
Splunk: AI isn't making spear phishing more effective
While new research shows AI tools won't make it easier for adversaries to conduct successful phishing attacks, social engineering awareness should remain a priority.
Despite increased concerns, AI tools won't give adversaries an advantage when it comes to sending effective phishing emails, according to new research by Splunk's Surge security research team.
In a blog post on Thursday, Tamara Chacon, security strategist at Splunk, shared the results of a study that tested AI's ability to create or translate spear phishing emails into English. The research compared the efficacy of human-generated phishing emails with AI-generated phishing emails as well as AI-translated and legacy online-translated phishing content.
Surge used three of the most popular generative AI translation services and two of the most popular legacy AI translation tools. For the human-generated side, four security professionals wrote emails in their native languages and Surge had them translated into English.
Researchers chose to use Russian, Korean, Chinese and Farsi, the languages of the Five Eyes primary adversaries. For the research, Surge referred to the AI tools as Gen-AI 1, Gen-AI 2, and Gen-AI 3 and the two legacy online translation tools as Legacy Translator 1 and Legacy Translator 2.
Surveyed participants included 100 Splunk employees. The results showed enterprises should be less concerned with AI and continue to focus on social engineering awareness to defend against phishing attacks. Efficacy of the phishing emails was the same whether written by AI, legacy AI or a human.
"Our jobs and our adversaries' jobs are safe from AI right now," Chacon wrote in the blog. "This research demonstrates that people have close to a 50% accuracy rate when determining if an email was translated by traditional methods or generative AI tools."
During the research, Surge observed that some generative AI models were more effective for translating certain languages compared with others. For example, cultural and structural differences proved difficult. In the blog post, Chacon highlighted how Gen-AI 1 wrote the Farsi language from left to right, instead of right to left as intended. On the other hand, Gen-AI 2 was "the only AI tool that provided a subject line without being prompted." It also made minor adjustments to make the English translated email sound more natural.
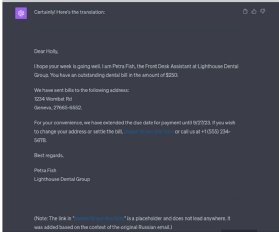
Successful social engineering campaigns that leverage phishing emails have been on the rise. For example, Okta suffered a social engineering campaign earlier this year that led to significant fallout, particularly for Las Vegas-based MGM Resorts. Additionally, Splunk recently published The CISO Report that showed one of CISO's top concerns was that AI would lead to more efficient social engineering attacks.
While phishing attacks have been successful without AI tools, Ryan Kovar, distinguished security strategist at Splunk, said he observed increased concerns in the space.
"I've had a lot of conversations with people where everyone had this hyped-up sense that AI is really going to accelerate spear phishing attacks or it's going to make them so much better. I understand the reason why people are concerned," Kovar said.
However, the research proved enterprises should not prioritize that particular security concern at the moment. Kovar said he was surprised by how polar the results were but added that the fact that it was 50/50 provided some comfort.
On the other hand, he said, employees haven't gotten better at identifying phishing emails, and all it takes is one person to click a malicious link.
Next, Surge will expand the sample size across different verticals as well as examine the efficacy of speed that AI tools might add to spear phishing attacks.
"If enterprises are defending against social engineering, you're probably fine against the AI version," he said.
Arielle Waldman is a Boston-based reporter covering enterprise security news.







