
Splunk details Sqrrl 'screw-ups' that hampered threat hunting
At RSA Conference 2024, Splunk's David Bianco emphasizes that enterprises need revamped threat hunting frameworks to help with threat detection and response challenges.
SAN FRANCISCO -- Splunk's David Bianco highlighted problems with threat hunting frameworks like Sqrrl that can hinder security teams' success -- and apologized for creating some of those problems years ago.
Bianco, a staff security specialist at Splunk, spoke on Monday at an RSA Conference 2024 session titled "I Screwed Up Threat Hunting a Decade Ago and Now We're Fixing It With PEAK." Bianco discussed his involvement in developing threat hunting frameworks including detection and response platform Sqrrl from 2015 to 2017 and, more recently, Splunk's PEAK framework, which launched last spring.
Bianco said the Sqrrl framework "disappeared" for a short time after Amazon Web Services acquired the startup in 2018. The framework focuses only on hypothesis-based threat hunting, he said, though there are additional models. Bianco shared how his experience working on the platform contributed to the development of PEAK, which he believes is a more well-rounded framework.
Prior to the RSA Conference session, Bianco spoke with TechTarget Editorial and stressed that PEAK and other threat hunting frameworks need to incorporate research and development as well as improving detection to increase efficiency and effectiveness.
"This might be an actual screw-up, especially in the Sqrrl framework, but it's really in all of them that I found. We talk a lot about what you should do, but we don't tell you a lot about how to do it," Bianco said.
Bianco considers Sqrrl, PEAK and the TaHiTI methodology as the three major threat hunting frameworks currently. TaHiTI, which stands for "Targeted Hunting integrating Threat Intelligence," was developed in a joint effort by several Dutch financial institutions known as the Dutch Payments Association and launched in 2018. Bianco said he had a level of involvement in the development of all three frameworks. However, he considers Sqrrl more of a collection of articles and e-books, rather than a framework.
Bianco's presentation highlighted three hunting types: hypothesis-based, model-assisted and baseline threat hunting. While he said Sqrrl was helpful, he does not believe that hypothesis-based hunts are sufficient on their own. He emphasized that Sqrrl is heavy on data analysis, but light on hunting outcomes. The primary problem is that it ignores preparation and planning, he said, confessing to another "screw-up" in thinking that threat hunting was a single-phase operation.
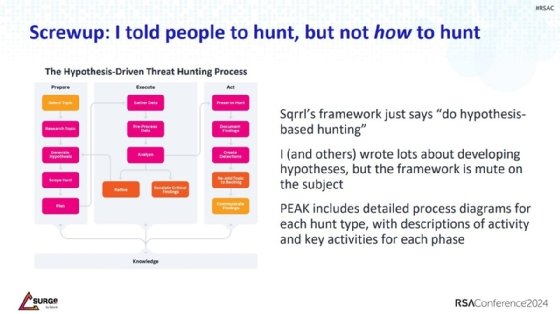
With that in mind, he helped developed PEAK, which stands for "Prepare, Execute and Act with Knowledge," as a three-phase hunting structure. The newer threat hunting framework contains detailed processes for different types of hunts, plus the key steps and activities for each phase.
Another problem Bianco observed while running the threat hunting team at Target is that they compressed all their hunts down into a particular week. He stressed that effective hunts require a more continuous process.
Threat hunting frameworks also go hand in hand with detection, which was another area Bianco wanted to reshape. "I realized I did not have anything about what happens after the hunt, except for you should make an automated detection. Just do that, it's super easy, no explanation needed. I was wrong," he said.
While Bianco stressed that detection of malicious activity is important, he believes it's essential to go beyond that to improve security postures across the board. Enterprises continue to face greater risks due to ransomware and a growing number of vulnerabilities, but they also struggle to follow mitigations for repeated security mistakes such as leaving Remote Desktop Protocol exposed and insufficiently patching.
"We realized that with threat hunting, when you're poking around and things where other people are not looking around, you're finding all kinds of stuff. These can be different misconfigurations or vulnerabilities, patches that have not been applied -- or even if there's no threat, these things are opportunities to improve your security posture," he said.
In addition, Bianco said it's important to provide security teams with tangible metrics of effectiveness to communicate to leadership and stakeholders. He said metrics reinforce the fact that threat hunting is not just about finding incidents or enhancing detection, but about creating continuous improvement across an enterprise's security posture.
During the session, Bianco detailed a set of five core metrics for PEAK, including detections created or updated, incidents opened, gaps identified, vulnerabilities and misconfigurations, and techniques hunted.
Bianco said PEAK has received positive feedback since launching last year as his team speaks with customers, government agencies and commercial entities.
"It helps even novice threat hunters because it tells them where they are in the process, what the next step is and what the next step actually means," he said. "It's really easy to start with the threat hunting types and metrics, and they can have the biggest impact."
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.








