
Getty Images/iStockphoto
Nokoyawa ransomware exploits Windows CLFS zero-day
The Nokoyawa ransomware attacks highlight the growing use of zero-day exploits by a variety of threat groups, including financially motivated cybercriminals.
Recent Nokoyawa ransomware attacks exploited a Windows zero-day vulnerability, marking a significant increase in sophistication levels among cybercriminal groups, according to Kaspersky Lab.
In a blog post on Tuesday, Boris Larin, lead security researcher at Kaspersky, detailed a campaign that leveraged a Windows Common Log File System (CLFS) driver elevation of privilege vulnerability, now tracked as CVE-2023-28252, to deploy Nokoyawa ransomware. The ransomware variant was first observed in February of 2022 and may be linked to Hive ransomware, according to multiple vendors.
While Microsoft fixed the CLFS flaw during the most recent Patch Tuesday update, Kaspersky emphasized how the activity represents an alarming evolution in zero-day attacks. Over the past two years, not only has zero-day activity spiked, but also threat actors' speed of exploit has increased as well.
Now a wider range of threat groups are exploiting zero-days in the wild.
"While the majority of zero-days we've discovered in the past were used by APTs, this particular zero-day was used by a sophisticated cybercrime group that carries out ransomware attacks," Larin wrote in the blog post.
Kaspersky researchers first observed the attacks against Windows CLFS in February against small and medium-sized businesses located in the Middle East, North America and Asia. CLFS is a log file system first introduced in 2003 that can be used by any application through an API, according to the blog.
Kaspersky reported the threat activity and zero-day vulnerability to Microsoft. Larin received partial credit for the discovery of CVE-2023-28252, along with Genwei Jiang at Mandiant and Quan Jin with DBAPPSecurity Company's WeBin Lab.
Labeled as an out-of-bounds write vulnerability, researchers discovered that CVE-2023-28252 can be exploited when the system attempts to extend the metadata block. While Kaspersky did not share additional details on how to exploit the vulnerability to provide enterprises with sufficient time to patch, the blog noted the CLFS technology is "quite complicated." But it's not the first time a Windows CLFS driver elevation of privilege vulnerability was reported.
Kaspersky found at least 32 other flaws discovered since 2018, including three detected in the wild as zero-days. Although the new vulnerability was like the previous ones, it doesn't appear to be a root cause issue but rather a problem with the overall design, Larin told TechTarget Editorial via email.
"Most often it's the case with code that was developed a long time ago and does complicate things. This is also the case [with] the CLFS driver," Larin said.
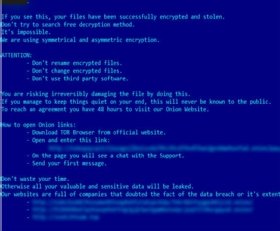
Like many ransomware attacks, the recent CLFS exploits used Cobalt Strike in the attacks. Subsequently, the group attempted to deploy Nokoyawa ransomware as a final payload. However, Kaspersky researchers noted differences between the CLFS attacks and past activity attributed to the same actor.
"In this attack, cybercriminals used a newer version of Nokoyawa that is quite distinct from the JSWorm codebase. It's written in C and has encrypted strings. It was launched with an encrypted json config provided with a "-config" command line argument," the blog read.
The biggest takeaway noted in the blog is the "significantly increasing level of sophistication among cybercriminals." Resources and access to zero-days are expanding to include APTs, as well as financially motivated groups. Previously, it was infrequent for even APTs to use zero-day exploits, but now Kaspersky has observed it "routinely" used in attacks by financially motivated groups as well.
"Moreover, there are developers willing to help cybercriminal groups and to produce one exploit after another," the blog post read.
Larin said developing zero-day exploits and using them in attacks requires completely different skills. Therefore, Kaspersky believes different people may have discovered the flaw than the Nokoyawa group actors that exploited it.
"But the fact that we have seen at least five different exploits that were likely developed by the same exploit author and have been used by that group since at least June 2022 makes us think that ransomware operators are working in fairly close collaboration with the exploit developer," Borin said.
In Microsoft's Patch Tuesday update, the vendor warned successful exploitation of CVE-2023-28252 could allow attackers to gain system privileges, so patching is important as exploitation remains ongoing.






