
Getty Images/iStockphoto
Black Basta ransomware payments exceed $100M since 2022
Insurance provider Corvus and blockchain analytics vendor Elliptic partnered to examine how much damage the Black Basta ransomware group has caused in less than two years.
The Black Basta ransomware gang accrued more than $107 million in ransom payments from more than 90 victims over the past year and a half, according to new research from Corvus Insurance and blockchain analytics vendor Elliptic.
The joint research was documented in blog posts Wednesday from Corvus and Elliptic. Using blockchain analysis, the research shed light on Black Basta ransom payment amounts, the number of victims and the top targeted sectors. The vendors also confirmed reports that linked Black Basta to the notorious Conti ransomware group, which disbanded around May 2022.
The vendors acknowledged that while the concept of blockchain is transparent, ransomware groups are skilled at obfuscating their tracks. Corvus and Elliptic described operators' laundering techniques as "complex" and said ransomware groups rarely use a single cryptocurrency wallet to receive payments. The illicit funds might be rerouted through multiple wallets to make it more difficult for law enforcement to track them. Lack of transparency from victims also makes it hard to gather wallet details, the companies said.
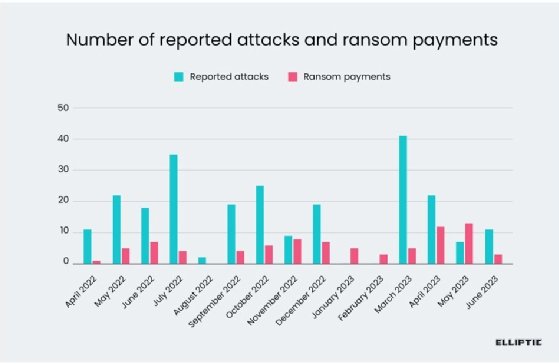
While difficult, the vendors traced illicit activity to provide further insight on the "fourth-most active strain of ransomware by number of victims in 2022-2023." After emerging in 2022, Black Basta showed how dangerous it could be by claiming more than 329 victims, including Capita, ABB and Dish Network. Dish apparently paid the ransom demand after suffering an outage.
"Based on the number of known victims listed on Black Basta's leak site through Q3 of 2023, our data indicates that at least 35% of known Black Basta victims paid a ransom. This is consistent with reports that 41% of all ransomware victims paid a ransom in 2022," the companies wrote in the report.
Blockchain analysis indicates that Black Basta received at least $107 million in ransom payments since early 2022 spread out across more than 90 victims. Operators took an average of 14% of the ransom payments, which Corvus and Elliptic said is typical of ransomware-as-a-service operations.
According to the research, the largest ransom payment Black Basta received was $9 million, and the average payment was $1.2 million. At least 18 of the ransoms exceeded $1 million.
Ryan Bell, Corvus' threat intelligence manager, was most surprised by the sheer monetary impact of the Black Basta ransomware group.
"It's quite an achievement for any legitimate company to make $100M in revenue, but here we see a gang of cybercriminals able to do it in roughly a year and a half. As just one among dozens of active ransomware groups, this research gives us a 'tip of the iceberg' view on just how large the financial impact of ransomware is," Bell said in an email to TechTarget Editorial.
However, the true numbers for Black Basta are likely much higher than the numbers cited in the research. Elliptic said the figures don't account for the most recent Black Basta ransom payments. Due to Black Basta and Conti's overlapping timeline, it was also difficult for the vendors to determine if some of the payments were related to Conti ransomware attacks.
Conti connection
In its heyday, Conti conducted highly disruptive attacks, including one against the Irish healthcare system and another against Costa Rican government agencies in 2022. ExaGrid Systems suffered a Conti attack in 2021 that led to a $2.6 million ransom payment.
However, Conti apparently started to dismantle its operations following leaked source code in March 2022 that revealed the ransomware group had received more than $2 billion in cryptocurrency since 2017. By May, vendors and researchers reported that Conti websites were no longer operating. However, several vendors discovered evidence that Conti operators had rebranded as other groups, including Black Basta.
Corvus and Elliptic's research further corroborated those reports.
"In particular, we have traced bitcoin worth several million dollars from Conti-linked wallets to those associated with the Black Basta operator. This further strengthens the theory that Black Basta is an offshoot or rebrand of Conti," the blog said.
Other evidence that tied Russian-linked Black Basta to Conti included the targeted victims and the cryptocurrency exchange both groups used to hide illicit payments. Corvus and Elliptic found overlaps in the targeted sectors such as construction, law practices and real estate.
Elliptic's blockchain analysis also traced millions of laundered ransom payments to Garantex, the Russian cryptocurrency exchange that was sanctioned by the U.S. government in 2022. The Treasury Department's Office of Foreign Assets Control said the virtual currency exchange laundered more than $100 million in illicit funds that included ransom payments from gangs such as Conti.
While examining payment trails, the vendors also found that portions of some victims' ransoms were sent to wallets of Qakbot operators. Qakbot malware sent through phishing emails was commonly used to deploy Black Basta ransomware as well as others, including Conti.
"These transactions indicate that approximately 10% of the ransom amount was forwarded on to Qakbot, in cases where they were involved in providing access to the victim. Qakbot was disrupted in August 2023 by a multinational law enforcement operation -- perhaps explaining a marked reduction in Black Basta attacks in the second half of 2023," the blog said.
In its conclusion, Corvus recommended that enterprises prioritize email protection and endpoint detection and response products. Those are crucial, the blog said, because Black Basta relies on info stealers and Trojans such as Qakbot to gain initial access to victim organizations. Corvus also advised using multifactor authentication, especially to secure remote access and administrative accounts, and prioritizing patch management to reduce vulnerabilities leveraged by attackers.
Arielle Waldman is a Boston-based reporter covering enterprise security news.






