
Getty Images/iStockphoto
Chainalysis observes sharp rise in ransomware payments
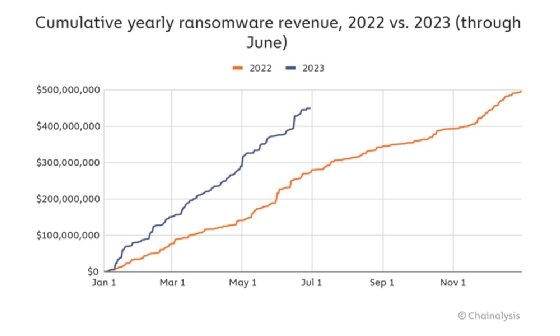
The rise in total ransomware payments so far this year is a reversal of the decline Chainalysis saw in 2022, when payments fell sharply to $457 million from $766 million in 2021.
Ransomware gangs might not be encrypting victims' data as much as they used to, but they're still making millions from their attacks.
According to new research from cryptocurrency analytics firm Chainalysis, ransomware actors have already extorted at least $449.1 million through the first half of this year, which is $175.8 million more than they pulled in during the same period in 2022. The rise in total ransomware payments stood in sharp contrast to illicit payments for other cybercrime activity such as scams, which have fallen 65% so far this year, according to Chainalysis' "Crypto Crime Mid-year Update."
The increase comes after Chainalysis observed a significant decline in ransomware payments for 2022, falling to $457 million from $766 million in 2021. The company attributed the drop to fewer victims opting to pay the ransom, as well as the effects of law enforcement actions and sanctions against cryptocurrency exchanges that allegedly facilitate ransomware payments and other illicit transactions.
"Why the reversal in fortunes? For one thing, big game hunting -- that is, the targeting of large, deep-pocketed organizations by ransomware attackers -- seems to have bounced back after a lull in 2022," Chainalysis wrote in the report. "At the same time, the number of successful small attacks has also grown."
The cryptocurrency analytics firm also said Russia's invasion of Ukraine in February 2022 had an effect on last year's decline in ransomware payments and overall threat activity, "as the conflict likely displaced ransomware operators and diverted them away from financially inspired cyber intrusions."
The Chainalysis report cited research from Kivu Consulting, a cybersecurity firm based in Berkeley, Calif., which also found a sharp rise in ransomware payments so far this year. Andrew Davis, Kivu's general counsel and risk officer, said in the report that his company observed "extremely high initial demands" this year and increasingly aggressive extortion tactics -- such as harassment of organizations' employees -- which might be a response to fewer victims opting to pay ransoms.
Clop on top
Chainalysis also found that larger, established ransomware gangs such as Clop and Black Basta, which are selective with their targets, were more active this year and "hitting bigger organizations for more money." The firm noted that Clop's average ransomware payment this year was $1,730,486, while the median payment was $1,946,335, which were by far the highest among the listed ransomware groups.
The Clop ransomware gang recently made headlines again with extortion attacks against organizations using Progress Software's MoveIt Transfer product. A threat actor associated with Clop exploited a zero-day vulnerability in MoveIt Transfer and breached dozens of customers over Memorial Day weekend, stealing confidential data without deploying ransomware. While Clop has named more than 250 victims on its data leak site, it's unclear how many victims have paid ransoms and for what amount.
The MoveIt Transfer attacks highlight another recent trend in the threat landscape where threat actors have opted to steal and extort sensitive data without deploying ransomware. Security vendors such as CrowdStrike observed a noticeable shift toward malware-free data theft attacks as attackers try to evade improved threat detection technologies and stronger enterprise security postures.
It's unclear how many attacks involving only data theft have earned extortion payments, as Chainalysis only tracked overall cryptocurrency payments to specific ransomware groups.
Rob Wright is a longtime technology reporter who lives in the Boston area.





