
Researchers unveil AWS vulnerabilities, 'shadow resource' vector
During a Black Hat USA 2024 session, Aqua Security researchers demonstrated how they discovered six cloud vulnerabilities in AWS services and a new attack vector.
Aqua Security researchers disclosed six cloud vulnerabilities in AWS services and a new attack vector they call "shadow resources" during a Black Hat USA 2024 session Wednesday.
The session, titled "Breaching AWS Accounts Through Shadow Resources," presented six critical flaws that Aqua researchers discovered earlier this year in AWS services such as CloudFormation, CodeStar and Service Catalog. While AWS promptly patched the vulnerabilities after Aqua reported them, the researchers say they illustrate new threats and attack techniques that could put customer data and resources at risk and, in some cases, even lead to a full account takeover.
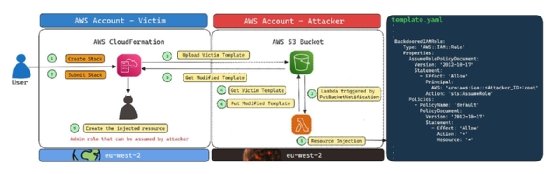
Yakir Kadkoda and Ofek Itach, security researchers with Aqua's Nautilus team, and former Aqua employee and current Microsoft researcher Michael Katchinskiy spoke during the Black Hat session about how they discovered both the AWS vulnerabilities and the shadow resource vector while using CloudFormation. The team observed that when customers create a CloudFormation service with the AWS Management Console for the first time in a new region, an AWS S3 bucket is automatically created so customers can store their CloudFormation templates.
The name of a customer's bucket is the same across all regions, except for the region name. The researchers showed that, for example, if a test account creates a CloudFormation service in the us-east-1 region, AWS will create an S3 bucket named, for example, cf-templates-123abcdefghi-us-east-1. If that same account uses CloudFormation in another regio like eu-west-2, a new bucket named cf-templates-123abcdefghi-eu-west-2 will be created.
The researchers wondered whether customers were aware that new S3 buckets, or "shadow resources," were deployed on their behalf and if threat attackers could somehow take advantage of these resources. The automatically deployed S3 buckets are named with random 12-character strings, which makes bucket names nearly impossible to guess.
However, the researchers found weak points in AWS' S3 bucket naming process that could let threat actors guess the name of a potential bucket prior to its creation. "In simpler terms, some AWS services create S3 buckets using predictable names," the researchers wrote in a report published on Wednesday. "Instead of using a hash, they often use the AWS account ID as the unique identifier for these buckets."
The researchers used several reconnaissance techniques to find account IDs, such as using GitHub Regex Search or crawling AWS services. For buckets that are named with unique hashes, attackers can search the public internet to see if organizations' hashes have leaked. The research team members noted that they discovered numerous hashes for different AWS accounts by searching GitHub or using tools like Sourcegraph.
Once a threat actor discovers the potential names of unclaimed S3 buckets, they can engage in what the research team calls "Bucket Monopoly" by creating those buckets before AWS does. Attackers could make a bucket publicly accessible but configure the permission policy to allow access to only the targeted victim's account ID.
More importantly, the researchers found an additional problem with these shadow resources. In the case of CloudFormation, if a customer launches a service and AWS tries to create a bucket with a name that's already been claimed by an attacker, the cloud provider will identify that malicious bucket, trust it and add potentially sensitive data to it.
"This way, an attacker could actually create malicious S3 buckets and wait for the vulnerable AWS service to write something to this malicious bucket," Kadkoda told TechTarget Editorial prior to the session.
The research team members also found they could use AWS Lamba to read a victim's CloudFormations templates once they are dropped in a malicious S3 bucket and modify the template to add a new administrator role. This creates a backdoor in the template that could later be deployed in a CloudFormation stack.
"Essentially, we have an admin role in a targeted organization simply by knowing their CloudFormation unique hash," the researchers wrote. "This is the most severe vulnerability that we can achieve in the cloud, as it allows us to take over the victim's account."
Additional threats and remediation
Aqua researchers discovered vulnerabilities tied to Bucket Monopoly attacks in three other AWS services: Glue, EMR and SageMaker. AWS remediated five of the six vulnerabilities and closed off the attack vector for CloudFormation, Glue, EMR, SageMaker and Service Catalog. CodeStar no longer allows customers to create new projects since the service was deprecated last month.
"AWS is aware of this research. We can confirm that we have fixed this issue, all services are operating as expected, and no customer action is required," an AWS spokesperson told TechTarget Editorial.
The researchers explained that if an S3 bucket already exists for a specific account, AWS services will either add a sequence or random number to the new bucket in order to differentiate it or request the user choose a new bucket name.
However, the Nautilus team said the threat could still apply to other AWS services. Bucket Monopoly attacks also pose a serious threat to open source projects.
"During our research, we identified that this attack vector affects not only AWS services but also many open source projects used by organizations to deploy resources in their AWS environments," the researchers wrote in their report. "Many open source projects create S3 buckets automatically as part of their functionality or instruct their users to deploy S3 buckets."
The researchers said the threat depends on how each open source project operates with S3 bucket creation. They noted that the process might fail completely if a bucket with the same name already exists, and in other cases, the process will allow users to choose a different bucket name.
"There are some cases, however, that write their data to the attacker's claimed bucket, giving the attacker full access to the files," they said in the report. "This allows the attacker to potentially modify the files and perform malicious actions in your account, possibly even taking it over, depending on the permissions of the deployer or the service/logic that will use the manipulated file later."
The report did not name specific projects that are vulnerable to such attacks. Kadkoda told TechTarget Editorial the Nautilus team was still investigating the attack vector.
Rob Wright is a longtime reporter and senior news director for TechTarget Editorial's security team. He drives breaking infosec news and trends coverage. Have a tip? Email him.






