Getty Images/iStockphoto
Flashpoint observes 84% surge in ransomware attacks in 2023
The threat intelligence vendor anticipates that enterprises will continue to face increases in ransomware activity and data breaches in 2024, with some silver linings ahead.
The number of publicly disclosed ransomware attacks increased by 84% from 2022 to 2023, and activity doesn't appear to be slowing down in 2024, according to a new report by Flashpoint.
In its "2024 Global Threat Intelligence Report" Wednesday, the threat intelligence vendor detailed significant surges in ransomware, vulnerability disclosures and data breaches. The findings were based on Flashpoint's cybersecurity analytics platform, which draws on information from ransomware leak sites, attorney general reports and Freedom of Information Act requests.
Flashpoint warned that ransomware remains a persistent threat as attackers continue to leverage zero-day and known vulnerabilities against victim organizations. In 2023, it was one of the top two causes for an alarming amount of data breaches.
"Flashpoint identified a significant increase in ransomware attacks across all sectors in 2023, resulting in an increase of 84% YoY [year over year]. In the first two months of 2024 alone, the number of public ransomware attacks has grown nearly 23% compared to the same period in 2023," Flashpoint wrote in the report.
Flashpoint threat intelligence revealed that the number of ransomware attacks rose from 2,720 in 2022 to 5,028 last year. The numbers continue to spike in 2024, a trend also reported by NCC Group last month. There were 637 publicly disclosed ransomware attacks in January and February, compared with 518 recorded for the same period in 2023, according to Flashpoint.
Construction and engineering remained the most targeted sector for ransomware attacks throughout 2023 and into 2024 with 416 incidents. Professional services, internet software and services, and healthcare providers and services were the second-, third- and fourth-most targeted sectors, respectively.
Flashpoint said these sectors share commonalities that make them attractive targets for ransomware actors, including sensitive data and urgency to resume operations. In addition, the report emphasized that critical infrastructure organizations often generate higher revenues, giving ransomware actors a potentially "higher profit per victim" compared with other industries.
The use of operational technology, which can contain outdated or unpatched software, is another lure to threat actors, Flashpoint said. Attackers can leverage OT vulnerabilities to gain access to victim organizations' systems.
Vulnerability management continues to be another challenge for enterprises. The report emphasized that 2023 marked a "significant peak" with 33,137 disclosed vulnerabilities; that included 35% with known public exploits. In addition, more than half of the vulnerabilities received a high to critical CVSS ranking, which makes prioritization even more difficult.
"One major blind spot occurs when enterprises strictly rely on the Common Vulnerabilities and Exposure (CVE) database, which is missing over 100,000 vulnerabilities -- nearly a third of known vulnerability risk," the report said.
The report referenced 330 vulnerabilities cataloged by Flashpoint analysts that were found to have been exploited in the wild, but had not been assigned a CVE ID as of February. Those flaws affected Adobe Reader, Apple iOS and macOS, Google Android, Microsoft SQL Server and Siemens SIMATIC. The list also included SolarWinds' Orion platform, which nation-state threat actors compromised during the massive supply chain attack that was discovered in 2020.
Flashpoint recommended that enterprises categorize high-severity vulnerabilities based on three factors: if the flaws are remotely exploitable, if there are known public exploits and if there are known solution details. Though timely patching remains a struggle for many organizations, Flashpoint said the prioritization model can help vulnerability management teams reduce their critical workloads by 85%.
The report also highlighted the value of "well-trained and auditable artificial intelligence and machine learning technologies" in detecting risks and sophisticated cyberthreats, though Flashpoint also stressed the need for human intelligence to complement such technologies.
Data breaches surge
Ransomware attacks were a major contributor to the 34.5% jump in data breaches in 2023. Operators increasingly leveraged brazen data extortion threats to pressure payments from victim organizations. The manufacturing and technology industries felt the brunt of it; Flashpoint analysts discovered that ransomware and unauthorized access accounted for more than 85% of all publicly disclosed breaches for organizations in those sectors. One prime example was Western Digital, which disclosed an attack in April.
Overall, Flashpoint analysts recorded 6,077 global data breaches in 2023 that leaked more than 17 billion personal records, and U.S. organizations accounted for the majority.
However, Flashpoint found that many incidents stemmed from attackers gaining unauthorized access to third parties. One prime example was the extensive threat campaign against customers of Progress Software's MoveIt Transfer product. While there was no actual ransomware deployment, the Clop ransomware group exploited a zero-day vulnerability in MoveIt Transfer that subsequently affected thousands of organizations.
"Flashpoint analysts determined that the MOVEit attack was responsible for 19.3% of all reported 2023 data breaches. This figure includes affected third-parties, organizations who were not directly compromised by Cl0p, but had sensitive data stolen from vendors within their supply chain," the report said.
The problem has worsened in 2024. The report emphasized that the amount of stolen data from Jan. 1 to Feb. 29 increased by 429% compared with the same period last year. Ransomware attacks and unauthorized access continue to be the primary culprits.
Ian Gray, vice president of cyberthreat operations at Flashpoint, told TechTarget Editorial that misconfigurations and unintentional data loss also contributed to the year-over-year rise in data breaches, which includes accidentally leaving containers and storage buckets exposed to the public internet. To prevent such incidents, he urged enterprises to check their access points and secure APIs.
Regarding ransomware, Gray said he believes the already staggering numbers would be higher if undisclosed attacks were included. He emphasized that the ransomware as a service (RaaS) ecosystem incentivizes enterprises to pay by threatening to publicly leak stolen data and causing prolonged disruptions to business operations. Enterprises often weigh the consequences of daily losses with ransom demand amounts.
He urged companies to verify whether ransomware actors are bluffing in regard to their stolen data claims. Flashpoint observed several instances of false claims from the RansomedVC ransomware group in 2023, for example.
"They're incentivizing companies to pay through as many measures as possible by giving them a way not to disclose incidents," Gray said.
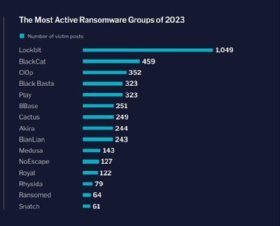
Flashpoint, like other vendors, found that the LockBit ransomware gang was by far the most active in 2023 with 1,049 victims, followed by the Alphv/BlackCat ransomware gang with 459.
Despite an international law enforcement action dubbed "Operation Cronos" that temporarily disrupted LockBit last month, the group remains strong in 2024. Vendors attributed recent attacks on ConnectWise ScreenConnect customers to the gang, and Flashpoint tracked 154 victims on its public leak site within the first two months of 2024. The report emphasized that the number was "almost triple" compared with the second-most active groups, 8Base and Alphv/BlackCat.
Alphv/BlackCat was also temporarily disrupted by law enforcement last year. The takedowns have led to shifts in the RaaS ecosystem.
"We're also seeing something interesting with cross-posting of different victims," Gray said. "I've seen a minor instance of that last week or the week before where a victim appeared both in LockBit and BlackCat [leak sites]. BlackCat was taken down first, so we saw LockBit say, 'Hey affiliates, if you want to, come over here.'"
Although LockBit resumed operations following Operation Cronos, Gray remains optimistic about law enforcement actions and their effect on the threat landscape moving forward. During last month's announcement, the U.S. Department of Justice revealed how much cryptocurrency law enforcement agencies were able to seize from LockBit. Gray anticipates that agencies might now be able to trace the funds to identify ransomware operators across other RaaS groups.
"We're seeing this cat-and-mouse game, but I think we're seeing it tilt more toward law enforcement this time," he said. "I think things are definitely going to be getting better across the landscape. And I don't think there's a one-pill solution, obviously, but it's about working together, transparency, disclosure and understanding."
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.