Getty Images/iStockphoto
Mandiant: 'Exposed credentials' led to Snowflake attacks
According to new threat research, Mandiant is reporting that UNC5537 conducted attacks against Snowflake database customers at least as early as April 14.
This article was updated on 6/11/2024.
Google Cloud's Mandiant reported on Monday that exposed credentials led to attacks against Snowflake database customers.
On May 30, cloud security vendor Mitiga Security said a threat actor tracked as UNC5537 used stolen credentials to target customers of cloud storage and analytics giant Snowflake. The following day, Snowflake published a security advisory confirming this threat activity, adding that it became aware of the activity on May 23 and that the company did not believe UNC5537's attacks were the result of any vulnerability, misconfiguration or malicious activity within Snowflake's products.
In an updated statement published to Snowflake's community forums on June 1 jointly with CrowdStrike and Mandiant, Snowflake claimed no evidence had been identified suggesting activity was "caused by compromised credentials of current or former Snowflake personnel." However, the vendor said a threat actor "obtained personal credentials to and accessed demo accounts belonging to a former Snowflake employee" and noted the demo accounts did not contain sensitive data.
In a June 10 blog post, Mandiant provided additional technical details surrounding UNC5537's campaign. According to its threat intelligence and incident response research, UNC5537 is a financially motivated threat actor that is "systematically compromising Snowflake customer instances using stolen customer credentials, advertising victim data for sale on cybercrime forums, and attempting to extort many of the victims."
UNC5537 utilized a custom attack tool, tracked by Mandiant as Frostbite, and multiple variants of info-stealing malware in its campaign with the goal of exposing customer credentials. These details were previously known or suspected to varying degrees, including knowledge that compromised customers did not have multifactor authentication (MFA) enabled, but the post also offered new information.
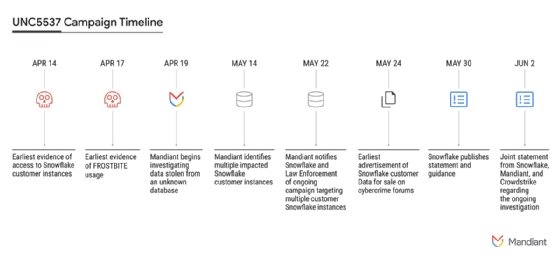
For example, a timeline included in the post dates initial threat activity to April 14. Moreover, it suggested most targeted customers had experienced credential exposure prior to being targeted by UNC5537.
"For the organizations that directly engaged Mandiant for incident response services, Mandiant determined the root cause of their Snowflake instance compromise was exposed credentials," the blog post read. "Further, according to Mandiant and Snowflake's analysis, at least 79.7% of the accounts leveraged by the threat actor in this campaign had prior credential exposure."
Additionally, "these credentials were primarily obtained from multiple infostealer malware campaigns that infected non-Snowflake owned systems," dating as far back as 2020.
Mandiant concluded that UNC5537's campaign reflects both the growing info-stealer market and "missed opportunities" to fully secure vulnerable credentials.
"The affected customer instances did not require multi-factor authentication and in many cases, the credentials had not been rotated for as long as four years," Mandiant said. "Network allow lists were also not used to limit access to trusted locations."
Mandiant and Snowflake have notified approximately 165 potentially exposed organizations to date, according to the company. In a statement shared with TechTarget Editorial, Mandiant Consulting CTO Charles Carmakal said organizations should anticipate further efforts from threat actors to conduct similar attacks.
"The combination of multiple factors contributed to the targeted threat campaign including Snowflake customer accounts configured without MFA, credentials stolen by infostealer malware -- often from personal computers -- and the tenants configured without network allow lists," Carmakal said. "It's critical that organizations assess their exposure to stolen credentials by infostealers, as we anticipate this threat actor and others will replicate this campaign across other SaaS solutions."
TechTarget Editorial asked Snowflake whether it planned to enforce MFA policies or enable it by default in customer environments. In response, a spokesperson shared a link to the initial community forum security advisory, which was updated an additional time on Monday. Snowflake CISO Brad Jones wrote that the company is "also developing a plan to require our customers to implement advanced security controls, like multi-factor authentication (MFA)."
Alexander Culafi is a senior information security news writer and podcast host for TechTarget Editorial.