Group researchers found the number of attacks was much lower compared to earlier this year.
Ransomware is down in both June and July compared to the same periods in 2023 and compared to most months so far this year, according to a new report from cybersecurity incident response and managed services provider NCC Group.
NCC Group on Thursday published its "Monthly Threat Pulse" report for July, in which the vendor tracked 395 ransomware attacks in July -- a 20% increase from June's 329. The report suggested the increase could have been caused by threat actors looking to target organizations while fewer IT staff are at work during the summer.
However, June and July marked significant declines from February through May, which researchers said suggested a decline in ransomware activity overall. There was also a significant decline compared to June and July last year. "Whether this [July] increase reflects the start of an upward trend remains to be seen, and we will continue to monitor such activity," the report read.
The industrial sector was by far the most targeted by ransomware, with 125 incidents tracked in July up from 105 in June. This more than doubled second place, consumer cyclicals, which experienced 48 incidents. Researchers said the targeting of industrial organizations, such as those using operational technology, "reflects a continued interest by threat actors in targeting critical national infrastructure (CNI)."
July was an interesting month for ransomware, particularly on the threat actor front. NCC Group's research showed RansomHub was the most prevalent ransomware gang in July, with its name on 11% of attacks. Though RansomHub's rise in prominence is notable, LockBit 3.0 took second place with 8% of attacks -- a notable feat given the gang's devastating disruption at the hands of international law enforcement effort Operation Cronos earlier this year.
In July's "Monthly Threat Pulse", researchers said RansomHub's high numbers are partially the result of its ransomware-as-a-service model and partially an observation that "previous LockBit affiliates are suggested to have switched over to the RansomHub RaaS model, as well as other groups, thus further contributing to their dominant presence in the threat landscape."
The report also noted that despite a showing for LockBit near the top of the rankings last month, the activity is nothing compared to the numbers the gang put up in its heyday.
"This [the migration of LockBit affiliates toward other RaaS groups] also provides another explanation for the low attack numbers we continue to observe for LockBit 3.0, with less affiliates operating under their model," NCC Group said. "Whilst LockBit 3.0 still manage to sit in second position, 37 attacks are hardly comparable to the high numbers observed prior to their takedown."
Another notable wrinkle involving ransomware in July was the use of VMware ESXi flaw CVE-2024-37085, a vulnerability Microsoft discovered and reported on last month. The tech giant said multiple ransomware gangs such Black Basta were using the flaw and that it was capable of gaining full administrative privileges on an affected machine. A fix for the vulnerability is available for affected customers.
Matt Hull, global head for strategic threat intelligence at NCC Group, told TechTarget Editorial that the decrease in June and July is "significant" even over last year. A key factor that impacted these figures, Hull said, is likely the reduction in LockBit activity since it was disrupted earlier this year.
"The group's activity had previously made up a large proportion of the overall number of ransomware victims," he said. "Also, an increase in broader law enforcement actions and operations against ransomware groups appears to be creating a difficult environment for ransomware groups to operate."
Asked whether LockBit could make a comeback, Hull said it's too soon to tell.
"The number of victims associated with this ransomware variant [is] still significantly lower than prior to Operation Cronos," Hull said. "This being said, there are clearly affiliates still willing to use this ransomware despite the recent spotlight on the group."
Alexander Culafi is a senior information security news writer and podcast host for TechTarget Editorial.




