
Getty Images/iStockphoto
Apple unveils PQ3 post-quantum encryption for iMessage
Apple said its new PQ3 protocol for iMessage is the first of its kind and addresses both future threats from quantum computing as well as "harvest now, decrypt later" attacks.
Apple on Wednesday introduced PQ3, a post-quantum cryptographic protocol for iMessage that the tech giant said has "the strongest security properties of any at-scale messaging protocol in the world."
In a research blog post, Apple said PQ3 addresses the threat posed by quantum computing, which could theoretically crack modern cryptographic protocols and jeopardize the security of encrypted data and communications. The post-quantum encryption protocol also addresses current threats such as "harvest now, decrypt later" attacks, in which threat actors steal large amounts of data and hoard it until they have the quantum computing capabilities to decrypt it in the future.
Apple said PQ3 has security properties that are strong enough to merit being considered "Level 3" security -- a communication security term Apple dubbed for itself as part of the announcement. Currently, communication security is known by three security levels: Level 0 security, in which messages are unencrypted; Level 1, for messages are encrypted end to end but have no additional identity authentication or quantum security; and Level 2, which has identity authentication and quantum security.
While Apple wrote in the blog post that Signal's recent support for the PQXDH messaging protocol made it "the first large scale messaging app to introduce post-quantum security" and worthy of Level 2, PQ3's features merit an additional, previously non-existent security level.
"At Level 2, the application of post-quantum cryptography is limited to the initial key establishment, providing quantum security only if the conversation key material is never compromised," Apple wrote. "But today's sophisticated adversaries already have incentives to compromise encryption keys, because doing so gives them the ability to decrypt messages protected by those keys for as long as the keys don't change."
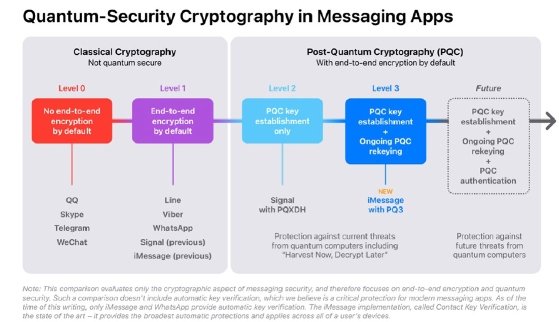
PQ3 introduces a new post-quantum encryption key within the set of public keys each Apple device generates locally and transmits to Apple servers as part of the iMessage registration process. A complete retooling of iMessage security, PQ3 uses Kyber's post-quantum public keys as the protocol's algorithm, Apple said. "This enables sender devices to obtain a receiver's public keys and generate post quantum encryption keys for the very first message, even if the receiver is offline."
Along with generating a post-quantum encryption key, PQ3 has additional security features such as a rekeying mechanism within iMessage conversations that Apple said "has the ability to self-heal" from key compromises.
"In PQ3, the new keys sent along with the conversation are used to create fresh message encryption keys that can't be computed from past ones, thereby bringing the conversation back to a secure state even if previous keys were extracted or compromised by an adversary," the blog post read. "PQ3 is the first large scale cryptographic messaging protocol to introduce this novel post-quantum rekeying property."
Because PQ3's post-quantum key has a larger wire size than the current protocol's key, the rekeying is performed periodically within conversations, rather than with each message, to maintain the message size requirement. Apple said the rekeying condition is designed to balance the average size of messages on the wire while preserving the user experience and to keep the global message volume under the capacity of the company's server infrastructure. "Should the need arise, future software updates can increase the rekeying frequency in a way that's backward compatible with all devices that support PQ3," the blog post read.
During a press briefing Tuesday, an Apple spokesperson said PQ3 will begin rolling out in the public releases of iOS 17.4, iPadOS 17.4, macOS 14.4 and watchOS 10.4. The spokesperson said deployment will continue through the rest of the year and replace the existing encryption protocol in all supported devices.
Apple's announcement follows the Linux Foundation's launch of the Post-Quantum Cryptography Alliance, which aims to drive the further adoption of post-quantum encryption while addressing relevant challenges.
Omkhar Arasaratnam, general manager of the Open Source Security Foundation (OpenSSF), told TechTarget Editorial that PQ3 makes a significant stride toward achieving quantum secure messaging on a broader scale. In particular, he complimented Apple's combination of post-quantum and traditional encryption ciphers.
"This novel approach holds promise in providing robust defense against potential adversaries aiming to intercept and decrypt encrypted traffic in the future," he said in an email. "Apple's pioneering deployment of a hybrid PFS [Perfect Forward Secrecy] pattern on a large scale is poised to strike a delicate balance between the performance implications of rekeying and the imperative of maintaining confidentiality."
Alexander Culafi is an information security news writer, journalist and podcaster based in Boston.








