
Rapid7 warns of alarming zero-day vulnerability trends
The cybersecurity vendor tracked vulnerabilities that were used by threat actors in mass compromise events and found more than half were exploited as zero days.
Attackers exploited more zero-day vulnerabilities than known vulnerabilities during widespread threat campaigns last year, according to new Rapid7 research.
The security vendor published its "2024 Attack Intelligence Report" on Tuesday, which analyzed alarming vulnerability and ransomware trends that contributed to massive compromises enterprises faced between January of 2023 through mid-February this year. Rapid7 based the research on more than 210 vulnerabilities disclosed since the end of 2019, including more than 60 flaws that were exploited over the past year.
Rapid7 researchers discovered that "mass compromise" attack campaigns, such as the ones against Progress Software's MoveIt Transfer product and Ivanti Connect Secure VPN, involved more zero-day vulnerability exploitation versus known, or N-day, vulnerabilities. Such zero-day attacks were frequent throughout last year.
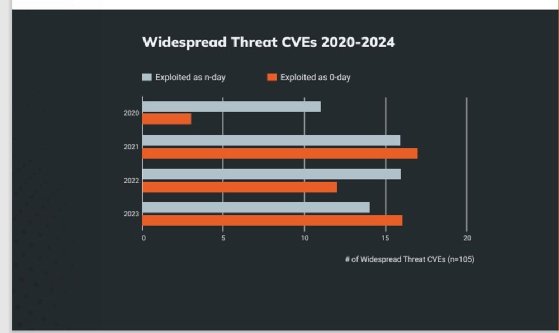
"In 2023, for the second time in three years, more mass compromise events arose from zero-day vulnerabilities than from n-day vulnerabilities. 53% of new widespread threat vulnerabilities through the beginning of 2024 were exploited before software producers could implement fixes -- a return to 2021 levels of widespread zero-day exploitation (52%) after a slight respite (43%) in 2022," the report read.
The report's data set is based on vulnerabilities that contributed to mass compromise events. In addition to CVE-2023-34362, which the Clop ransomware gang exploited against MoveIt Transfer customers, Rapid7 also documented a remote code execution flaw, tracked as CVE-2023-0669, in Fortra's GoAnywhere managed file transfer (MFT) product. Clop also claimed responsibility for some of those attacks, including one against data backup vendor Rubrik.
However, Rapid7 researchers noted some silver linings related to the attacks on the MFT products, crediting Progress Software and Fortra with fast responses. "More broadly, there's been evidence that some file transfer technology vendors are using recent Cl0p attacks as an impetus for maturing vulnerability disclosure and product security practices -- for example, by speeding up remediation SLAs, establishing formal disclosure mechanisms for external security researchers, and implementing more frequent and transparent patch release cycles," the report read.
Other widely exploited vulnerabilities were discovered in several Cisco products as well as Citrix's NetScaler ADC and NetScaler Gateway, particularly CVE-2023-3519, which received a 9.8 CVSS.
The report also detailed the Ivanti Connect Secure and Policy Secure authentication bypass flaw tracked as CVE-2023-46805. A Chinese nation state threat actor subsequently exploited the flaw to compromise CISA, which the agency confirmed in March. In April, Mitre, which manages the CVE system, disclosed a breach by an unnamed nation-state actor that also exploited Ivanti flaws.
Caitlin Condon, director of vulnerability intelligence at Rapid7 and a co-author of the report, said the Ivanti attacks further highlighted how skilled adversaries claim widespread victims in one campaign with zero-days and custom payloads.
"I have a lot of empathy for [Ivanti]. There's so much legacy technology out there; this isn't an isolated issue. Customers want security, of course, but they also don't want disruptions to business operations or functionalities. I think that puts software producers in a tough spot," Condon said.
While legacy issues remain ongoing, Rapid7 researchers cited new exploitation trends they observed during mass compromise events. For example, researchers relied less on the use of honeypots because all the flaws they categorized in 2023 were actively exploited in real-world production environments.
Additionally, they stressed how last year's threat landscape proved one flaw could lead to a massive attack scope.
"Instead of following the familiar pattern of 'many attackers, many targets,' nearly a quarter (23%) of widespread threat CVEs arose from well-planned, highly orchestrated zero-day attacks in which a single adversary compromised dozens or hundreds of organizations in one fell swoop, often leveraging a custom tooling like proprietary exploits and backdoors," the report read. "These aren't our grandparents' cyber threats -- this is a mature, well-organized cybercrime ecosystem at work, with increasingly sophisticated mechanisms to gain access, establish persistence and evade detection."
However, the report stressed that many of the vulnerabilities used in widespread attacks were easily exploitable and leveraged "command injection or improper authentication issues" rather than memory corruption.
Condon emphasized how Rapid7 observed more advanced actors hit much simpler root causes with software vulnerabilities. She told TechTarget Editorial that most of the widely exploited vulnerabilities she's seen have simple root causes.
While threat actors are leveraging what Rapid7 categorizes as basic vulnerability classes, enterprises still struggle to combat attacks. She urged enterprises to conduct penetration tests and examine their software for basic flaws.
"We've seen government guidance over the last nine months or so on things like memory safe roadmaps or eliminating SQL injection [vulnerabilities]. I think that type of guidance is good, and we're not saying don't do it. But I think we're seeing a bit of a disparity between the things being focused on and targeted by government agencies than the type of root causes that attackers are using so frequently," Condon said.
Nation-state actors and APTs
During attacks, threat actors increasingly used zero days and known vulnerabilities in network edge devices such as VPNs to gain initial access to a victim organization. in many cases, those devices lacked MFA, a standard the industry has pushed for years.
The report emphasized that 36% of widely exploited vulnerabilities occurred in network perimeter technologies. "Network edge CVEs are also disproportionately represented across zero-day attacks in our data -- for the past three years, more than 60% of the vulnerabilities Rapid7 analyzed in network and security appliances were exploited as zero-days," the report said.
Cyber insurer Coalition's "Cyber Claims Report 2024" published last month highlighted that ongoing threat. The report showed that claims related to Cisco and Fortinet network boundary devices skyrocketed last year.
Rapid7 observed that nation-state advanced persistent threat (APT) groups were highly active in the exploitation of vulnerabilities between January 20203 and February of this year. The cybersecurity vendor identified 188 individual campaigns that researchers attributed to APTs with moderate to high confidence.
"Based on our analysis, we concluded that across the top 15 groups, 30% of attacks attributed to APT groups originated from Chinese-backed campaigns. Campaigns from Russian-affiliated groups came in a close second, comprising 26% of campaigns conducted by state-sponsored adversaries, while North Korea (14%) and Iran (9%) ranked third and fourth," the report read.
In addition to nation-state threat groups, ransomware gangs were also highly active. Rapid7 tracked 5,600 reported ransomware cases between January 2023 and February of this year but noted the number is likely much higher due to a lack of reporting.
While ransomware actors seemingly decreased malware deployment and increased data theft and extortion activity, Rapid7 also observed "traditional" ransomware remained prevalent. "The vast majority of ransomware-related incidents Rapid7 MDR responded to in the last year have included encryption, with only a small number of incidents ending in extortion alone," the report read.
Throughout last year, the report warned that ransomware actors continued to exploit public-facing applications and use valid account credentials to gain initial access to victim organizations. Like past years, 41% of incidents Rapid7's Managed Detection and Response (MDR) observed in 2023 occurred due to absent or unenforced MFA protection.
Silent patching
Vendors silently patching vulnerabilities was another issue that proved challenging for enterprises, according to the report. For example, in March, Rapid7 called out JetBrains for silently patching a TeamCity vulnerability that quickly came under attack following a disclosure dispute between the two companies.
"In our experience, it's been increasingly common for vendors to silently patch issues, withholding advisories and CVE descriptions until days or weeks later. Even then, more vendors appear to be deliberately obfuscating vulnerability details, declining to publish root cause and attack vector information based on an understandable but misguided belief that obscurity deters adversaries and mitigates reputational risk to software producers," the report said.
Rapid7 added that it's observed an uptick in the privatization of vulnerability and exploit information as well. While vendors and manufacturers typically publish public security advisories on vulnerabilities discovered in their products, some companies have shifted to releasing such information privately through email notifications or gated customer portals "for profit or otherwise."
Condon agreed the silent patching issue has grown worse over the past year, negatively impacting end-user organizations because it eliminates informed consent. She stressed that many organizations are trying to prioritize vulnerability patches, but it makes that process more difficult when crucial data and context aren't provided. But there are some who feel that publicly releasing patches and technical details for critical vulnerabilities gives the attackers the advantage.
"I think there's a problem with a whole lot of fear, which is completely understandable. To be clear, we don't recommend or condone silent patching because we think that hurts the people who need to know the patch exists beyond attackers," Condon said. "I think we're in a tough spot as a community. It's going to get messier before it gets better."
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.





