
Getty Images
Sophos: Ransomware present in 70% of IR investigations
Sophos' Active Adversary Report said securing remote desktop protocols and Active Directories and hardening credentials can help limit the influx of successful ransomware attacks.
Sophos said the majority of cyberattacks it investigated in 2023 involved ransomware, while 90% of all incidents included abuse of remote desktop protocol.
The security vendor published its Active Adversary Report of 2024 Wednesday that drew on data from more than 150 incident response (IR) investigations it conducted in 2023. Breaking down the data set, 88% of the investigations were derived from organizations with fewer than 1,000 employees, while 55% involved companies with 250 employees or fewer. Twenty-six sectors were represented, and manufacturing remained the No. 1 sector to engage the Sophos IR team for the fourth consecutive year.
For the report, Sophos tracked attack types, initial access vectors and root causes, and found that trends have remained consistent for the past two years. While attackers frequently abuse remote desktop protocol (RDPs) and credential access to infiltrate a victim's network, enterprises continue to leave RDPs exposed and often lack multifactor authentication (MFA) protocols.
Sophos added that enterprises also fell short regarding sufficient log visibility, which can hinder IR investigations.
"Often, the sole differences between organizations that are breached and ones that aren't are 1) the preparation entailed by selecting and putting the proper tools in place and 2) the knowledge and readiness to act when required," Sophos wrote in the report. "Most of the tools and techniques described in this report have solutions, or at the very least, mitigations to limit their harm, but defenses are simply not keeping up."
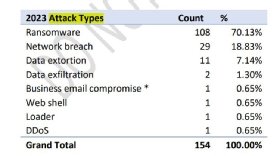
Like many other vendors, Sophos found ransomware to be the most prevalent attack type in 2023; the threat accounted for 70% of its investigations. The vendor responded to 108 ransomware attacks. Network breach placed second but accounted for only 19% of investigations. However, Sophos deduced a possible link between the two attack types. "While we can't be certain in all cases, there is mounting evidence that many network breaches are indeed unsuccessful ransomware attacks," the report said.
Sophos confirmed known ransomware gangs conducted five of the network breaches it investigated. The vendor also compared network breaches with ransomware attacks by quarter and found that breaches increased when ransomware activity decreased. While 44% of ransomware attack cases involved data exfiltration, Sophos found that 72% of network breach investigations had "no evidence of data exfiltration."
Sophos also tracked the ransomware deployment timelines and found a consistent pattern. Last year, 91% of ransomware payloads were deployed outside of traditional business hours, down just 3% from 2022. Sophos categorized "traditional business hours" as Monday through Friday from 8 a.m. to 6 p.m., but the report noted that data also accounted for countries that don't follow that schedule.
Another consistent trend was ransomware family distribution. Sophos found the LockBit ransomware group continued to be the most prolific gang last year. The report attributed 24 ransomware attacks, or 22% of IR investigations to LockBit. It's difficult to say if LockBit will continue to dominate the landscape throughout 2024. The infamous group was temporarily disrupted by an international law enforcement effort in February. While LockBit operators quickly restored their servers, the gang's attempted comeback has struggled.
John Shier, field CTO of threat intelligence at Sophos, told TechTarget Editorial that the law enforcement action dubbed, "Operation Cronos" was successful in disincentivizing affiliates to join LockBit. Shier said brokers and affiliates have expressed that sentiment on underground forums following the disruption. "LockBit thrived partly due to its scale. Without criminal partners to work with and an erosion of trust we'll hopefully see LockBit continue its downward slide into irrelevance."
LockBit was one of many ransomware groups, including Cuba and Snatch, that have been part of investigations since Sophos published the first Active Adversary report in 2021.
The ransomware gang Akira, which emerged in March 2023, took second place last year, with 12 attacks. Sophos was surprised that Akira outpaced the Alphv/BlackCat ransomware gang, which took third place.
Operators are known to target healthcare organizations, and claimed responsibility for a notable attack against MGM Resorts last year. In December, the U.S. Department of Justice announced that the FBI temporarily disrupted Alphv/BlackCat and developed a decryption tool to help victim organizations, but the group remains active. Alphv/BlackCat actors were behind the massive attack against UnitedHealthcare's Change Healthcare in February.
"Ransomware attacks have reached a stasis point with respect to prevalence, tooling and timelines. Unfortunately, we are also still seeing the same mistakes being made by defenders every year. It's with this in mind that we think organizations need to urgently participate in their own rescue," the report said.
Repeated mistakes
Sophos listed many mistakes defenders continue to make, such as leaving VPNs and RDPs exposed. Attackers take advantage of those errors to gain initial access to a victim's environment, Sophos warned. For example, in August Cisco detailed an attack campaign in which Akira and LockBit actors targeted organizations that used its VPNs but did not have MFA enabled.
The report emphasized that external remote services remained the leading initial access method for every Active Adversary report Sophos has published.
Sophos urged enterprises to secure RDPs in its midyear Active Adversary report published in August. The vendor warned the protocol was involved in 95% of attacks during the first half of 2023. However, the threat vector continued to pose problems for organizations throughout the year. The report emphasized RDP remained the "most abused of all the Microsoft LOLBins (living-off-the-land binaries)," last year.
"RDP abuse has reached new heights, with 90% of attacks using it for internal lateral movement and 20% for external remote access. As for the 18% of organizations who still have RDP exposed to the internet, you should ask yourself, 'My God, what have I done?'" the report said.
Shier expanded on why enterprises continue to struggle to secure RDP. Based on the IR data, he said organizations fall into two categories. "One is that organizations don't know the harms that can come from exposing RDP to the internet and chronically under-protecting it, and the other is that they simply don't care," he said.
Enterprises also continued to struggle with securing credentials. Sophos attributed compromised credentials as the No. 1 root cause of attacks, with the percentage of incidents nearly doubling from 2022. "What makes this worse is the woeful state of credential hardening. In 43% of investigations, multifactor authentication (MFA) was not configured," the report said.
Sophos added that MFA technology is now three decades old.
The report urged enterprises to also secure their Active Directories (AD), which attackers increasingly target. Sophos started tracking the time-to-Active Directory metric in 2023 and found the median time-to-AD for all attacks was 0.64 days.
Regarding AD threats, the report recommended that enterprises run tools to detect suspicious activity and, more importantly, continually monitor and respond to the suspicious signals. During IR investigations, Sophos also found that log visibility was an issue. Telemetry was missing in 54% of attacks the vendor investigated.
"While there were several reasons why the logs were unavailable, in most cases it was because organizations hadn't taken the necessary steps to ensure they would be there when it mattered most," the report said.
"What matters most in the incident-response context is how the attackers breached the organization and why they succeeded," Sophos added.
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.






