
kras99 - stock.adobe.com
Coalition looks to bridge gap between CISOs, cyber insurance
While carriers and CISOs agree cyber insurance has contributed to better security postures, Coalition said the relationship needs to stronger as threat evolve and intensify.
LAS VEGAS -- As the threat landscape shifts and intensifies, one cyber insurance carrier is urging CISOs to play a more active role in policies and work more closely with insurers.
Catherine Lyle, head of claims at Coalition, presented a Black Hat USA 2023 session Wednesday titled "Why Cyber Insurance Should Be Your SOC's New Best Friend" where she discussed how threat actors' growing sophistication is affecting both the insurers and the insured. While many threats to enterprises remain consistent, such as phishing, funds transfer fraud (FTF), ransomware attacks and business email compromise (BEC), evolving techniques are contributing to a higher success rate.
During the session, Lyle emphasized that insurers, IT departments and enterprise security teams have a shared mission: to adapt to the shifting cybercrime landscape where threat actors apply increased pressure with aggressive extortion tactics. Speaking with TechTarget Editorial prior to the conference, she described the Black Hat USA 2023 session as a "very frank discussion with CISOs."
"This falls to you [CISOs], and you really need to be active and participate in this. It's not something you can think that security is going to solve it all, because it's not. Time and time again, that's been proven," Lyle said.
Insurers vs. CISOs
While there has been contention between insurers and CISOs as premiums increase and coverage in some policies decreases, Lyle listed ongoing security assessments, patch alerts and retrieving stolen funds as incentives for cyber insurance. Lyle said Coalition is also working on building forensic relationships to assist insured organizations with incident response.
"CISOs think when an event comes, they know exactly what to do. But I would say the majority don't," she said. "Having tabletop exercises and incident response plans are important, and they don't have to be super intense. Just know who you have to call when something's gone wrong. And don't tell me you're just going to email someone, because your email is probably down."
Fawaz Rasheed, field CISO at VMware, spoke with TechTarget Editorial about the problems he faces with cyber insurance policies. The number one concern is higher premiums and lesser protections. One responsibility he has as a CISO is to attempt to keep those premiums as low as possible because there can be pushback from leadership on the security budget.
It can also be tough to justify implementing all the new requirements insurers pose. But coverage does depend on meeting certain standards like having MFA and endpoint detection and response. "There is an understood notion that premiums are increasing and then the inverse proportion with coverage, so I can't rely on cyber insurance as much as I have to make sure I have my ducks in a row on the front end and to make sure that we are better protected," Rasheed said, adding that cyber insurance is currently more of a fallback.
However, he also recognized that insurance carriers' new security requirements are contributing to better security postures. He spoke to other CISOs who said cybersecurity vendors are demanding they have cyber insurance coverage.
Lyle emphasized that insurance carriers are there to help organizations in far more ways than they may think. "Many CISOs think that somehow insurance companies are going to make it worse, and I promise you, it makes it better. Our job is to make sure they're getting the most out of their product."
Part of that assistance, in Coalition's case, includes identifying threats and attack trends while also advising customers on how to shrink their attack surfaces.
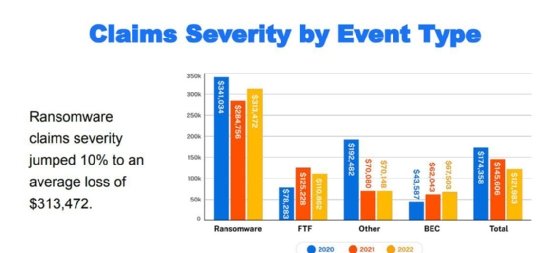
Claims trends and increasing threats
Based on Coalition customer claims, threat actors have become more effective of late, particularly when it comes to ransomware. Coalition observed ransomware attacks increased 27% from the second half of 2022 to the first half of 2023. During those attacks, ransomware operators demanded an average of $1.4 million, according to customer data from the first half of this year. The growth of ransomware as a service has contributed to the threat's growing sophistication because operators and affiliate hackers are now sharing stolen credentials, Lyle said.
"They've realized how they're specialized and then sell what they're doing. They have monetized every aspect of their crime," she said.
Lyle also highlighted phishing, which was the attack vector in 76% of Coalition customer claims in 2022. Phishing emails often led to ransomware attacks, BEC and FTF.
Defending against FTF attacks, which Lyle said surpassed ransomware in 2022 as a top threat, was a major focus for Coalition last year. The insurer observed dwell time in FTF events increased from 24 days in 2021 to 42 days in 2022, which meant threat actors took longer to plan their attacks. Lyle emphasized the dangers of that increased patience.
Now attackers maintain persistence to find all the necessary details to deploy a successful social engineering attack. For example, they can find out who's in charge of the checkbook and who they need to trick to get those funds transferred. In some cases, Lyle said attackers used AI technology like ChatGPT to craft more legitimate looking emails free of misspellings and grammar mistakes.
While FTF attacks were successful in some cases, more than $18 million in stolen Coalition customer funds have been seized so far this year. Lyle detailed a case study based on a union customer that lost $6.5 million during an FTF incident. Coalition worked with law enforcement agencies and banking institutions to recover $5.4 million. Lyle emphasized that Coalition has made a conscious effort to focus more on seizing back stolen funds.
Patch, patch, patch
In terms of enterprise attack surfaces, Lyle said end of life (EOL) software remains a concern for enterprises. Coalition determined that organizations using EOL software were three times more likely to be attacked.
"It's the quickest way for a threat actor to get in, so get it offline," Lyle said.
The most important defense against many of the security threats is to implement efficient vulnerability patch management protocols, Lyle said. Timely patching is an ongoing problem, as organizations are faced with an insurmountable number of flaws and don't have the workforce to address them all. Lyle said Coalition is making it easier for enterprises with alerts and prioritization methods.
"Patching is not super complex. It's made to be simple. And so while some of these small and medium-sized companies might not have somebody that's assigned this as their job, they're going to do it. And it's super important … making sure that patch and data information gets to right people," Lyle said.
When it comes to ransomware, Lyle urged enterprises to maintain efficient backups for recovery and implement MFA, which is increasingly important as threat groups share and abuse stolen credentials.
Arielle Waldman is a Boston-based reporter covering enterprise security news.







