
Getty Images/iStockphoto
CISA: Volt Typhoon had access to some U.S. targets for 5 years
A joint cybersecurity advisory expanded on the Volt Typhoon threat Wednesday, confirming attackers maintained prolonged persistent access to critical infrastructure targets.
U.S. government agencies issued another warning about the significant threat posed by a Chinese nation-state threat group to critical infrastructures, revealing attackers might have been lurking in victims' IT environments for several years.
Last week during a hearing before the House Select Committee on Strategic Competition Between the United States and the Chinese Community Party, CISA Director Jen Easterly and FBI Director Christopher Wray warned that Chinese nation-state actors had positioned themselves in critical infrastructure organizations for future attacks. Potential targets included organizations in the energy, water and telecommunications sectors. The hearing was held in the wake of the Department of Justice's disruption of a botnet campaign by a Chinese threat group, known as Volt Typhoon, that infected U.S.-based SOHO routers.
In a joint cybersecurity advisory Wednesday, CISA, the FBI and the National Security Agency echoed the warning and confirmed that Volt Typhoon compromised organizations in the communications, energy, transportation systems, and water and wastewater sectors. CISA posted an incident response guide in January for water utilities, highlighting an ongoing threat.
Like Easterly and Wray, Wednesday's advisory alerted critical infrastructures to an impending threat by the elusive threat actor. CISA said Volt Typhoon has gained access to the IT environments for multiple critical infrastructure entities in the "event of a major crisis or conflict with the United States." The advisory confirmed Volt Typhoon held access to some environments for an alarming amount of time.
"In fact, the U.S. authoring agencies have recently observed indications of Volt Typhoon actors maintaining access and footholds within some victim IT environments for at least five years," the agencies wrote in the advisory.
The warnings and threat intelligence outlined in the advisory are based on CISA, NSA and FBI incident response investigations that involved Volt Typhoon. During those investigations, the agencies discovered that Volt Typhoon activity did not align with cyber espionage purposes and determined there is a bigger play at hand that could put operational technology (OT) systems of critical infrastructure organizations at risk.
"The U.S. authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT assets to disrupt functions," the advisory said. "The U.S. authoring agencies are concerned about the potential for these actors to use their network access for disruptive effects in the event of potential geopolitical tensions and/or military conflicts."
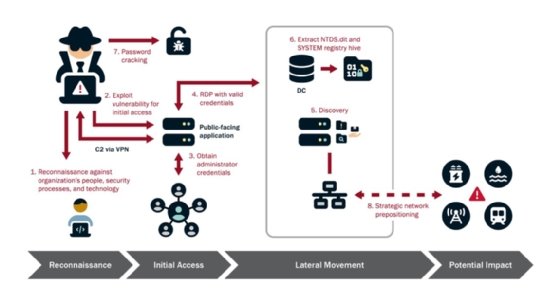
Patience and persistence
Volt Typhoon is dangerous due to its extensive reconnaissance capabilities, discoveries and usage of zero-day vulnerabilities, and evasion techniques. U.S agencies even observed the actors targeting the personal emails of key network and IT staff in targeted organization. To gain initial access to a victim environment, Volt Typhoon is known to leverage both zero-day and known vulnerabilities in networking appliances.
The agencies urged organizations to secure internet-facing devices, which Volt Typhoon has targeted in the past. The joint advisory noted the group has gained access to IT networks by exploiting known or zero-day vulnerabilities in routers, VPNs and firewalls.
The agencies warn that Volt Typhoon typically exploited vulnerabilities in network devices from Fortinet, Ivanti Connect Secure, Netgear, Citrix and Cisco as primary Volt Typhoon initial access targets.
"In one confirmed compromise, Volt Typhoon actors likely obtained initial access by exploiting CVE-2022-42475 in a network perimeter FortiGate 300D firewall that was not patched. There is evidence of a buffer overflow attack identified within the Secure Sockets Layer (SSL-) VPN crash logs," the advisory read.
Volt Typhoon attacks have been publicly reported in the past, although it was previously not known that the group had contingency plans to launch disruptive attacks. In June, Carl Windsor, senior vice president of product technology and solutions at Fortinet, warned users that Volt Typhoon would likely exploit a critical Fortinet SSL VPN vulnerability, tracked as CVE-2023-27997.
Microsoft issued a similar warning the previous month, noting that Volt Typhoon was gaining initial access to critical infrastructure organizations through internet-facing Fortinet FortiGuard devices. Microsoft observed attacks against U.S. and Guam based communications, manufacturing, government, and transportation sectors, although at the time the company believed the activity was part of a cyber espionage effort.
The advisory said Volt Typhoon actors are also adept at leveraging credential access, often with administrative privileges, to move laterally within an environment. Those credentials are often stolen from poorly protected public-facing network appliances, the agencies warned.
In some instances, the agencies said threat actors used elevated credentials to gain OT access and take control of critical equipment and assets.
The advisory warned that access could lead to the compromise of heating, ventilation and air condition systems in server rooms or disrupt critical energy and water controls. The agencies confirmed that in some cases, Volt Typhoon also gained access to camera and surveillance system within critical infrastructure facilities.
Volt Typhoon actors exhibit significant patience after using credentials to gain access to legitimate accounts. The advisory emphasized that Volt Typhoon's objective is to maintain persistence within targeted organizations.
"This assessment is supported by observed patterns where Volt Typhoon methodically re-targets the same organization over extended periods, often spanning several years, to continuously validate and potentially enhance their unauthorized access. Evidence of their meticulous approach is seen in instances where they repeatedly exfiltrate domain credentials, ensuring access to current and valid accounts," the advisory read.
The agencies urged critical infrastructure to take immediate action to mitigate Volt Typhoon activity. Recommendations included patching internet-exposed systems and to prioritize patching vulnerabilities that Volt Typhoon frequently exploits; implementing phishing-resistant multifactor authentication; and review account permissions on edge appliances and network devices and removed any domain administrator privileges.
Arielle Waldman is a Boston-based reporter covering enterprise security news.







