
kras99 - stock.adobe.com
Onapsis researchers detail new SAP security threats
At Black Hat 2023, Onapsis researchers demonstrated how attackers could chain a series of SAP vulnerabilities impacting the P4 protocol to gain root access to a target network.
Onapsis researchers unveiled new attacks vectors for SAP that combine existing vulnerabilities for potentially devastating chained exploits.
Pablo Artuso, lead security researcher at Onapsis, presented the attacks with fellow researcher Yvan Geuner in a Black Hat 2023 session Wednesday titled "Chained to Hit: Discovering New Vectors to Gain Remote and Root Access in SAP Enterprise Software." In the session, the researchers demonstrated how they combined three different attacks to gain root access into the SAP system.
The various attacks involved chaining SAP enterprise software vulnerabilities, many of which received high and critical CVSS scores. Prior to the Black Hat conference, Artuso and Onapsis CTO JP Perez-Etchegoyen spoke with TechTarget Editorial about the research.
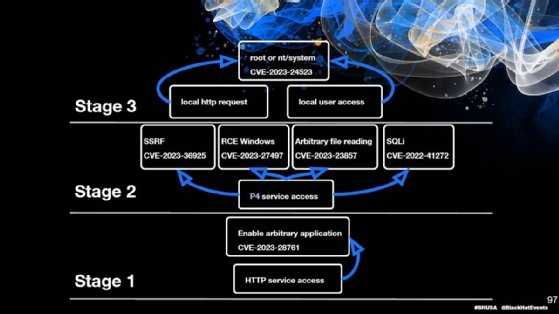
The attacks demonstrated during the session combined three different research projects at Onapsis. By chaining the projects, researchers discovered if they gained HTTP access, they could obtain root access into the SAP system with no authentication required.
After gaining HTTP access to a target network, which is the first step, the researchers exploited an SAP NetWeaver Enterprise Portal flaw, tracked as CVE-2023-28761, which gave them ability to arbitrarily launch applications without authorization. The vulnerability also allows an unauthenticated attacker to eventually access or modify server settings and data.
From there, the Onapsis researchers moved to a crucial part of the attack chain that involved a proprietary SAP protocol called P4 and is based on Remote Method Invocation, which is a Java API. P4 is present in all SAP NetWeaver Application Servers for Java and is designed to facilitate remote communications. On the bright side, Onapsis researchers say P4 services are rarely exposed to the internet.
On the other hand, the service can cause significant damage in the wrong hands. In Spring, Onapsis disclosed a series of vulnerabilities that it called "P4Chains," some of which impact the protocol and are used in the new chained attacks. In a report titled "P4Chains:
Unpacking the Impact of Vulnerabilities Affecting SAP P4," Onapsis explained that obtaining access to the protocol can make seemingly less-severe vulnerabilities far more dangerous.
"Even though the exploitation of these issues is, under most circumstances, limited to local networks, there are configurations and vulnerabilities that attackers could use in combination with the vulnerabilities affecting P4 services, which ultimately leads to potentially
exploiting these issues over the HTTP(s) protocol, even over the internet," the report read.
After exploiting the NetWeaver Enterprise Portal flaw, Onapsis researchers gained access to the P4 service, which is stage two of the attacks. The researchers then exploited CVE-2023-23857, a DoS and OS file arbitrary read vulnerability that impacts P4 and has a CVSS score of 9.9, and CVE-2023-27497, a remote code execution vulnerability in the SAP Diagnostics Agent that has a CVSS score of 10.
Other flaws exploited during stage two of the attacks include a server-side request forgery vulnerability in SAP Solution Manager, tracked as CVE-2023-36925 with a 7.2 CVSS score. Another flaw that received a critical CVSS score of 9.9 was an SQL injection flaw, tracked as CVE-2022-41272, which also impacts the P4 service.
The attacks culminate with Stage 3, where the researchers use local HTTP requests or local access and exploit CVE-2023-24523, a privilege escalation vulnerability in SAP Host Agent that has an 8.8 CVSS score, to achieve root access to the target system.
Onapsis researchers provided an extensive list of flaws that enabled the attacks and urged enterprises to patch all of them, even though some may appear to have lower severity. The presentation showed threat actors can take several different exploitation paths to reach Stage 3 and achieve root access.
The attacks don't require a particularly advanced threat actor, the researchers said, but SAP knowledge is essential. Artuso described the level of difficulty to execute the chain as medium. "Besides exploitation level, attackers would need SAP knowledge and internal knowledge [of the target network] to be able to exploit the vulnerabilities," Artuso said.
While many of the flaws were critical, there was good news for the defense. If enterprises mitigate one step, the entire chain is compromised, Perez-Etchegoyen said. That could include patching only one component and highlights the importance of configuring access control lists (ACLs).
SAP security in the spotlight
Artuso emphasized how critical SAP security is for enterprises. "SAP systems are also vulnerable because most people tend to overlook their security. We would like to highlight the fact that SAP systems are there and may be vulnerable, and [enterprises] have to pay attention to security," Artuso said.
Threat actors' increased interest in SAP is another reason security awareness is important. Currently, attackers can exploit SAP applications, both manually and automated. Another evolution Perez-Etchegoyen' highlighted related to malware and ransomware.
"In the past SAP, applications have been kind of left aside from the security perspective. But over the past couple of years, threat actors have been incorporating them on their campaigns, targeting active exploitation [and] updating malware and ransomware to be able to understand those applications to capture credentials and to get information for those processes and services," Perez-Etchegoyen said.
While SAP applications don't necessarily contain more vulnerabilities than other software, Perez-Etchegoyen's main concern is enterprises' preparedness level when it comes to addressing SAP software. He has observed an improvement in enterprises' SAP vulnerability patch management but believes there is still work to be done.
"In very few cases, they are out of band patches. But in the majority of cases, there are patches available. Enterprises need to have the processes and the resources to be able to address that just like they do with every other software in their landscape," Perez-Etchegoyen said.
Resources include staying up to date with Patch Tuesday alerts and configuring specific ACLs to restrict access to certain services.
Arielle Waldman is a Boston-based reporter covering enterprise security news.






