
kras99 - stock.adobe.com
Coalition: Employee actions are driving cyber insurance claims
After analyzing cyber insurance claims data, Coalition determined that phishing escalated in 2022, ransomware dropped and timely patching remained a consistent problem.
A new study from a cyber insurance provider found that when it comes to organizations filing claims, the employees were usually to blame.
A recurring theme in Coalition's 2023 Cyber Claims Report Tuesday was the impact employee actions, such as clicking on malicious links, had on a business's cyber insurance claims. The insurer referred to such behavior as "the greatest contributing factor to organizations that experienced a cyber insurance claim," as it led to vulnerability patching failures and the continued use of end of life (EOL) technology that attackers increasingly exploited.
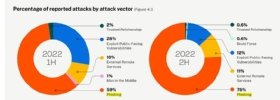
The technique that claimed the top attack vector further highlighted the problem. Phishing was the root cause for 76% of all Coalition claims reported in the second half of 2022, followed by the exploitation of public-facing vulnerabilities, which accounted for only 12% of claims.
Coalition partly attributed the increase in effective phishing attacks to AI tools.
"Phishing-related claims have spiked over the course of the year -- increasing 29% from H1 2022 -- as the rise of new technologies has made these attacks easier to execute. Threat actors have started leveraging AI tools to write credible phishing emails and translate the scams across multiple languages, giving them more time and cover to gain access to a network," Coalition wrote in the report.
Catherine Lyle, head of claims at Coalition, said phishing emerging as the top attack vector made sense -- it is a simple a way to get into a system. However, she is concerned the data represents a shift in the threat landscape for U.S.-based enterprises.
"In years past, it used to be a target-of-choice situation, where a company had the crown jewels and threat actors would say, 'I need to get in there to get the money.' Now what threat actors are saying is, 'Hey, look, we're going to send out an enormous number of phishing emails and whoever clicks on it, now they'll become the target of choice,'" Lyle said. "It doesn't matter if you're a nonprofit trying to cure cancer or if you're a school or if you're a million-dollar company. If your employee falls for a phishing scam, you become the target of choice."
Successful phishing led to funds transfer fraud (FTF) and business email compromise attacks. Coalition said both techniques saw a slight uptick year-over-year in 2022, with FTF attacks accounting for one third of Coalition claims, surpassing ransomware.
Ransomware decreased 54% year-over-year, which Coalition attributed as the greatest contributor to a drop in overall claims frequency last year. Claims frequency is defined by Coalition as the average number of claims per earned insurance policy. Coalition's report also showed the severity of claims decreased as well, with less-sophisticated cybercrimes growing in popularity.
Lyle said Russia's invasion of Ukraine was one contributing factor to the ransomware decrease, but the main driver for the drop was how involved ransomware attacks are. She described it as a much longer game compared to FTF, where attackers launch a phishing scam and wait in the victim's email account. Once the invoice arrives threat actors simply change it and give it to the victim with a new bank account.
Lyle said threat actors will also insert themselves in the conversation between the insured and the vendor who is seeking payment and change the vendor's invoice, so the insured pays the attacker instead.
"In the past, threat actors were in the system for 24 days, but they're now in there for 42 days. They're playing the longer game, and they're actually getting money. That's why FTF was so successful and out-seated ransomware," she said.
In its ransomware response role, Coalition advises enterprises to contact them before anyone else, including law enforcement. When Coalition did negotiate ransom payments in 2022, payments dropped an average of 27% from the initial demand. Lyle emphasized that companies with sufficient backups often refuse to give into attackers' demands. On the other hand, companies without good backups that fear an attack will limit its ability to function choose to negotiate.
Recent and increasing sanctions issued by the Treasury Department's Office of Foreign Assets Control against illicit cryptocurrency exchanges intended to deter payments have not been effective, she said.
While the OFAC list includes wallet addresses and a few ransomware variants, Lyle said it's not a big factor for a victim's payment decision. If Coalition sees attackers provided a wallet address for a sanctioned exchange, they will discuss it with their customer, but there are ways around it.
"You can make business exceptions as to why payment is needed. If the company is dead in the water and cannot function and will be out of business otherwise, we can work with the federal government to seek these kinds of exceptions to be able to help the company rebuild," she said.
Unfortunately, the drop in ransomware activity was short lived. Coalition observed an increase by the end of the second half of 2022 that continued into this year and is only getting worse.
"What they're doing now is they're going into healthcare entities and changing the medical records. Then they'll say, 'We're not going to tell you which medical records we've changed until you pay,'" she said.
Timely patching still a problem
Many of the issues that led to claims in 2022 were not new problems. Attackers continued to target unpatched, critical vulnerabilities and EOL software to gain system access. Policyholders that did not remediate critical flaws were 33% more likely to experience an attack or claim, according to the report.
"The majority of vulnerabilities in 2022 were exploited within the first 30 days of public disclosure, underscoring the importance of quick and consistent patching," the report read.
Additionally, companies were penalized for the use of certain technologies. In 2022, several critical Fortinet vulnerabilities that remained widely unpatched caused significant problems. Coalition provided a case study where despite its warning, a customer did not remediate the Fortinet flaw. That customer suffered a ransomware attack with a $1 million demand and eight days of business disruption.
"Consequently, organizations with exposed Fortinet devices experienced three times as many claims as those with no Fortinet devices," the report said.
The report also warned that SMBs running on-premises Microsoft Exchange servers were nearly twice as likely to experience a claim compared to those without it. The use of EOL software also posed continued problems, as companies that used such products in 2022 were three times more likely to experience a claim.
Lyle said smaller companies, non-profits and municipalities with tight budgets are the most frequent EOL software users. "It's costly for a company [to change technology], so they're not thinking, 'Oh, wait a minute, this is exposing me to three times more chance of getting hacked.' They're not thinking about that at all," she said.
The number one way to reduce policy costs, which are skyrocketing, is to focus on technology and hygiene. Lyle said implementing multifactor authentication, deploying Patch Tuesday fixes and protecting applications behind a firewall are all ways to drive down costs.






