
Getty Images/iStockphoto
SentinelOne: Ransomware actors are adapting to EDR
At RSA Conference 2024, SentinelOne's Alex Stamos discussed ongoing global threats such as ransomware and how threat actors are changing their techniques.
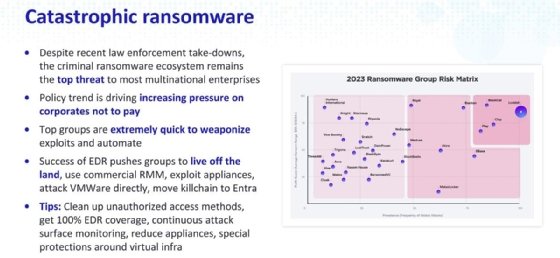
SAN FRANCISCO -- During an RSA 2024 session on Tuesday, SentinelOne's Alex Stamos warned that ransomware actors are leveraging more commercial software tools instead of malware due to the success of endpoint detection and response products.
Stamos, chief trust officer at SentinelOne, presented a session titled "Global Threat Overview" where he discussed geopolitical conflicts, the cyber arms race, policy regulations, generative AI and the ongoing evolution of ransomware. In addition to more brazen extortion tactics and a decrease in ransomware deployment, SentinelOne also observed threat actors are increasingly using living off the land (LOTL) techniques to avoid detection.
Though it highlights endpoint detection and response (EDR) tools increasing effectiveness, Stamos stressed that ransomware actors are adapting quickly. He added that he prefers using the term cyber extortion over ransomware because attackers have gotten more complex in extortion tactics.
"If you've got computers, if you've got money, then you're going to get ransomwared," Stamos said during the session. "From a tech perspective, these actors have changed their model. I think a lot of this is because of the success of EDR."
SentinelOne observed ransomware actors are now using less custom malware as well as leveraging more commercial software and remote employee management tools during attacks to avoid detection tools and remain hidden inside networks. The use of LOTL tactics is a growing trend across the threat landscape. U.S. agencies and Microsoft highlighted the LOTL risk to critical infrastructure organizations in another RSA Conference 2024 session Monday around the Chinese nation-state threat actor Microsoft tracks as Volt Typhoon.
During Tuesday's session, Stamos highlighted the extent of the problem in ransomware attacks. While conducting an incident response case, Stamos observed attackers planted 12 different backdoors inside the victim organization. Eleven of those backdoors were commercial tools that attackers either bought or were using 30-day free trial offers.
Stamos stressed that attackers adapted their tactics because it is more difficult for enterprises to detect commercial tools versus custom malware that is more likely to trigger suspicious activity alerts in EDR products.
The ongoing cyber arms race also contributed to the ransomware evolution, Stamos said, as zero-day exploits and "cyberweapons" have become more common.
"Cyber arms race at the top level makes the entire world more dangerous because these weapons are effectively falling out of the sky and everyone once in a while a ransomware or any actor picks one up whodidn't have money to invent it themselves," he said.
Another problem he addressed was the expanding attack surface. Stamos stressed that most companies have complicated attack surfaces that are difficult to understand and navigate. He said threat actors are going after any vulnerable system they find, then deciding if it's a victim worth attacking.
Despite expanding attack surfaces, Stamos said Microsoft is the popular vector and cited Microsoft Exchange as 2023's top target. "Here's a tip: Never use a Microsoft product that Microsoft themselves doesn't even use anymore. That's a bad sign. Microsoft Exchange would very firmly fit in that category of a product you shouldn't employ yourself," he said.
He added that attackers are becoming increasingly effective at targeting the kill chain just to get to Microsoft. In some cases, enterprises are extremely vulnerable because many mitigations are out of their control.
"We found out just last week, there was a Microsoft graph API endpoint that didn't have any rate limiting on it, so people have been password spraying without any kind of alert coming to you. There's no way you could have stopped that."
Brian Reed, cybersecurity evangelist at Proofpoint, told TechTarget Editorial that attackers constantly target Microsoft because their products are so widely deployed across the landscape. However, he said it's counterproductive to name and shame Microsoft because it could lead the company to be even less transparent about security incidents and vulnerabilities.
GenAI tools are working
Stamos said generative AI can help enterprises defend against these evolving threats. For example, AI tools can help with the workforce shortage and enterprise's ability to operate around the clock as well as globally. He stressed that for the most part, generative AI has been more significant for defenders versus attackers.
"Big benefit there. It can make SOC [security operations center] analysts, individual workers more efficient. However, bad guys are going to get there," he said.
He warned that every enterprise is a target for attackers, but those with operations in China should be particularly concerned. Stamos added that China has become better than any nation at blending human security and cybersecurity to conduct successful attacks.
Regarding mitigation recommendations, Stamos advised enterprises to get all their data into one place and monitor suspicious activity across correlating logs.
"From an enterprise security perspective, for any reasonably sized organization, you have to assume breach."
Arielle Waldman is a Boston-based reporter covering enterprise security news.







