
Getty Images/iStockphoto
Bl00dy ransomware gang targets schools via PaperCut flaw
The Bl00dy ransomware gang is targeting schools via a critical remote code execution flaw present in unpatched instances of PaperCut MF and NG print management software.
A threat group identifying as the "Bl00dy" ransomware gang is targeting unpatched instances of PaperCut NG and PaperCut MF in the education sector, according to a Thursday joint security advisory from CISA and the FBI.
Print management software vendor PaperCut in March patched CVE-2023-27350, a critical remote code execution vulnerability affecting the vendor's MF and NG print management products. Unpatched servers began facing widespread exploitation last month. PaperCut said its first customer report of exploitation occurred on April 18, and Microsoft attributed some recent attacks to the Clop ransomware gang.
"PaperCut servers vulnerable to CVE-2023-27350 implement improper access controls in the SetupCompleted Java class, allowing malicious actors to bypass user authentication and access the server as an administrator," CISA's advisory read. "After accessing the server, actors can leverage existing PaperCut software features for remote code execution (RCE)."
According to PaperCut's page dedicated to CVE-2023-27350 and user account data flaw CVE-2023-27351, MF and NG versions 8.0.0 to 19.2.7, 20.0.0 to 20.1.6, 21.0.0 to 21.2.10 and 22.0.0 to 22.0.8 are vulnerable. The vendor urges customers to update their instances to a fixed version, which includes 20.1.7, 21.2.11, and 22.0.9 and later.
In addition to vulnerability and patch details, the support page includes workarounds -- focused on locking down network access to vulnerable servers -- as well as indicators of compromise.
Exploitation efforts have apparently escalated since the initial Clop attacks last month. CISA's joint security advisory detailed a ransomware campaign first detected in early May by a group self-identifying as the Bl00dy ransomware gang. CISA said the campaign is targeting the education facilities subsector, which the U.S. Department of Homeland Security defines as prekindergarten through 12th grade plus postsecondary school education facilities.
"Education Facilities Subsector entities maintained approximately 68% of exposed, but not necessarily vulnerable, U.S.-based PaperCut servers," the advisory read. "In early May 2023, according to FBI information, the Bl00dy Ransomware Gang gained access to victim networks across the Education Facilities Subsector where PaperCut servers vulnerable to CVE-2023-27350 were exposed to the internet. Ultimately, some of these operations led to data exfiltration and encryption of victim systems."
The education sector is a highly popular target for ransomware gangs -- even though schools rarely pay the ransom.
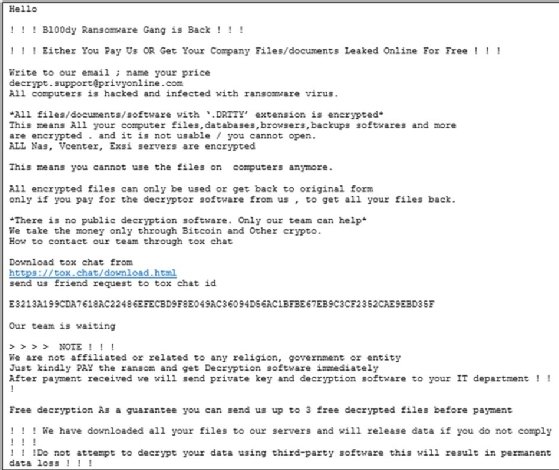
According to the advisory, Bl00dy used various tools such as legitimate remote management and maintenance software and command and control tools including Cobalt Strike Beacons, DiceLoader and TrueBot.
Additional technical information including rule-based detections is available in the advisory, though CISA warned that the detections might not be airtight against more advanced CVE-2023-27350 exploits because threat actors "are known to adapt exploits to circumvent rule-based detections formulated for the original iterations of exploits observed in the wild."
According to a blog post from threat intelligence vendor Cyble, Bl00dy emerged last July with the creation of a dedicated Telegram account. It began publishing victim data in August via Telegram, as opposed to dark web leak sites typically used by ransomware gangs. Cyble said the gang focuses on double-extortion attacks, meaning victims face both encryption and the threat of stolen data being published publicly.
PaperCut lead solutions architect David O'Hara told TechTarget Editorial in an email that the CISA advisory was "very well done" and the company is "currently focused on supporting our customers and making sure they have our full attention."
Alexander Culafi is a writer, journalist and podcaster based in Boston.







