
Alex - stock.adobe.com
Coalition: Insurance claims for Cisco ASA users spiked in 2023
Coalition urged enterprises to be cautious when using Cisco and Fortinet network boundary devices as attackers can leverage the attack vectors to gain initial access.
Enterprises using specific network boundary devices, including Cisco and Fortinet products, faced greater security risks last year, and the trend is likely to continue in 2024, according to a new report by Coalition.
The insurer published on Wednesday its '2024 Cyber Claims Report' that analyzed claims submitted by policyholders from across the U.S. While ransomware, business email compromise and funds transfer fraud attacks remained prevalent threats, vulnerable boundary devices were also a main driver for the 13% increase in overall claims year-over-year between 2022 and 2023. Additionally, claim severity increased by 10%, resulting in an average loss of $100,000 for Coalition policyholders.
Boundary devices, such as firewalls, VPNs and routers, are common components of security postures. But Coalition found certain products posed increased risk to enterprises compared to others. Coalition warned that attackers frequently target boundary or edge devices because they are "critical to business operations" and secure remote access.
Therefore, the insurer urged enterprises to increase awareness around any vulnerabilities reported in boundary devices deployed for network security and to ensure the devices are not exposed to the public internet.
"Firewalls, virtual private networks, and other devices can help reduce cyber risk. However, boundary devices with known vulnerabilities increased the likelihood of a business experiencing a cyber claim," Coalition wrote in the report.
The report highlighted devices manufactured by two companies in particular: Cisco and Fortinet. First, Coalition discovered a connection between claims frequency and enterprises that used Cisco Adaptive Security Appliance (ASA) devices, which are intended to secure remote access. Cisco ASA devices offer a combination of firewall, antivirus, intrusion prevention and VPN capabilities, according to the report.
Coalition found that ASA devices posed an increased risk to enterprise security due to repeated vulnerabilities in the products as well as enterprises not adhering to best practices. For example, last month, CISA disclosed that the Akira ransomware gang has extorted $42 million from more than 250 victims since it was first observed a year ago, with many attacks involving the exploitation of two separate Cisco vulnerabilities.
Both flaws affected Cisco's ASA and Firepower Threat Defense software. But one was first disclosed and patched in 2020, which further highlighted enterprises' struggle to patch in a timely manner. CISA said Akira operators exploited the flaws to compromise devices without MFA protection and gain initial access to victim organizations.
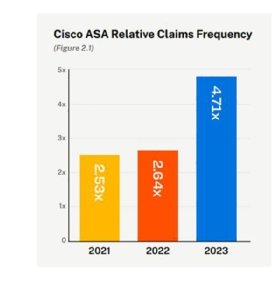
"Due to the risk associated with these devices, Coalition routinely scans policyholders for exposed Cisco ASA web panels," the report read. "Businesses with internet-exposed Cisco ASA devices were nearly five times more likely to experience a claim in 2023."
For comparison, claims frequency related to Cisco ASA devices stayed steady at around 2.5 times higher than other boundary devices in 2021 and 2022.
Secondly, enterprises with internet-exposed Fortinet devices were twice as likely to submit a claim -- a statistic that's remained consistent from 2021 through 2023. Coalition stressed that attackers target Fortinet devices for the "level of privileged access that can be gained by compromising them."
In June, Fortinet warned that attackers, including Volt Typhoon, might have been exploiting a critical Fortinet SSL VPN flaw tracked as CVE-2024-27997. While Coalition's report only addresses 2023 threats, CISA has already added two Fortinet vulnerabilities to its Known Exploited Vulnerabilities Catalog this year.
Shelley Ma, incident response lead at Coalition, said Cisco and Fortinet boundary devices aren't the only products that attract threat actors, noting that SonicWall firewalls and Microsoft Exchange Server are also frequently targeted. "A policyholder is using that; it just requires so much stringency around the security protocols," she told TechTarget Editorial.
RDP "a looming presence"
Another threat related to boundary devices is internet-exposed Remote Desktop Protocol (RDP), which is a remote communication feature built into Microsoft Windows. "After a decrease in 2022, the risk associated with RDP surged in 2023. Policyholders using internet-exposed RDP were 2.5 times more likely to experience a claim in 2023," the report read.
Coalition was not the only vendor to observe that trend. Sophos published its "Active Adversary Report of 1H 2024" earlier this month that found 90% of attacks the security vendor responded to in 2023 involved RDP abuse -- a consistent trend over the past few years.
Ma expanded on the pervasive RDP threat, which she observed firsthand.
"We [Coalition] had an almost 60% surge in unique IP addresses scanning for open RDP over the past year, which suggests a growing trend of attackers targeting these entry points," Ma said. "I've been in the industry since 2014 and RDPs just literally never go away. 90-95% of ransomware back in the day used to be because of RDP, and to this day, RDP is still this looming presence, which honestly surprises me. Even though the industry at large has gotten better, RDP is still a thing."
She attributed RDP risks in part to enterprises sometimes forgetting about an entry point because it's running in a legacy server. Additionally, she said RDPs can get scanned and picked up when security teams temporarily expose instances to make it easier to migrate from one platform to another. Other times, a company might be acquiring or merging with another organization and are unaware there are open RDP instances in the infrastructure.
When alerting policyholders, Coalition deems RDP risks as critical, so notifications tend to be more aggressive. However, getting responses can depend on the personality of the IT personnel, she said.
In addition to RDP, ransomware also remained a consistent threat last year. Coalition found that ransomware frequency increased by 15% year-over-year, driven by a surge in activity during the first half of 2023.
As for the second half of 2023, Coalition observed that ransomware frequency, severity and demands decreased. The report attributed successful law enforcement efforts to the fluctuations in ransomware activity levels throughout the year. For example, in December, the Department of Justice announced the FBI disrupted the BlackCat/Alphv ransomware gang.
Coalition opposes ransom payment bans
The report also focused on ransomware payments, which have been a contentious topic lately as ransomware activity and the number of victims reached historic records in 2023. Coalition found that the average ransom demand increased 36% to an average of nearly $1.4 million in 2023.
Some infosec professionals argue that giving into extortion demands fuels ransomware groups' operations and should be banned. Others say paying should be a business decision since attacks pose operational, economic and reputational damages to victims.
"While paying every ransom is not the answer, a blanket ban is impractical. Proponents of a ransomware payment ban often say cyber insurers are part of the problem, suggesting they pay ransoms as an easy way out or view insurance as a substitute for security investments," the report said. "Insurers often incur higher incident costs than the initial ransom demand, spending more on crisis response and recovery expenses."
The report revealed 40% of Coalition policyholders that suffered a ransomware attack last year did pay. But Coalition was also successful in negotiations with threat actors in terms of reducing the initial amount. The insurer negotiated demands down by an average of 64% in 2023.
Ma said negotiation strategies involve a lot of psychology, game theory and different mathematical principles. It's become even more difficult now as attackers have apparently embraced AI. During communications with threat actors, for example, Ma noticed significantly improved vocabulary.
"Putting email communications side by side from a certain actor in 2016 versus today, you can't even recognize it as kind of the same thing," she said.
Ma also observed how attackers use AI to synthesize large quantities of data much quicker. When exfiltrating hundreds of gigabytes of data, it can be impossible for threat actors to go through and determine exactly what's encapsulated. However, Ma said the turnaround is much more efficient with AI tools, fueling data extortion threats.
"They can say, 'We know you have business relationship with companies X, Y and Z. We know how much you make based on the general ledger.' They can just go through the data with so much ease, and they can translate it into their native language. It's a powerful tool," she said.
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.





