
Getty Images
Chainalysis: 2023 a 'watershed' year for ransomware
Chainalysis said ransomware payments ballooned to reach $1.1 billion in 2023, marking a complete reversal from the decline in ransomware payments seen the year prior.
Listen to this article. This audio was generated by AI.
Ransomware payments surpassed $1 billion last year according to new research from Chainalysis, leading the Blockchain analytics vendor to call 2023 a "watershed" year for the attack type.
2022 was generally seen as a down year for ransomware. CrowdStrike saw the average ransom payment drop from $5.7 million in 2021 to $4.1 million in 2022; Mandiant said it responded to 15% fewer ransomware incidents in 2022 than the previous year. But while 2022 saw various declines on the ransomware front, experts cautioned that reality was more complicated than numbers suggested.
A significant number of threat actors in 2022 pivoted from ransomware attacks to data extortion-only attacks where cybercriminals stole data in the hopes of getting paid without encrypting victim networks. Another factor was that Russia's invasion of Ukraine pulled at least some attention away from financially motivated cybercrime and toward politically motivated attacks.
Chainalysis on Wednesday published a blog post detailing new research and observations regarding ransomware trends last year. The vendor said 2023 marked a "major comeback" for ransomware, something it warned about last year. According to the company, ransomware payments reached $1.1 billion in 2023 -- the highest ever recorded -- compared to $567 million in 2022 and $983 million in 2021.
"It is important to recognize that our figures are conservative estimates, likely to increase as new ransomware addresses are discovered over time," the blog post read. "For instance, our initial reporting for 2022 in last year's crime report showed $457 million in ransoms, but this figure has since been revised upward by 24.1%."
The vendor also called 2022 an "anomaly." In addition to the aforementioned factors, Chainalysis said 2022 was a down year due to FBI's takedown of the Hive ransomware gang. In January 2023, the U.S. Department of Justice announced that the FBI completed a months-long infiltration of the Hive ransomware gang, in which the agency managed to prevent victims from paying $130 million in ransomware payments. Based on its research and factors like knock-on effects for Hive affiliates, Chainalysis estimates that the FBI's takedown could have "averted at least $210.4 million."
2023, meanwhile, featured an expansion of ransomware as a service (RaaS) as well as several big game attacks.
"The ransomware landscape underwent significant changes in 2023, marked by shifts in tactics and affiliations among threat actors, as well as the continued spread of RaaS strains and swifter attack execution, demonstrating a more efficient and aggressive approach," Chainalysis said. "The movement of affiliates highlighted the fluidity within the ransomware underworld and the constant search for more lucrative extortion schemes."
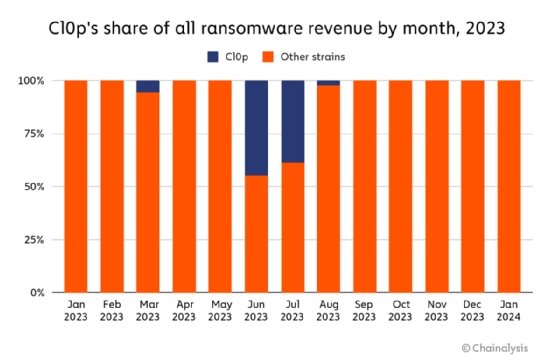
Perhaps the most infamous example of large-scale extortion activity was Clop's massive campaign against customers of Progress Software's managed file transfer product MoveIt Transfer beginning in May of last year. The Clop gang utilized a zero-day vulnerability in the product and launched many data extortion attacks against customers. Chainalysis said that since Clop's campaign began, the gang received more than $100 million in ransom payments, which represented 44.8% of all ransomware value received in June and 39% in July.
"With so many targets, encrypting data and distributing decryptor keys to those who pay becomes logistically impractical," Chainalysis said. "Data exfiltration -- stealing data without blocking access and threatening to release it to the public -- proves to be a more efficient tactic and hedges against possible decryptors foiling the attack."
Wednesday's report provided a more detailed view of previous research from Chainalysis. The company published the introduction to its "2024 Crypto Crime Trends" report on Jan. 18, which showed an overall decline in illicit cryptocurrency activity in 2023, falling to $24.2 billion compared to $39.6 billion in 2022. Chainalysis found a decrease in cryptocurrency scamming and hacking but warned that ransomware activity for the year had risen and reversed the sharp decline observed in 2022.
Jacqueline Burns Koven, head of cyber threat intelligence at Chainalysis, told TechTarget Editorial that the key to making long term progress is disrupting the entire ransomware supply chain, which includes developers, affiliates, infrastructure service providers, launderers and cash-out points.
"Many agencies and entities are doing good work to prevent and disrupt ransomware, and we have seen that success here decreases ransomware revenue and makes it harder for these actors to cash out their ill-gotten gains," Burns Koven said.
"Beyond looking into ransomware strains, we need to focus on the individuals behind them, to name and shame them, and continue sanctioning. Sanctions and naming and shaming are disruptive to these bad actors because while the strains constantly change and rebrand, the individuals behind them are the real drivers."
Alexander Culafi is an information security news writer, journalist and podcaster based in Boston.







